Posts
2711Following
681Followers
1505Project Zero Bot
p0botDolby Unified Decoder: Out of bounds write in evolution parsing
https://project-zero.issues.chromium.org/issues/428075495
CVE-2025-54957
Brad Spengler
spendergrsec@bird.makeupThese kinds of issues are more common than people would expect. I remember running tcpdump in 2003 and seeing some obvious kernel data being leaked over the network. Similar to the coredump case, it's there but nobody really looks:
https://bird.makeup/users/grsecurity/statuses/1252558055629299712
/r/netsec
_r_netsec@infosec.exchangeHow I Reversed Amazon's Kindle Web Obfuscation Because Their App Sucked https://blog.pixelmelt.dev/kindle-web-drm/
OOC: Honestly, just read this guy's explanation. It's way better than mine: https://paulkedrosky.com/weekend-reading-plus-spvs-meta-and-fiber-buildout-2-0/
codecolorist
codecolorist@infosec.exchangeMy OBTS v8 slides for Apple Compressor (part of Final Cut Pro) unauthenticated LAN RCE. No CVE? Because it’s not patched…🫣
buherator
buheratorhttps://research.checkpoint.com/2025/denial-of-fuzzing-rust-in-the-windows-kernel/
buherator
buheratorbuherator
buheratorThis is an old article, but this one sentence explains so many things!
https://dzone.com/articles/why-you-should-avoid-jsf
buherator
buheratorhttps://blog.exploits.club/exploits-club-weekly-newsletter-89-ios-gpu-driver-bugs-kernel-stack-uafs-hardware-wallet-auth-bypasses-and-more/
Costin Raiu
craiu@bird.makeupSo this October 2025 F5 security notification is pretty wild because of the sheer volume of vulnerabilities disclosed: more than 30 high-severity CVEs (!) and around a dozen medium-severity ones in a single release cycle. This affects almost every F5 product family, BIG-IP (all modules), BIG-IP Next, F5OS, and related components. Something we don’t see very often... and a lot of these vulnerabilities score above 8.0; remote exploitation, denial-of-service or privilege escalation. Also, the number of affected software branches (from 15.x through 17.x) means most F5 deployments are touched in some way. YMMV.
In short, this quarter’s bulletin is probably F5’s heaviest security updates ever. If you run F5 products, patch now. https://my.f5.com/manage/s/article/K000156572
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20251014-00/?p=111681
/r/netsec
_r_netsec@infosec.exchangeyIKEs (WatchGuard Fireware OS IKEv2 Out-of-Bounds Write CVE-2025-9242) - watchTowr Labs https://labs.watchtowr.com/yikes-watchguard-fireware-os-ikev2-out-of-bounds-write-cve-2025-9242/
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@eupolicy.socialWith the AI-bubble looking close to bursting, here I present a pre-mortem, in which I state that much of AI is simultaneously mega-impressive and still mostly useless. The collapse of the bubble does not mean the technology will go away, however. Also, there are extremely useful AI applications already that we should not lose sight of once we are post-collapse. Plus some thoughts on 'intelligence' & evolution:
https://berthub.eu/articles/posts/an-ai-premortem/
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchangeEver wondered how virtual machines talk to their host without relying on traditional networking?
Meet vsock (Virtual Socket) - the Linux kernel’s built-in communication layer for blazing-fast, low-latency host ↔ guest interaction.
Unlike TCP/IP, vsock skips the network stack entirely and works directly over the hypervisor, making it perfect for control channels, telemetry, and secure VM management in QEMU/KVM, VMware, and Hyper-V environments.
Read our full technical breakdown: https://ssd-disclosure.com/an-introduction-to-chrome-exploitation-webassembly-edition-2/
buherator
buheratorhttps://www.preludesecurity.com/blog/windows-arm64-internals-deconstructing-pointer-authentication
buherator
buheratorhttps://blog.dfsec.com/ios/2025/10/14/Depicting-an-iOS-Vulnerability/
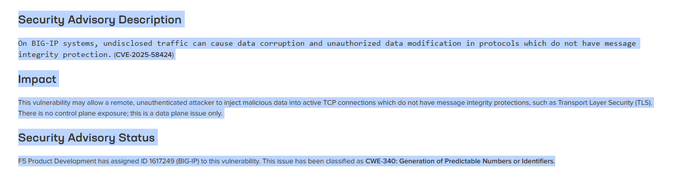
4Dgifts
4Dgifts@mastodon.socialIn the year of Our Lord Two Thousand and Twenty-Five, BIG-IP devices from F5 Inc. are vulnerable to TCP hijacking due to use of a bad TCP Initial Sequence Number generator.