Posts
2763Following
681Followers
1504HN Security
hnsec@infosec.exchangeWe've just published "Streamlining Vulnerability Research with the idalib Rust Bindings for IDA 9.2" by @raptor, now live on our freshly restyled blog:
Originally featured last week as a guest post on the @HexRaysSA blog, this article shows how Marco's headless #IDA plugins written in #Rust can be used to scale up #vulnerability research and uncover real-world security issues efficiently.
If you’re into reverse engineering, automation, or vulnerability discovery, this one's a must-read! 💻 🦀
Clément Labro
itm4n@infosec.exchangeA nice and short blog post about blinding EDR with WFP by my colleague Florian.
"Blinding EDRs: A deep dive into WFP manipulation"
https://blog.scrt.ch/2025/08/25/blinding-edrs-a-deep-dive-into-wfp-manipulation/
LaurieWired
lauriewired@bird.makeupThis is fundamentally the problem with how C++ is currently taught.
The best way to “unlearn” a negative C++ bias, especially for students, is to look at how Modern C++ is actually done.
Every year, CppCon has a “Back to Basics” Track, which they also upload to youtube. I highly recommend all of them.
Instead of being constrained to “old school” CS teaching logic, it’s a demonstration of fuller, modern capabilities.
buherator
buheratorhttps://microsoftedge.github.io/edgevr/posts/Changes-to-Internet-Explorer-Mode-in-Microsoft-Edge/
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 00867b00
____strtol_l_internal
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00867b00.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00867b00.json&colors=light
buherator
buheratorRon Bowes
iagox86@infosec.exchangeRE: https://infosec.exchange/@BleepingComputer/115367382398075001
Another one??
daniel:// stenberg://
bagder@mastodon.socialA new breed of analyzers.
And they use AI.
https://daniel.haxx.se/blog/2025/10/10/a-new-breed-of-analyzers/
Frida
fridadotre@fosstodon.orgFrida 17.4 introduces Simmy, a new backend for Apple’s Simulators on macOS.
Spawn, attach, and instrument apps — just like on a real device. #ios #reverseengineering
daniel:// stenberg://
bagder@mastodon.socialIf you're curious, here are 158 of Joshua's reported issues on #curl to give you an idea what we talk about.
We have manually gone trough them all and dismissed or addressed them. None of them has been deemed a security problem. Not all the PRs for the valid problems have been merged yet.
https://gist.github.com/bagder/d1fff7f0471fbbe71354048a282e098e
Saar Amar
amarsaar@infosec.exchangeIt took four years, but now there is spec for lock files https://snarky.ca/why-it-took-4-years-to-get-a-lock-files-specification/
buherator
buheratorhttps://github.com/LvStrnggg/zkm-flow
buherator
buheratorhttps://spaceraccoon.dev/nokia-beacon-router-uart-command-injection/
postcardware.net
postcardware@cyber.msSent from Los Gatos, California, U.S.A. on July 16, 1995. https://postcardware.net/?id=36-67
buherator
buheratorThe Hacker‘s Choice
thc@infosec.exchangeINTERVIEW of "MB" WhereWarlocksStayUpLate:
https://wherewarlocksstayuplate.com/interview/mohammed-bagha/
You have inspired many. We are fans:⚡️🌊🎠
https://wherewarlocksstayuplate.com/interview/mohammed-bagha/
Learn Turbo Pascal - a video series originally released on VHS
pancake 
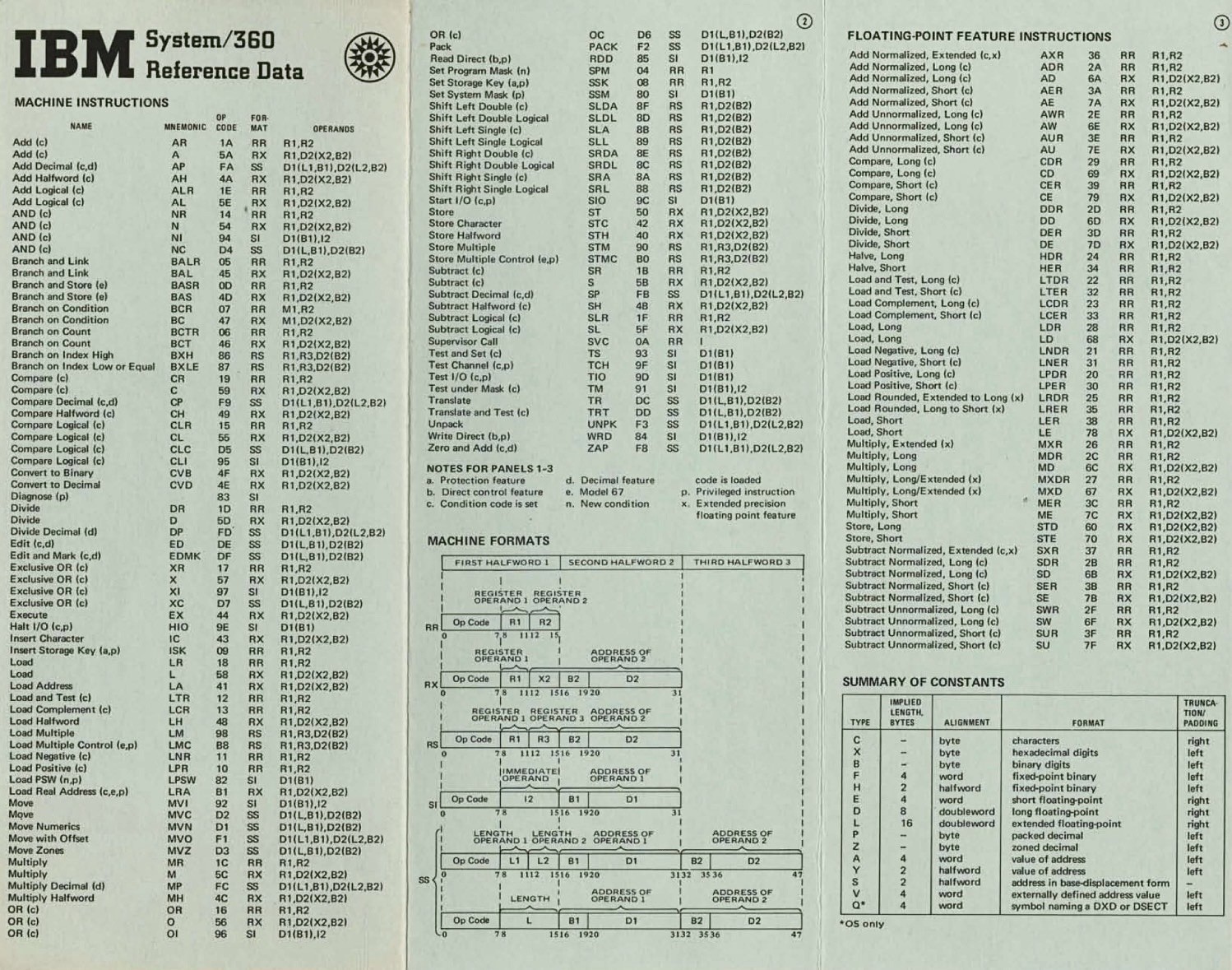
pancake@infosec.exchange
The IBM System/360 machine instructions reference card #s360 #assembly #mainframe https://archive.computerhistory.org/resources/access/text/2010/05/102678081-05-01-acc.pdf