Posts
2789Following
681Followers
1505The Hacker‘s Choice
thc@infosec.exchangeINTERVIEW of "MB" WhereWarlocksStayUpLate:
https://wherewarlocksstayuplate.com/interview/mohammed-bagha/
You have inspired many. We are fans:⚡️🌊🎠
https://wherewarlocksstayuplate.com/interview/mohammed-bagha/
Learn Turbo Pascal - a video series originally released on VHS
pancake 
pancake@infosec.exchange
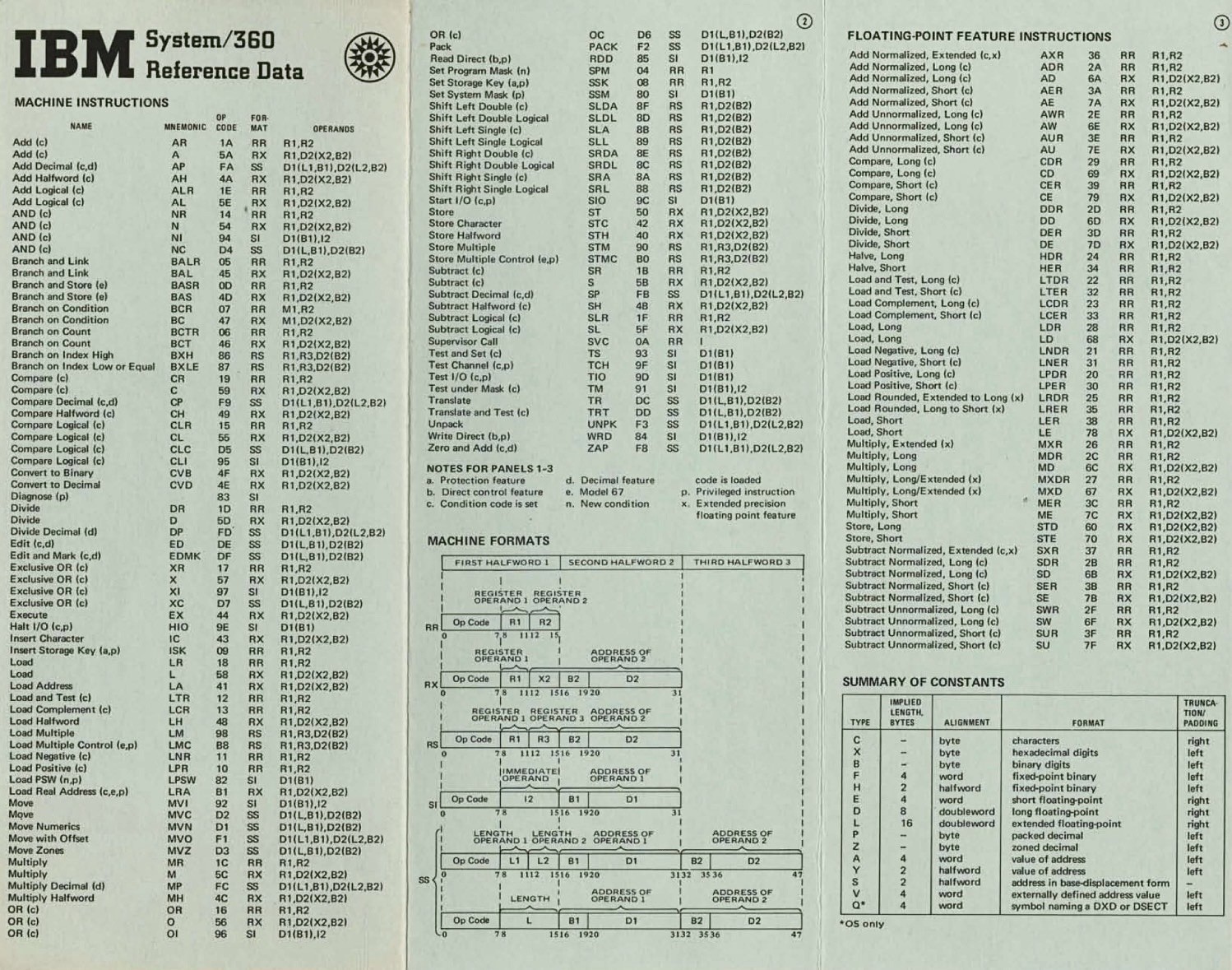
The IBM System/360 machine instructions reference card #s360 #assembly #mainframe https://archive.computerhistory.org/resources/access/text/2010/05/102678081-05-01-acc.pdf
buherator
buheratorI think this is a reasonable stance. What I do find unreasonable are design choices that (sorry, example again) make people shovel down megabytes of code into a client-side VM to display black on white text. I don't think this would cross anyones mind 20y ago, and not only because perf constraints. But our thinking changed at some point.
