Posts
2505Following
650Followers
1469buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250723-00/?p=111403
CFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a434dcc
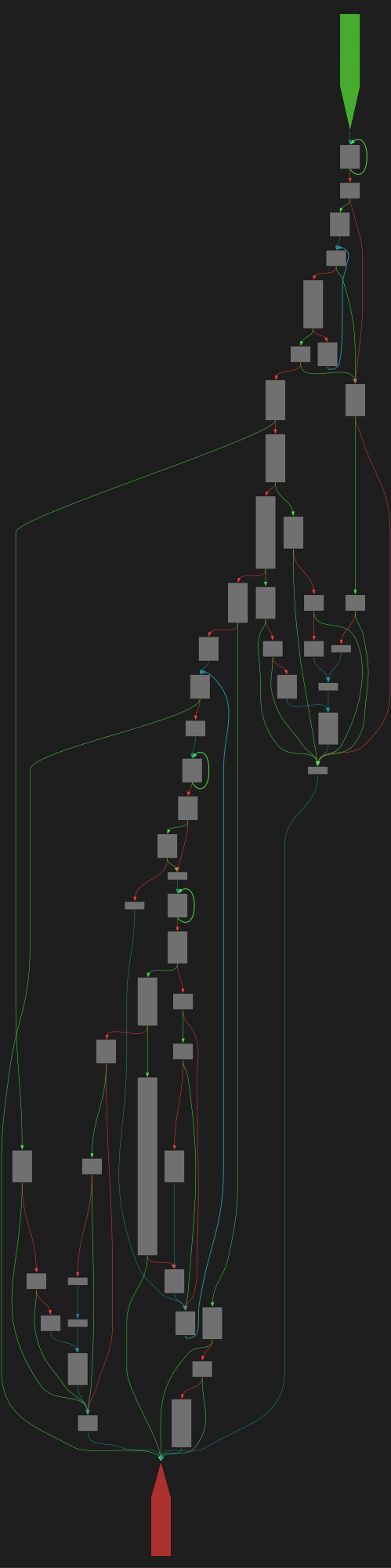
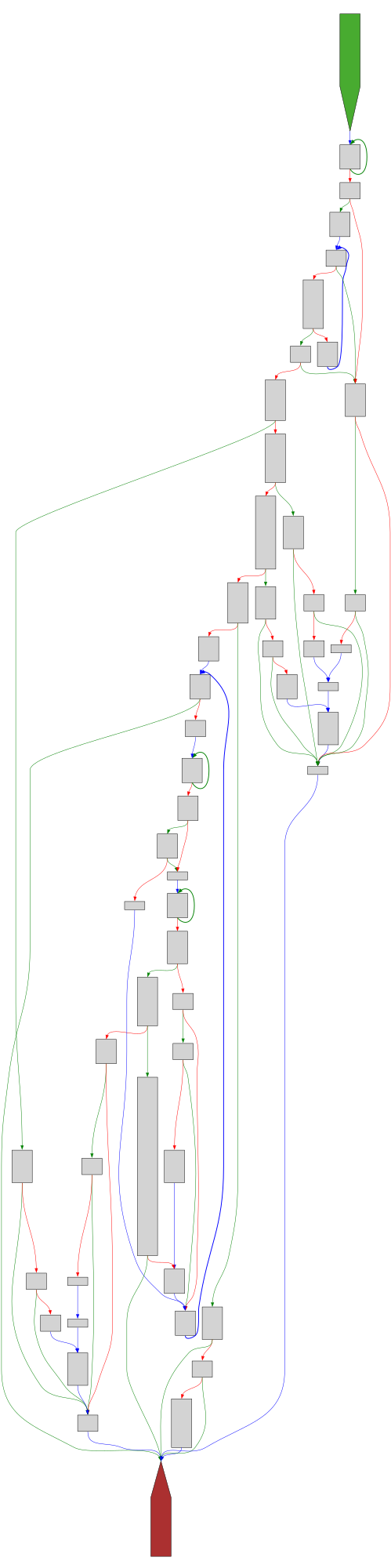
ComparePathWithVolumeMap
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a434dcc.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a434dcc.json&colors=light
Bastian Greshake Tzovaras
gedankenstuecke@scholar.social«Alan Turing Institute scraps diversity drive under pressure from ministers»
Funny change in tune for an institute that was named after a person that was basically killed by the UK government for being gay. 🤷
James Kettle
albinowax@infosec.exchangeWant to make the most of the upcoming research drop? We've just updated https://http1mustdie.com/ with links to essential pre-read/watch resources. Enjoy!
