Posts
2488Following
654Followers
1479buherator
buheratordaniel:// stenberg://
bagder@mastodon.socialMeanwhile, if you abuse the API and don't comply, asan might complain but that's not a #curl security problem.
Programming Quotes
programming_quotes@mastodon.socialAny fool can write code that a computer can understand. Good programmers write code that humans can understand.
— Martin Fowler
Charlie Balogh
chainq@mastodon.socialNo CPU Challenge by Demostue Allst★rs
Evoke 2025 party Alternative Platforms compo winner.
An Amiga AGA demo that entirely runs on the copper. This is the same capture from real hardware, that was presented in the compo.
https://youtu.be/OXT5MrDdyB8
https://www.pouet.net/prod.php?which=104753
(Edit: updated YouTube link, due to audio sync issues)
Julian Stecklina
blitz@infosec.exchange@amarsaar The code now lives here for easier reference: https://github.com/blitz/l1tf-demo
erysdren
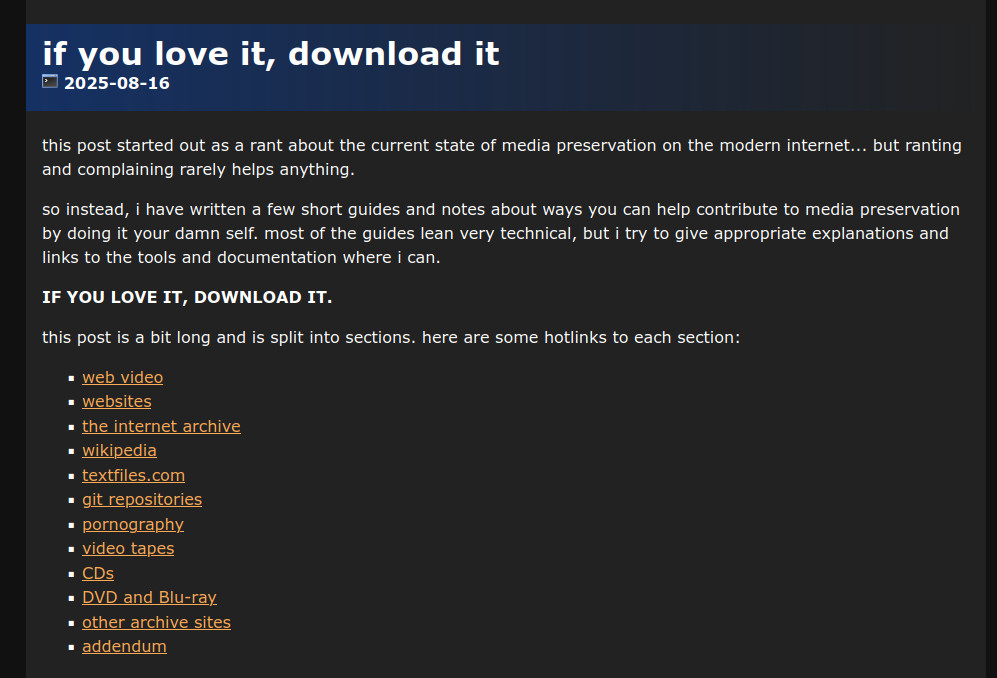
erysdren@idtech.spaceIF YOU LOVE IT, DOWNLOAD IT.
https://erysdren.me/blog/2025-08-16/
Nina Kalinina
nina_kali_nina@tech.lgbtAnd we're live with Pentium II: https://youtube.com/live/Jt4_ekA7q4M?feature=share
danzin
danzin@mastodon.socialPreparing a post about lafleur, the CPython JIT fuzzer I develop.
It has found 4 JIT crashes so far:
#136996: "JIT: `executor->vm_data.valid` assertion failure in `unlink_executor`".
#137007: "JIT: assertion failure in _PyObject_GC_UNTRACK".
#137728: "Assertion failure or `SystemError` in `_PyEval_EvalFrameDefault` in a JIT build".
#137762: "Assertion failure in `optimize_uops` in a JIT build".
Contributions welcome!
https://github.com/search?q=repo%3Apython%2Fcpython+lafleur&type=issues
buherator
buherator(note that I said entertaining, not informative or useful...)
École des Bro-Arts
aphyr@woof.groupMade a little pornographic test case for the UK #OnlineSafetyAct, to see whether we can get Ofcom to ban AWS S3 from the United Kingdom.
buherator
buheratordaniel:// stenberg://
bagder@mastodon.socialDoing #curl command lines in powershell can be a whole adventure: https://medium.com/@shindeshreeharsh157/my-midnight-battle-with-a-curl-command-ac6b22942f01
buherator
buheratorhttps://github.com/google/security-research/security/advisories/GHSA-xrg4-qp5w-2c3w
CVE-2025-48387
buherator
buheratorhttps://github.com/google/security-research/security/advisories/GHSA-v2c8-vqqp-hv3g
buherator
buheratorI absolutely agree with *your* comment, but this is just bad journalism transforming expert opinion into clickbait bullshit.