Posts
2478Following
654Followers
1480
Unnamed RE Podcast 
unnamedre@infosec.exchange
New episode is up!
We talked with Nathan Emerick about the Spotify CarThing and it's journey to becoming the DeskThing :D
https://unnamedre.com/episode/75
buherator
buheratorbuherator
buheratorhttps://github.com/NationalSecurityAgency/ghidra/releases/tag/Ghidra_11.4.1_build
What's New:
https://github.com/NationalSecurityAgency/ghidra/blob/Ghidra_11.4.1_build/Ghidra/Configurations/Public_Release/src/global/docs/WhatsNew.md
Change History:
https://github.com/NationalSecurityAgency/ghidra/blob/Ghidra_11.4.1_build/Ghidra/Configurations/Public_Release/src/global/docs/ChangeHistory.md
Graham Sutherland / Polynomial
gsuberland@chaos.socialblue cheese (the blue is Cherenkov radiation)
Caitlin Condon
catc0n@infosec.exchangeThis is super interesting and isn’t a type of research I’ve seen a lot of before. Great write-up from @albinolobster and team on attacker infrastructure longevity: https://www.vulncheck.com/blog/stillup-stillevil
ɗ𐐩ʃƕρʋ
deshipu@fosstodon.orgAny technical solution that is supposed to block teenagers from anything is not going to work very well, because you are facing an opponent that:
* is smarter than you,
* is very dedicated,
* has a lot of free time,
* has an extensive network of friends,
* faces no serious consequences if caught,
* outnumbers you,
* considers you an immoral crook.
You really, *really* want to have them on your side. That means education rather than control.
Joel Chippindale
joel@social.monkeysthumb.co.uk"If you only praise last-minute saves, you’ll keep getting last-minute problems. Make sure to recognize the engineer who reduced incidents, the PM who saw the risk a month out, the designer who caught the complexity before it shipped. Make that kind of foresight just as visible and valuable as triage and repair."
— @timcheadle from https://www.timcheadle.com/dont-let-crisis-become-a-compass/
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Related: If you want to tell me you've jailbroken the AI, you better be prepared to tell me how you reverse engineered the ETL, data model and guard rails, not how you clicked on the shiny, shiny and got a shell prompt.
