Posts
2836Following
682Followers
1507Kevin Beaumont
GossiTheDog@cyberplace.socialReally big scoop (I don't think @briankrebs knows how big yet) here - he's tracked down somebody who says they are Rey from Lapsus$.
I don't wanna say why yet as I don't have all the pieces of the jigsaw, but I imagine this is going to turn into a long thread over time.
https://krebsonsecurity.com/2025/11/meet-rey-the-admin-of-scattered-lapsus-hunters/
well strlen() returns the amount of bytes so in this regard multibyte characters are not really an issue per see.
https://gitlab.gnome.org/GNOME/glib/-/blob/f28340ee62c655487972ad3c632d231ee098fb7f/glib/gconvert.c#L1318 defines a char array of acceptable (meaning ASCII) characters.
Then it iterates over the dynamically allocated buffer and keeps track of the amount of "unacceptable" characters.
unacceptable was a gint (https://docs.gtk.org/glib/types.html#gint) which could therefore overflow.
To me it does look like glib could use some refactoring.
https://gitlab.gnome.org/GNOME/glib/-/commit/f28340ee62c655487972ad3c632d231ee098fb7f
buherator
buheratorAll this because some genius thought that preventing me from searching my own stuff will prevent online harassment.
#Akkoma #Mastodon #search
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20240521-00/?p=109786
cR0w h0 h0
cR0w@infosec.exchangeNeat vuln in Fail2Ban.
https://gist.github.com/R-Security/1c707a08f9c7f9a91d9d84b5010aaed2
Fail2Ban 0.11.2 contains a vulnerability that allows an attacker with the ability to influence logged input (e.g., authentication logs, service logs processed by Fail2Ban filters) to inject specially crafted patterns that lead to command execution within the Fail2Ban action processing pipeline.
Because Fail2Ban actions typically run with root privileges, this can result in privilege escalation, allowing an attacker to execute commands with elevated permissions.
The issue arises from insufficient sanitization of variables passed into action scripts under certain configurations, allowing malicious input to propagate into shell execution.
cR0w h0 h0
cR0w@infosec.exchangeThat's an avenue that I admit I hadn't thought to check before. Seems so simple though.
https://access.redhat.com/security/cve/CVE-2025-13601
A heap-based buffer overflow problem was found in glib through an incorrect calculation of buffer size in the g_escape_uri_string() function. If the string to escape contains a very large number of unacceptable characters (which would need escaping), the calculation of the length of the escaped string could overflow, leading to a potential write off the end of the newly allocated string.
jiska 🦄
jiska@chaos.social
Using a Pixel with GrapheneOS that features Inactivity Reboot, MTE, and more? — You must be a drug dealer. 🚨
Using an iPhone 17, which now also ships with EMTE, Inactivity Reboot, SPTM, TXM, Conclaves, ...? — Oh, just the average Apple fangirl/boy who gets a new device every year due to camera improvements. ✅
GrapheneOS released some innovative mitigations prior to Apple. Yet, it needs Big Tech to apply such ideas and make phones more secure at scale.
Simple Sabotage Field Manual
simple_sabotage@mastodon.socialAbstract verbalizations about personal liberty, freedom of the press, and so on, will not be convincing in most parts of the world.
Martin Owens 
doctormo@floss.social
Has anyone ever heard of a phono jack connection detection that works in windows with headphones and a sound system, but only works in linux in the headphones?
This issue breaks my understanding of how phono detection works. How the operating system would have any way to distinguish between the two. And it sounds like some physical weirdness.
Anyone else seen anything like this? Please boost.
The Seven Voyages Of Steve
sinbad@mastodon.gamedev.placeAll human-authored art, regardless of quality, is vastly superior to soulless AI remixes.
Using AI art just sends a message that filling a space with *anything* is all that matters. How can you expect people to care about anything else you have to offer once they know that?
Frederik Braun �
freddy@security.plumbingHello from Düsseldorf. I am at German OWASP day and you can follow along too. There’s a live stream on https://media.ccc.de/.