[1] https://www.youtube.com/watch?v=6tu0mIpX8nU
Where Homes Get Weird
weirdestate@eigenmagic.netYes we are all normal here in HUMANSVILLE. We are all HUMANS of course. No need to check.
kriware 
kriware@infosec.exchange
The Debugging Book
Interactive guide exploring automated debugging, testing, and program repair with Python examples for researchers and developers.
Piotr Bazydło
chudypb@infosec.exchangeFun times with Telerik UI and DoS by default (it will hit for a long time I think). Sometimes it may lead to more fun, like RCE :)
Gadgeting inspired by @pwntester Oleksandr and @stevenseeley
Blog:
buherator
buheratorhttps://momo5502.com/posts/2025-10-03-reverse-engineering-denuvo-in-hogwarts-legacy/
buherator
buheratorhttps://labs.infoguard.ch/posts/attacking_edr_part5_vulnerabilities_in_defender_for_endpoint_communication/
buherator
buheratorAny recommendations?
"You know, I couldn't do it. I couldn't reduce it to the freshman level. That means we really don't understand it." - Richard Feynman
hanno
hanno@mastodon.socialDear Infosec people who have looked at XML and XXE before: I am trying to get an understanding of Blind XXE.
Many of the descriptions I find are lacking an important detail which makes the attack much less practical. Blind XXE works by building an URL which contains content of a file, allowing to exfiltrate content. However, in all my tests, that *only* works if the file contains no newlines, as those are not allowed in URLs. Am I missing something?
🧵
hanno
hanno@mastodon.socialThat means the attack is only relevant if a) you have a file with a secret, but no newlines&other characters breaking an URL, b) you know the path.
That seems rather unlikely in practice.
It may be that there are implementations that will ignore that and still open the URL. Or that will auto-encode newlines. Or that there's some trick I don't know. But that's all speculation. If you know of any *working* scenario where exfiltration with newlines works, I'd be interested to hear about it.
Cure53 🏳️🌈
cure53@infosec.exchangeDOMPurify 3.3.0 will soon be released, with this likely being the most important change in a long time:
buherator
buheratorhttps://techtrenches.substack.com/p/the-great-software-quality-collapse
"We've normalized software catastrophes to the point where a Calculator leaking 32GB of RAM barely makes the news."
hackaday
hackaday@hackaday.social2025 Component Abuse Challenge: Load Cell Anemometer
https://hackaday.com/2025/10/09/2025-component-abuse-challenge-load-cell-anemometer/
quarkslab
quarkslab@infosec.exchangeFinding a buggy driver is one thing, abusing it is another🧠
In his latest blog post, Luis Casvella shows you how BYOVD can be used as a Reflective Rootkit Loader ! 🚀
➡️ https://blog.quarkslab.com/exploiting-lenovo-driver-cve-2025-8061_part2.html
Guillaume Endignoux
gendx@infosec.exchangeA few technical examples of when C++/Rust interop is complicated. #EuroRust
buherator
buheratorI just had to use one of my password cracking wordlists to figure out kiddos homework