Samuel Groß
saelo@chaos.socialWe released our Fuzzilli-based V8 Sandbox fuzzer: https://github.com/googleprojectzero/fuzzilli/commit/675eccd6b6d0c35ea6c7df24a0a1e513cce45bb3
It explores the heap to find interesting objects and corrupts them in a deterministic way using V8's memory corruption API. Happy fuzzing!
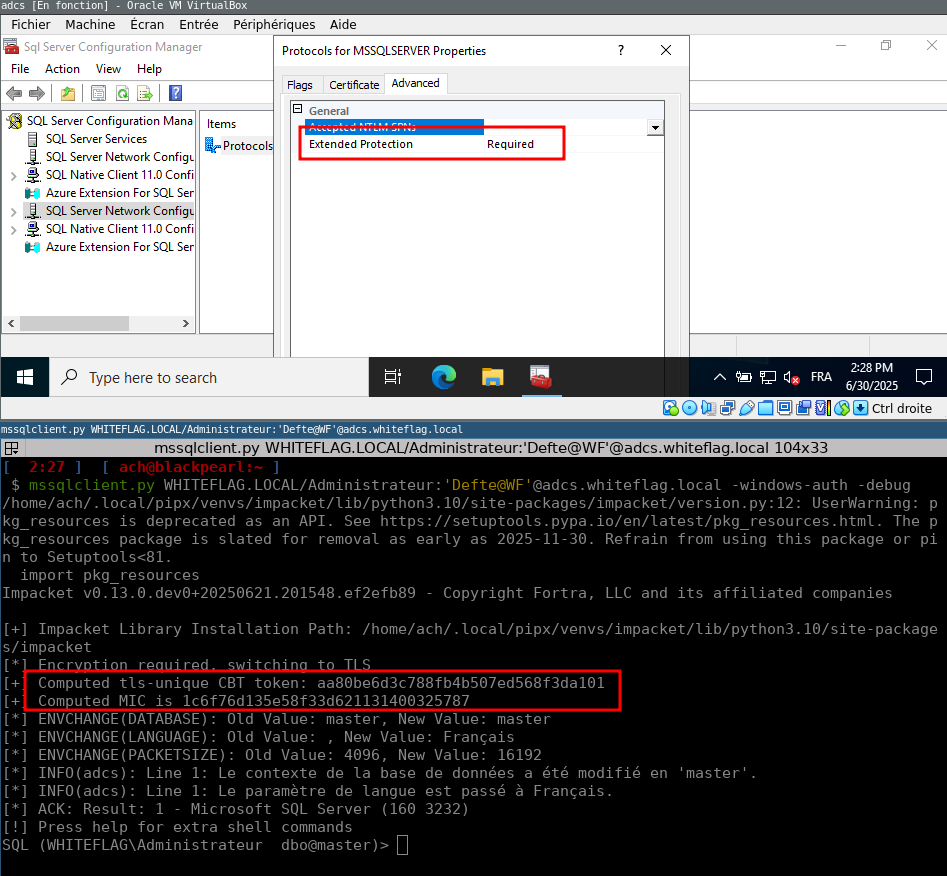
SensePost
sensepost@infosec.exchangeReverse engineering Microsoft’s SQLCMD.exe to implement Channel Binding support for MSSQL into Impacket’s mssqlclient.py. Storytime from Aurelien (@defte_), including instructions for reproducing the test environment yourself.
https://sensepost.com/blog/2025/a-journey-implementing-channel-binding-on-mssqlclient.py/
BobDaHacker 🏳️⚧️ | NB
bobdahacker@infosec.exchangeFound critical vulns in Lovense (the biggest sex toy company) affecting 11M+ users. They ignored researchers for 2+ years, then fixed in 2 days after public exposure. 🤦
What I found:
- Email disclosure via XMPP (username→email)
- Auth bypass (email→account takeover, no password)
History of ignoring researchers:
- 2017: First recorded case of someone reporting XMPP email leak.
- 2022: Someone else reports XMPP email leak, ignored
- Sept 2023: Krissy reports account takeover + different email leak via HTTP API, paid only $350
- 2024: Another person reports XMPP email leak AND Account Takeover vuln, offered 2 free sex toys (accepted for the meme)
- March 2025: I report account takeover + XMPP email leak, paid $3000 (after pushing for critical)
- Told me fix for email vuln needs 14 months because "legacy support" > user security (had 1-month fix ready)
- July 28: I go public
- July 30: Both fixed in 48 hours
Same bugs, different treatment. They lied to journalists saying it was fixed in June, tried to get me banned from HackerOne after giving permission to disclose.
News covered it but my blog has the full technical details:
https://bobdahacker.com/blog/lovense-still-leaking-user-emails/
