Posts
2754Following
681Followers
1504abadidea
0xabad1dea@infosec.exchangeSomeone asked me to hand-translate a publicly posted Chinese technical report about NSA shenanigans on the Chinese Center for Time-Keeping network. It took me a while, because it turns out translating technical corporatese from your third language is very hard when chronically sleep deprived, but it is done.
https://docs.google.com/document/d/1gk1fDLKrN3m5jOSk7QbpGL1SBcLvrm0FTN3H-5ZJZcY/edit?usp=sharing
buherator
buheratorhttps://research.checkpoint.com/2025/microsoft-teams-impersonation-and-spoofing-vulnerabilities-exposed/
CFG Bot 🤖
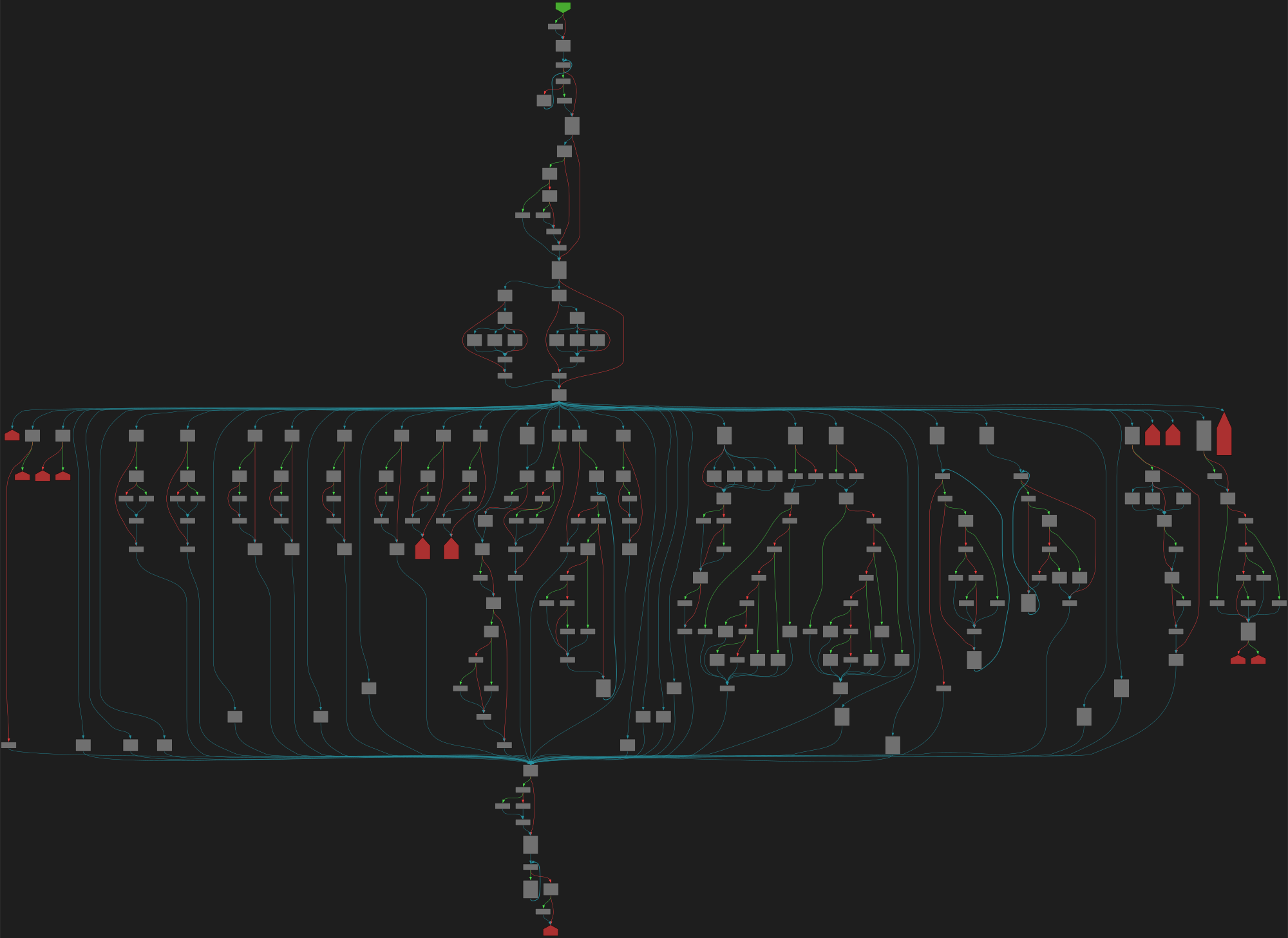
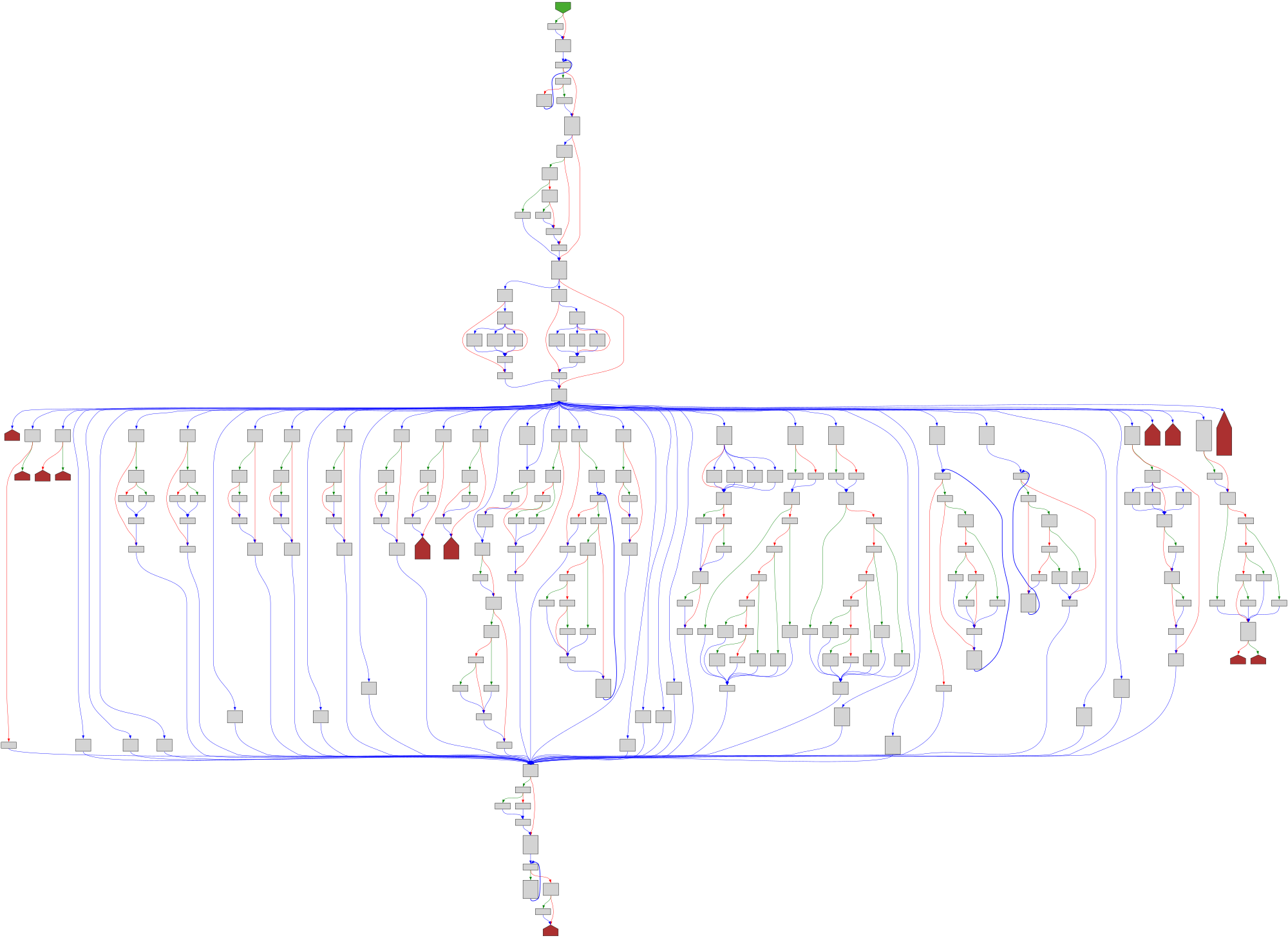
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
File: src/cmd/vendor/golang.org/x/arch/arm64/arm64asm/plan9x.go:24 https://github.com/golang/go/blob/6425749695130f2032ac9cfdf5407b6a322534db/src/cmd/vendor/golang.org/x/arch/arm64/arm64asm/plan9x.go#L24
func GoSyntax(inst Inst, pc uint64, symname func(uint64) (string, uint64), text io.ReaderAt) string
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2F6425749695130f2032ac9cfdf5407b6a322534db%2Fsrc%2Fcmd%2Fvendor%2Fgolang.org%2Fx%2Farch%2Farm64%2Farm64asm%2Fplan9x.go%23L24&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2F6425749695130f2032ac9cfdf5407b6a322534db%2Fsrc%2Fcmd%2Fvendor%2Fgolang.org%2Fx%2Farch%2Farm64%2Farm64asm%2Fplan9x.go%23L24&colors=light
Dave Townsend
Mossop@fosstodon.orgThis is possibly my favourite bug in Firefox right now. Unfortunately it looks like it is about to be fixed.
