Posts
2589Following
669Followers
1495Doyensec
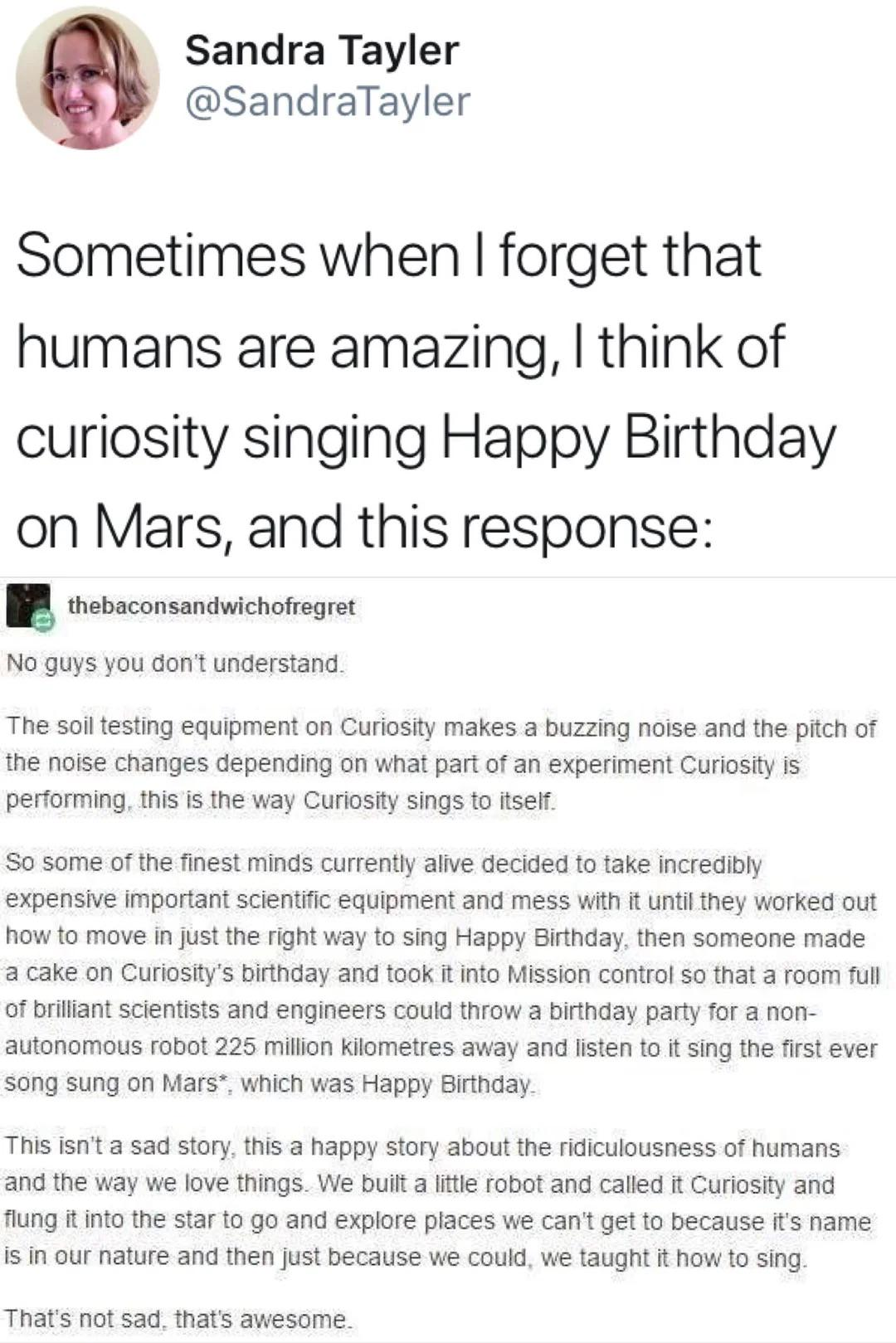
doyensec@infosec.exchange📢 It's here! Part two of Norbert Szetei's (@sine) research into ksmbd. See how customized fuzzing & selecting the right sanitizers led to discovering 23 Linux kernel CVEs, including use-after-frees & out-of-bounds reads/writes.
https://blog.doyensec.com/2025/09/02/ksmbd-2.html
#doyensec #appsec #security #fuzzing
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250902-00/?p=111544
buherator
buheratorhttps://swarm.ptsecurity.com/kernel-hack-drill-and-a-new-approach-to-exploiting-cve-2024-50264-in-the-linux-kernel/
buherator
buheratorbuherator
buheratorPeter Kröner
sir_pepe@mastodon.social🤯🚨 BREAKING NEWS 🚨🤯
In a shocking development, new additions to the #ECMAScript standard WILL UNLEASH THE HERETOFORE UNAVAILABLE POWER OF ADDITION _IN JAVASCRIPT_ upon the world!
👉 https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Global_Objects/Math/sumPrecise
Only works in Firefox ATM. Like, Chrome and Safari can't even add numbers currently.
