Posts
2711Following
681Followers
1505buherator
buheratorhttp://blog.quarkslab.com/nvidia_gpu_kernel_vmalloc_exploit.html
Brian Greenberg 
brian_greenberg@infosec.exchange
Hackers can steal 2FA codes and private messages from Android phones. The "Pixnapping" attack is a really clever piece of research. It shows that the theoretical wall between apps on your phone isn't as solid as we'd like to believe. By exploiting a GPU side channel, a malicious app with zero permissions can effectively screenshot other apps, one pixel at a time. It's a reminder that security is a stack, and a vulnerability at the hardware level can undermine everything built on top of it.
TL;DR
👾 A new attack called "Pixnapping" can read visual data from other apps on Android devices.
🔑 It exploits a GPU side-channel leak to steal sensitive info like 2FA codes and messages, pixel by pixel.
⚠️ The scary part: the malicious app required for the attack needs zero special permissions to be granted.
🧠 While complex to pull off, this is a serious proof of concept that challenges the core idea of OS app sandboxing.
https://arstechnica.com/security/2025/10/no-fix-yet-for-attack-that-lets-hackers-pluck-2fa-codes-from-android-phones/
#Android #Cybersecurity #SideChannelAttack #2FA #security #privacy #cloud #infosec
Julia Evans
b0rk@jvns.caTERM
https://wizardzines.com/comics/term/
(from The Secret Rules of the Terminal, out now! https://wizardzines.com/zines/terminal)
stf
stf@chaos.social\m/ dnet just released v0.6 of androsphinx, a v2.0 compatible #android client for the #sphinx #passwordmanager! \o/
you ask, wtf sphinx? check out: https://sphinx.pm
get the android client here: https://github.com/dnet/androsphinx/releases/tag/v0.6
buherator
buheratorhttps://arxiv.org/pdf/2510.09272
#fromTwitter
Haifei Li
haifeili@bird.makeupThe end of an era.
If you don’t know what Tavis (and the P0) has contributed to and changed the vulnerability research community, let me give you just an example: if not because of Tavis and P0, we’d be still waiting 6 or 12 months to get a Windows or Office bug patched.
https://bird.makeup/users/taviso/statuses/1976724463103426860
HN Security
hnsec@infosec.exchangeWe've just published "Streamlining Vulnerability Research with the idalib Rust Bindings for IDA 9.2" by @raptor, now live on our freshly restyled blog:
Originally featured last week as a guest post on the @HexRaysSA blog, this article shows how Marco's headless #IDA plugins written in #Rust can be used to scale up #vulnerability research and uncover real-world security issues efficiently.
If you’re into reverse engineering, automation, or vulnerability discovery, this one's a must-read! 💻 🦀
Clément Labro
itm4n@infosec.exchangeA nice and short blog post about blinding EDR with WFP by my colleague Florian.
"Blinding EDRs: A deep dive into WFP manipulation"
https://blog.scrt.ch/2025/08/25/blinding-edrs-a-deep-dive-into-wfp-manipulation/
LaurieWired
lauriewired@bird.makeupThis is fundamentally the problem with how C++ is currently taught.
The best way to “unlearn” a negative C++ bias, especially for students, is to look at how Modern C++ is actually done.
Every year, CppCon has a “Back to Basics” Track, which they also upload to youtube. I highly recommend all of them.
Instead of being constrained to “old school” CS teaching logic, it’s a demonstration of fuller, modern capabilities.
buherator
buheratorhttps://microsoftedge.github.io/edgevr/posts/Changes-to-Internet-Explorer-Mode-in-Microsoft-Edge/
CFG Bot 🤖
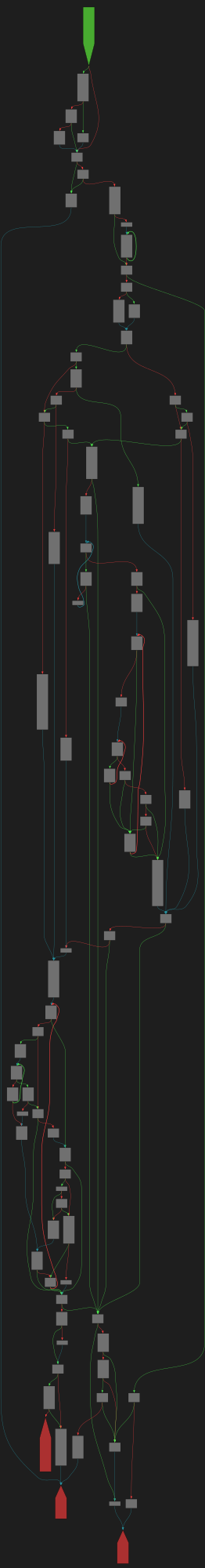
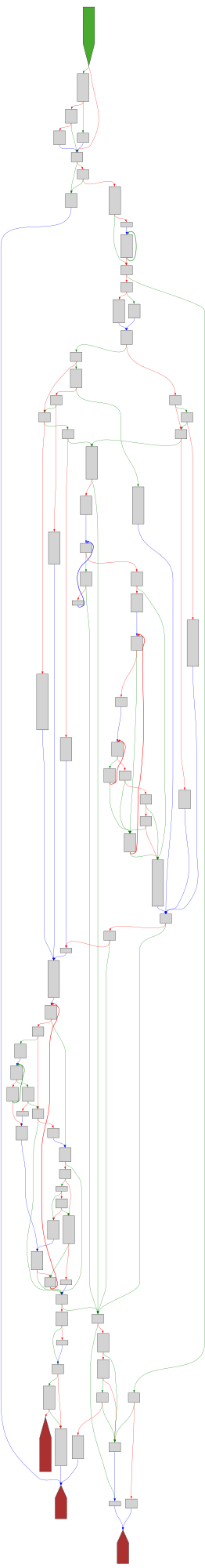
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 00867b00
____strtol_l_internal
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00867b00.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00867b00.json&colors=light
buherator
buheratorRon Bowes
iagox86@infosec.exchangeRE: https://infosec.exchange/@BleepingComputer/115367382398075001
Another one??
daniel:// stenberg://
bagder@mastodon.socialA new breed of analyzers.
And they use AI.
https://daniel.haxx.se/blog/2025/10/10/a-new-breed-of-analyzers/