buherator
buheratorhttps://blog.talosintelligence.com/trufflehog-fade-in-and-bsafe-crypto-c-vulnerabilities/
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchange🚨 New advisory was just published! 🚨
A vulnerability in the Windows Cloud File API allows attackers to bypass a previous patch and regain arbitrary file write, which can be used to achieve local privilege escalation.
This vulnerability was disclosed during our TyphoonPWN 2025 Windows Category and won first place: https://ssd-disclosure.com/cloud-filter-arbitrary-file-creation-eop-patch-bypass-lpe/
Registration for TyphoonPWN 2026 is already open: https://typhooncon.com/typhoonpwn-2026/
cynicalsecurity 
cynicalsecurity@bsd.network
Does anyone know how we can pull a malicious domain which, genially, is usable for multiple #scams?
private-eu[.]com - LIVE domain - #malware
is being used to generate URLS such as "bankname[.]private-eu[.]com" so that they fly below the radar of the "new domain" watches.
Boost for visibility is appreciated.
Josh Bressers
joshbressers@infosec.exchangeI started using @kagihq as my search engine
The biggest surprise has been how jarring seeing a search page that isn't full of shit
I didn't realize my brain has come to expect a page of garbage when I search for things, and it doesn't know what to do now
Dare Obasanjo
carnage4life@mas.toInvestors woke up this morning and decided we’re in an AI bubble after all. Palantir beat expectations and posted upbeat guidance but is down -8% and Nvidia down -4% after Michael Burry disclosed put options with a notional value of about $187 million against Nvidia and $912 million against Palantir.
The market decided if he’s willing to bet $1B+ that we’re in a bubble then he might be onto something.
Space Rogue
spacerog@mastodon.socialI've decided to stop pussy footing around and I am now openly looking for my next challenge.
Interested in a company on the small to mid-size range with a cool story. Ideal position would be a combination of customer outreach, marketing and thought leadership. What ya got? #CyberSecurity
FOR IMMEDIATE RELEASE: exploits.forsale's statement on the arrest of Peter Williams
buherator
buherator- Fixing bugs in Gradle scripts
- Resolving systemd and Network Manager fights
I see a pattern emerging!
buherator
buheratorhttps://jfrog.com/blog/CVE-2025-11953-critical-react-native-community-cli-vulnerability
"The Metro development server [..] binds to external interfaces by default [...] The server%27s /open-url endpoint handles a POST request that includes a user-input value that is passed to the unsafe open() function provided by the open NPM package, which will cause OS command execution."
Adam Caudill
adam_caudill@infosec.exchangeRandomly Scheduled Reminder: You should use a tool like Loqseq or Obsidian to keep notes and a journal of your life, work, and what you're doing. Future you will thank you. Having those details handy and searchable comes in handy in so many ways.
My approach: https://adamcaudill.com/2022/06/05/logseq-my-external-brain/
Lorenzo Franceschi-Bicchierai
lorenzofb@infosec.exchangeNEW: This is how former L3Harris Trenchant boss Peter Williams was able to steal zero-days worth millions of dollars and sell them to a Russian broker, based on court documents and interviews with his former colleagues.
A former Trenchant employee told me that “no one had any supervision over [Williams] at all. He was kind of allowed to do things the way he wanted to.”
“He was, in my opinion, perceived to be beyond reproach,” the former employee, who has knowledge of Trenchant's IT systems, told me.
Kevin Beaumont
GossiTheDog@cyberplace.socialNew by me - CyberSlop, where I look at orgs misusing GenAI fears to take from their own customers.
First threat actor - MIT and Safe Security go full cyberslop.
https://doublepulsar.com/cyberslop-meet-the-new-threat-actor-mit-and-safe-security-d250d19d02a4
Nina Kalinina
nina_kali_nina@tech.lgbtI love reverse-engineering because it allows me to dismantle structures of control.
Blacktop
blacktop__@bird.makeupFirst attempt at building macOS 26.0 XNU as a LIBRARY?! 👩🔬
Check it out! 🎉
https://github.com/blacktop/darwin-xnu-build/releases/download/v26.0/xnu-lib-26.0.tar.gz