Full program at https://god.owasp.de/2025/
Talks are about all sorts of appsec things, from langsec over pdf to passkeys and so on. All talks will be recorded :)
Joanna Holman
joannaholman@aus.socialCame across this striking art piece in Bourke St Mall, #melbourne called Paid Attention by Huei Yin Wong. It’s designed to comment on the way the advertising industry profits from constantly taking our attention at no benefit to us. If you sit making unbroken eye contact with the messages about our attention choices on the screen, it pays out the equivalent of minimum wage for the time watched. Sitting there conspicuously staring at something silly in public for even less than 2 minutes was weirdly unsettling even though we’re constantly looking at silly stuff on screens
/r/netsec
_r_netsec@infosec.exchangeWe made a new tool, QuicDraw(H3), because HTTP/3 race condition testing is currently trash. https://www.cyberark.com/resources/threat-research-blog/racing-and-fuzzing-http-3-open-sourcing-quicdraw
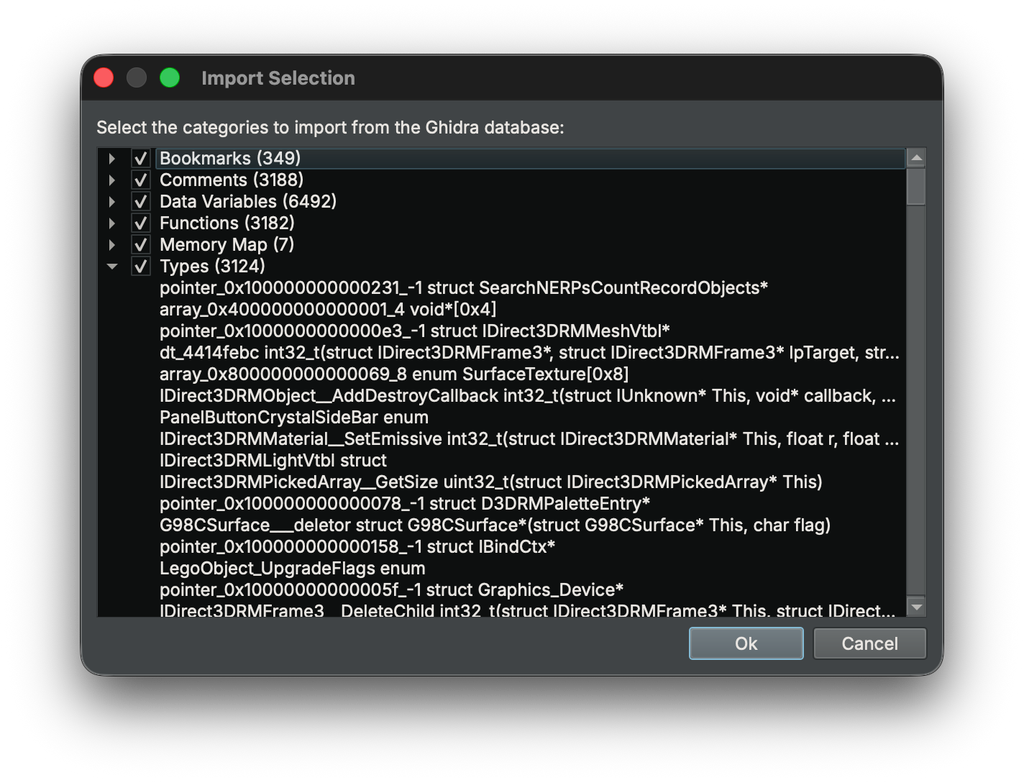
Binary Ninja
binaryninja@infosec.exchangeYou can now pull Ghidra databases straight into your workflow in Binary Ninja 5.2! Open a .gbf on its own, import Ghidra data into an existing session, or bring parts of a full project into a Binary Ninja project on Commercial and above. Mixed tool workflows get a lot easier and this update sets the stage for future export support. https://binary.ninja/2025/11/13/binary-ninja-5.2-io.html#ghidra-import