Paolo Amoroso
amoroso@oldbytes.spaceEerie Linux posted an extensive introduction to using CP/M that assumes no previous knowledge of early operating systems. They also link to other posts they wrote on the evolution of CP/M.
https://eerielinux.wordpress.com/2025/08/28/a-gentle-introduction-to-cp-m
/r/netsec
_r_netsec@infosec.exchangeKsmbd Fuzzing Improvements and Vulnerability Discovery https://blog.doyensec.com/2025/09/02/ksmbd-2.html
buherator
buheratorhttps://u1f383.github.io/linux/2025/09/02/linux-io-port-access-checks-on-x86_64.html
Viss
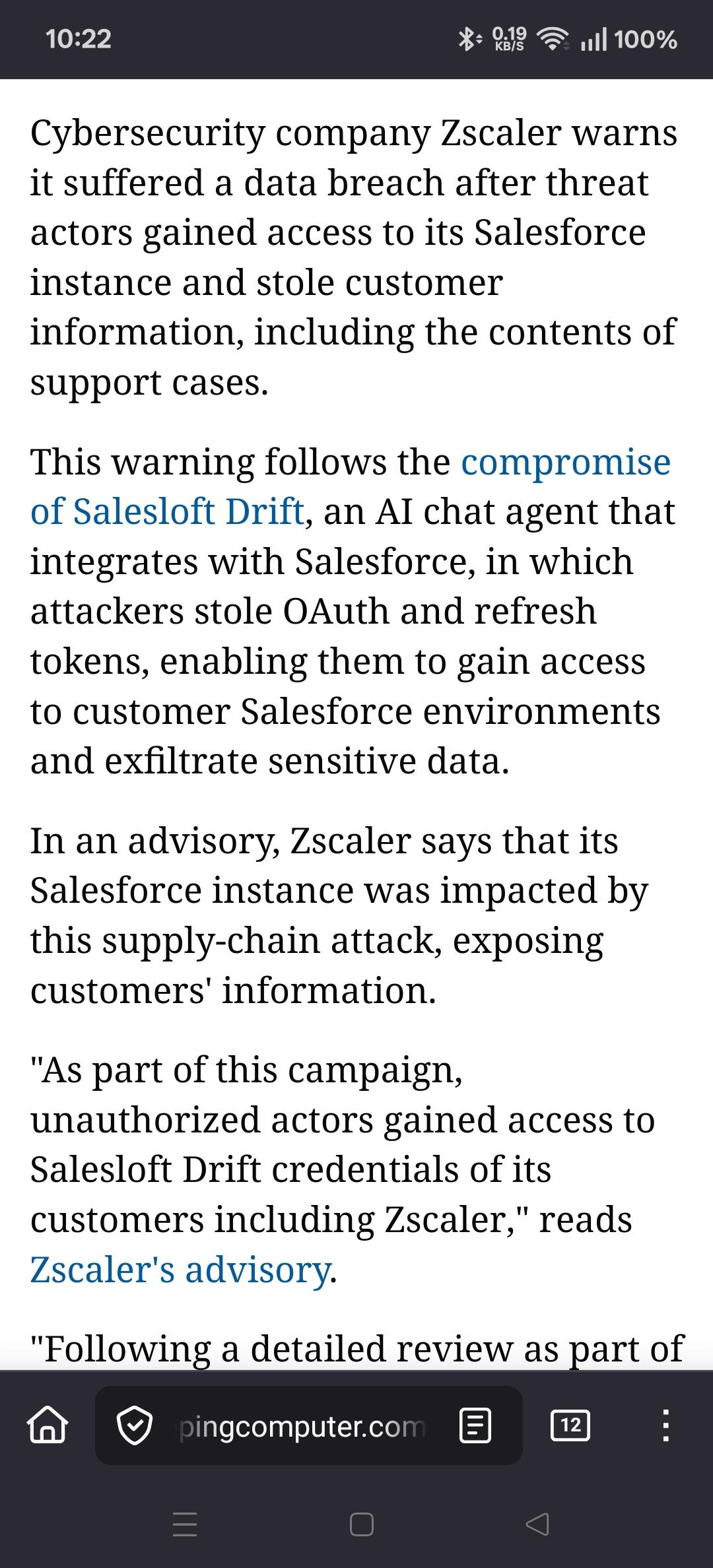
Viss@mastodon.socialgo to the cloud they said
it'll be fine they said
https://www.bleepingcomputer.com/news/security/zscaler-data-breach-exposes-customer-info-after-salesloft-drift-compromise/
buherator
buheratorhttps://en.wikipedia.org/wiki/Wired_Equivalent_Privacy
buherator
buheratorlintile
lintile@hackers.townYour #DFIU category today is OG HACKER SHIRTS
This Ron Rivest 1987 cipher, illegal to export from the US (mathematical munitions), fit on 3 lines of Perl and adorned t-shirts as a form of civil disobedience before becoming the WEP protocol's greatest weakness