Posts
3368Following
712Followers
1579eShard
eshard@infosec.exchangeOur Windows CTF is coming to Nullcon in Berlin, Sept 4-5 🎯 https://github.com/eshard/TTA-CTF
Play for a chance to win a Binary Ninja license or a Flipper Zero.
Simon Tatham
simontatham@hachyderm.ioThere is a new short domain name for #PuTTY!
At present, this is just a "landing page": a nice short name to remember, which will redirect you to the full PuTTY website at the same longer URL where it's always been.
But unlike putty.org or other third-party landing pages, this one is run by us, the actual PuTTY team, and it doesn't have a weird separate agenda of its own.
I intend to move the main PuTTY site over to that domain in the future, and leave just a redirector at the old location. But first I want to get the word out, so that people know which site to trust.
If anyone is still linking to putty.org, here's a place to link to instead. Please spread the word!
buherator
buheratorhttps://www.reddit.com/r/vintagecomputing/comments/1mp7r9w/about_30_sun_sparc_workstations_need_a_new_home/
buherator
buheratorhttps://www.openwall.com/lists/oss-security/2025/08/13/9
#FOSS #supplychain
Dgar
dgar@aus.social“Head, shoulders, knees and toes.”
Went from being a fun little kids song to a list of things that hurt.
buherator
buheratorhanno
hanno@mastodon.socialIn case I know anyone here who's familiar with the finer details of DNS and particularly DNS amplification attacks and their mitigations, I have some questions.
buherator
buheratorhttps://binary.ninja/2025/08/12/function-level-basic-block-analysis.html
Ayke van Laethem
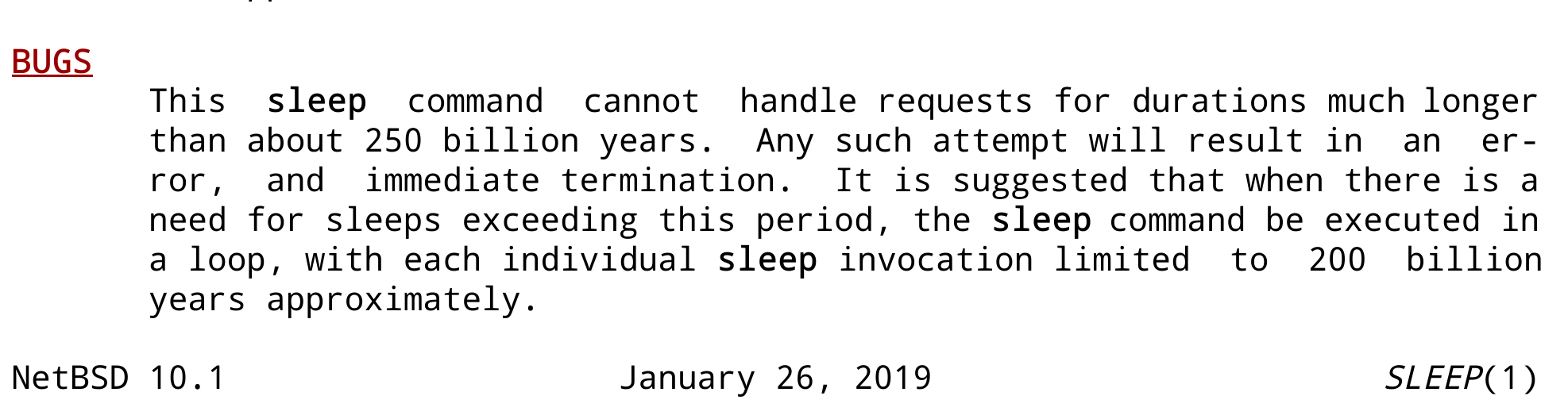
ayke@hachyderm.ioSomehow landed on the NetBSD manpage of sleep(1) and they seem to have a rather unique take on what is considered a bug.
Dark Web Informer
darkwebinformer@bird.makeup🚨Alleged Sale of Fortinet 0-Day RCE Exploit
• Industry: N/A
• Threat Actor: WISDOM
• Network: Clearnet, Dark Web
• Price: 0.5 BTC
• Details: A threat actor claims to be selling a 0-day remote code execution (RCE) exploit affecting FortiOS VPN versions 7.4 to 7.6. The listing includes a proof of concept (PoC) available to serious buyers with deposit or established reputation.
Filippo Valsorda
filippo@abyssdomain.expertI edited my Cross-Site Request Forgery countermeasures research into a stand-alone article, including recommendations reusable by other projects.
tl;dr: no need for tokens or keys, modern browsers tell you if a request is cross-origin!
Kagi HQ
kagihq@mastodon.social"Orion Browser for Linux Gets Exciting Progress Update" 👇
https://www.omgubuntu.co.uk/2025/08/orion-browser-linux-milestone-2-webkit-alternative-chromium
buherator
buheratorhttps://horizon3.ai/attack-research/attack-blogs/from-support-ticket-to-zero-day/
Jeff Hall - PCIGuru 
jbhall56@infosec.exchange
Markus Vervier 👾
marver@mastodon.socialHere's the full writeup of CVE-2025-53773 - Visual Studio & Copilot – Wormable Command Execution via Prompt Injection: https://www.persistent-security.net/post/part-iii-vscode-copilot-wormable-command-execution-via-prompt-injection
Patch now!
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@eupolicy.socialI had a great time at the most excellent #why2025 camp! Here a write-up of my own #DNA talks (with links to video & annotated slides), some observations on the tremendously terrible state of security & regulation, and what we could do about it, plus some nice photos!
https://berthub.eu/articles/posts/dna-talks-and-why2025/
buherator
buheratorShow content
https://amylandthesniffers.bandcamp.com/
buherator
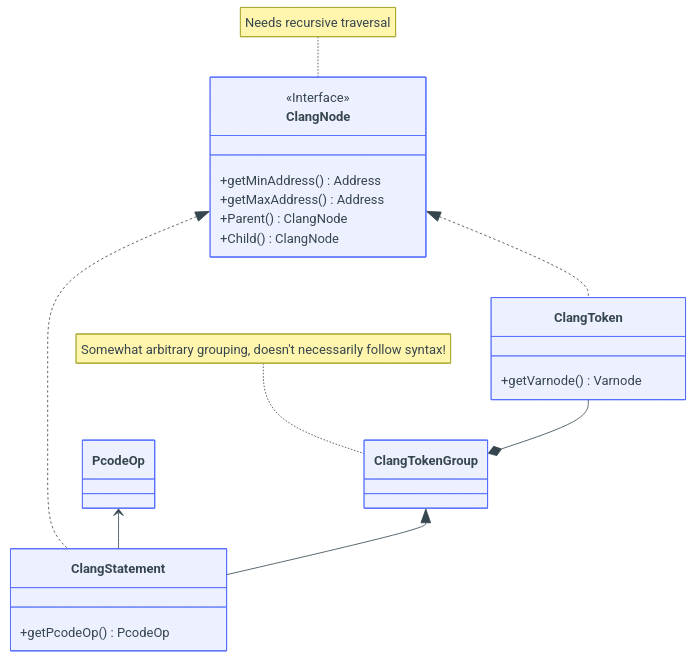
buheratorhttps://github.com/v-p-b/ghidra-cheat-sheet/blob/main/scripts/dump_clang.py
Sample output:
https://scrapco.de/ghidra-cheat-sheet/decompiler/structure_samples/
buherator
buheratorhttps://scrapco.de/ghidra-cheat-sheet/
PR's and suggestions are most welcome!