#InfoSec #BugBounty #ResponsibleDisclosure #Security #Vulnerability #IoT #cybersecurity
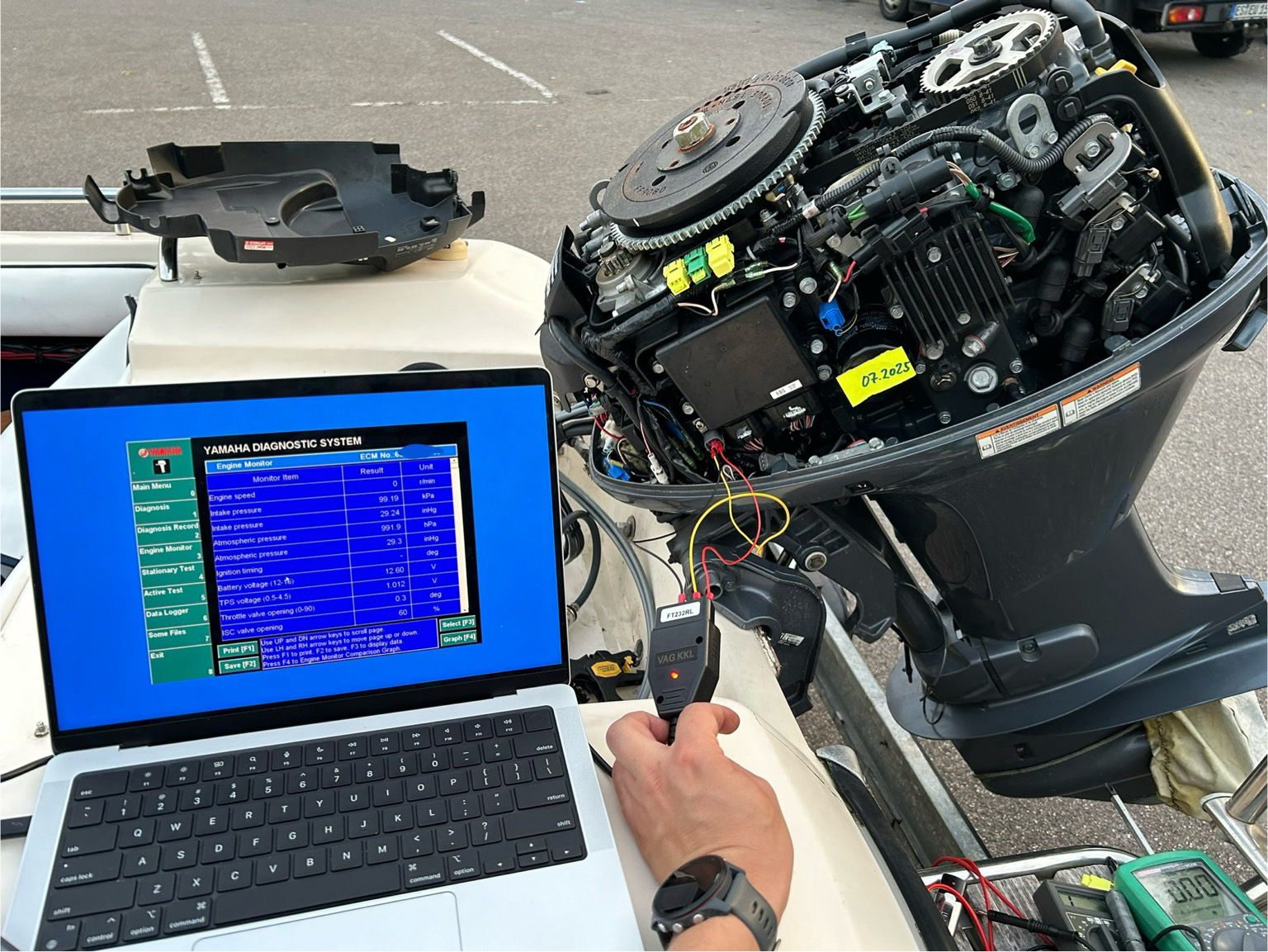
stacksmashing
stacksmashing@infosec.exchangeWhy do so many aspects of my life involve connecting FT232s to random pins 😂
Phrack
phrack@haunted.computerHeya @why2025camp! You got 2250 copies of Phrack Magazine coming your way!!
K. Reid Wightman  🌻
🌻 

reverseics@infosec.exchange
I want to gush about the dumbest thing for a minute.
I subscribe to @molly0xfff 's newsletter thing. And while the news often is a bit concerning, the format is A++++ perfection.
The newsletter comes to my inbox in its entirety. There are references and links, and NONE OF THEM ARE TRACKING LINKS. (well okay, there are two links that are technically trackers, they are the 'more like this' and 'less like this'...it's hard to make some kind of newsletter customization without knowing who clicked the link). But all the rest of the links are just plain links. To plain URLs. Like what we used to have back in the '90s. Remember those halcyon days when readers weren't the product?
I read the whole newsletter every time one comes out, in part because I don't have to 'click here to read more'.
I'm sure it's a little concerning to run a publication this way in the modern era ("are people even reading this?" is probably a real concern. Well hey, at least I do...).
Anyway, if you're able to support her, I do recommend it. Well researched news, worth every penny for the ad-free experience.
Royce Williams
tychotithonus@infosec.exchangeOh look, another "door locks are bad because someone can crawl through the window" scare article (this time a sponsored one). Not responsible journalism, Bleeping.
I especially "appreciate" the scare quotes around "phishing-resistant" 🤬
Ivan Fratric
ifsecure@infosec.exchange@buherator @freddy
CVE-2025-7424 appears to be fixed in today's Apple update :)
Phrack
phrack@haunted.computerAre you going to @defcon ??
We'll have 9500 print copies of Phrack distributed around the con! Come to main stage Sunday @ noon to see phrack staffers @netspooky @richinseattle and @chompie1337 talk hacker history!