Posts
2461Following
661Followers
1486Brambleminster Gollyhatch
gollyhatch@hachyderm.ioPro tip: if you're using @kagihq's video search instead of #YouTube's own search (which you should), you can customize your search results using the little shield icon next to each result just like with the regular search, except you don't block entire domains here but individual YouTube channels, allowing you to permanently ban trash/clickbait/AI channels from your results.
BOFH Excuses
bofh_excuses@gts.chapek9.com#BOFH excuse #404:
Sysadmin accidentally destroyed pager with a large hammer.
/r/netsec
_r_netsec@infosec.exchangeCVE-2025-53149: Heap-based buffer overflow in Windows Kernel Streaming https://www.crowdfense.com/cve-2025-53149-windows-ksthunk-heap-overflow/
Trail of Bits
trailofbits@infosec.exchangeWe built local backdoors for Signal, 1Password & Slack through V8 heap snapshot tampering (CVE-2025-55305).
Method: Replace v8_context_snapshot.bin files with versions that override JavaScript builtins. When apps call Array.isArray(), malicious code executes.
Works because integrity checks ignore these "non-executable" files that actually contain executable JavaScript.
Impact: Nearly every Chromium-based app is vulnerable.
https://blog.trailofbits.com/2025/09/03/subverting-code-integrity-checks-to-locally-backdoor-signal-1password-slack-and-more/
buherator
buheratorhttps://blog.silentsignal.eu/2025/09/04/Exploit-development-for-IBM-i/
Another one from my old partners in crime, incl. exploit for CVE-2023-30990 #IBMi
Sylvhem
Sylvhem@eldritch.cafeAlright Fedi. This is going to be my more far fetched question as of yet.
Do any of you happens to have, lying in a box somewhere, a Photo CD? And if so, would you be willing to part with it?
Just to clear any possible confusion, I’m specifically looking for a disc in the Photo CD format, not a CD-R on which pictures have been stored as files. Here is the article on the subject: https://en.wikipedia.org/wiki/Photo_CD.
Boosts are appreciated, as my search has not been fruitful this far.
buherator
buheratorhttps://u1f383.github.io/linux/2025/09/03/analysis-of-CVE-2025-37756-an-uaf-vulnerability-in-linux-ktls.html
buherator
buheratorhttps://slcyber.io/assetnote-security-research-center/secondary-context-path-traversal-in-omnissa-workspace-one-uem/
meowray
meowray@hachyderm.ioAfter a decade of neglect, ELF object file specification is being maintained again
https://groups.google.com/g/generic-abi/c/doY6WIIPqhU Updated my notes https://maskray.me/blog/2024-01-14-exploring-object-file-formats
Cary is maintaining both DWARF and ELF :)
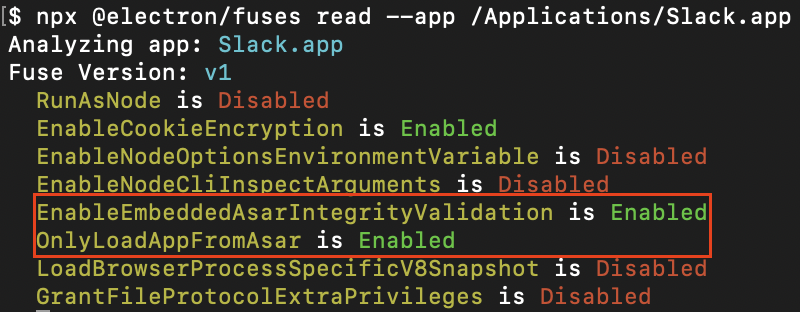
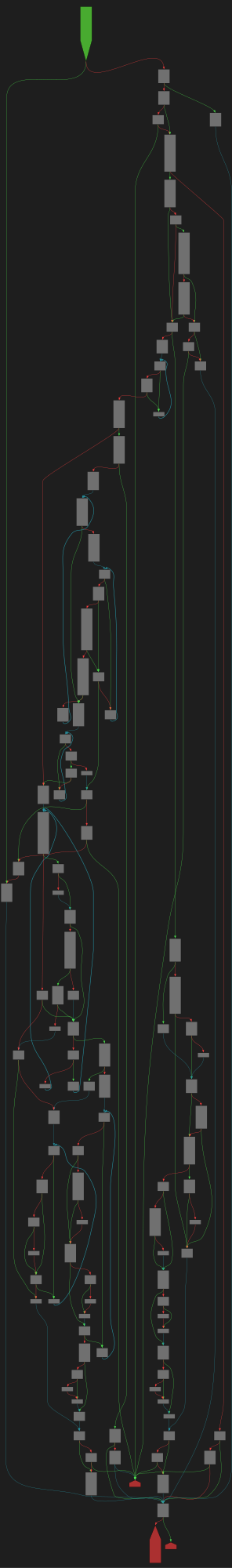
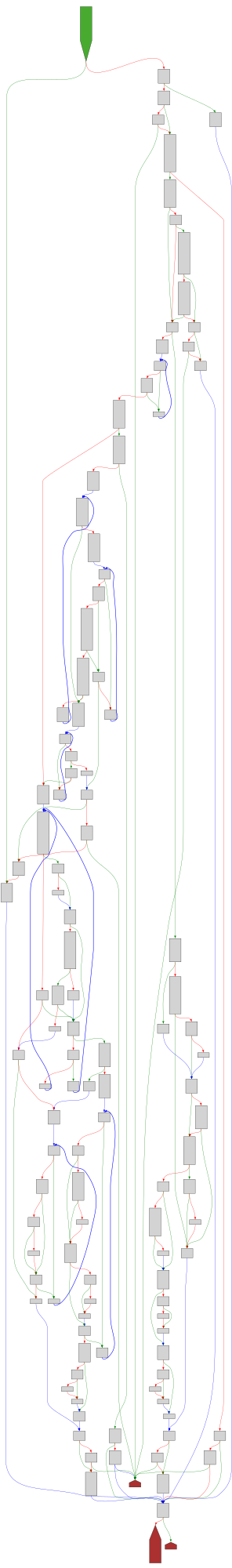
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 008ff630
setlocale
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F008ff630.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F008ff630.json&colors=light
Doyensec
doyensec@infosec.exchange📢 It's here! Part two of Norbert Szetei's (@sine) research into ksmbd. See how customized fuzzing & selecting the right sanitizers led to discovering 23 Linux kernel CVEs, including use-after-frees & out-of-bounds reads/writes.
https://blog.doyensec.com/2025/09/02/ksmbd-2.html
#doyensec #appsec #security #fuzzing
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250902-00/?p=111544
buherator
buheratorhttps://swarm.ptsecurity.com/kernel-hack-drill-and-a-new-approach-to-exploiting-cve-2024-50264-in-the-linux-kernel/