buherator
buheratorhttps://karmainsecurity.com/KIS-2025-06
(Also an XSS @ KIS-2025-05, CVE-2025-48933)
buherator
buheratorhttps://youtu.be/rXPpkzdS-q4
Programmers are Also Human is usually great, but this one is just hysterical xD
LOL. Funny bug to make it to prod.
https://httpd.apache.org/security/vulnerabilities_24.html
A bug in Apache HTTP Server 2.4.64 results in all "RewriteCond expr ..." tests evaluating as "true".
HyperDbg
hyperdbg@infosec.exchangeI'm happy to announce that HyperDbg v0.14 is released!
This version includes HyperEvade (beta preview), fixes Win11 24H2 compatibility issues & adds multiple timing functions to the script engine (Special thanks to @0Xiphorus )
Check it out: https://github.com/HyperDbg/HyperDbg/releases/tag/v0.14
More info on HyperEvade: https://github.com/HyperDbg/slides/blob/main/2025/DEBT2025/hyperevade-ecoop2025-debt.pdf
Microsleep function:
https://docs.hyperdbg.org/commands/scripting-language/functions/timings/microsleep
and RDTSC/RDTSCP:
https://docs.hyperdbg.org/commands/scripting-language/functions/timings/rdtsc
https://docs.hyperdbg.org/commands/scripting-language/functions/timings/rdtscp
Thanks to Tara for making this painting for us (it's not AI-generated).
buherator
buheratorhttps://swarm.ptsecurity.com/the-guest-who-could-exploiting-lpe-in-vmware-tools/
CVE-2025-22230 CVE-2025-22247
buherator
buheratorhttps://talosintelligence.com/vulnerability_reports/TALOS-2025-2201
https://talosintelligence.com/vulnerability_reports/TALOS-2025-2200
https://talosintelligence.com/vulnerability_reports/TALOS-2025-2199
https://talosintelligence.com/vulnerability_reports/TALOS-2025-2198
CVE-2025-35966 CVE-2025-36512 CVE-2025-48498 CVE-2025-46354
danzin
danzin@mastodon.social@buherator Thanks!
The new fuzzer is live and found two JIT crashes, so it's met the goal of being better than an idle core in practice :)
buherator
buheratorhttps://slcyber.io/assetnote-security-research-center/how-we-accidentally-discovered-a-remote-code-execution-vulnerability-in-etq-reliance/
CVE-2025-34140 CVE-2025-34141 CVE-2025-34142 CVE-2025-34143
buherator
buheratorhttps://github.com/emcalv/BlackHat-MEA-2024-slides/blob/main/BH%20MEA%202024%20-%20Reverse%20Engineering%20of%20Security%20Products_%20Defender.pdf
SkelSec
skelsec@bird.makeupShared the PoC with @mkolsek few days ago, the same one I gave to microsoft. Unlike microsoft however, they not only verified the issue within days but refined it demonstrating that ANY domain user can crash a fully patched windows 2025 server as of now.
https://bird.makeup/users/0patch/statuses/1947674442772910437
catsynth / amanda c
catsynth@mstdn.socialIn memory of Ozzy Osbourne, we replay our review of Technical Ecstasy, an often overlooked album from his era of Black Sabbath that is among our favorites at CatSynth. We extend our thoughts to his family, friends, and colleagues 😿
https://youtu.be/vklyJuPbilY
tiddy roosevelt
babe@glitterkitten.co.ukBanana ozzy deployed to usher gk through a period of mourning 
Mattias_G
Mattias_G@mastodon.gamedev.placeI am excited to share this new single-header C library I have been working on for a while now: vecmath.h, a comprehensive vector/matrix math library for graphics/games/3d.
It allows you to write vector math code in C that looks like this:
A ../ in AIM server just feels right.
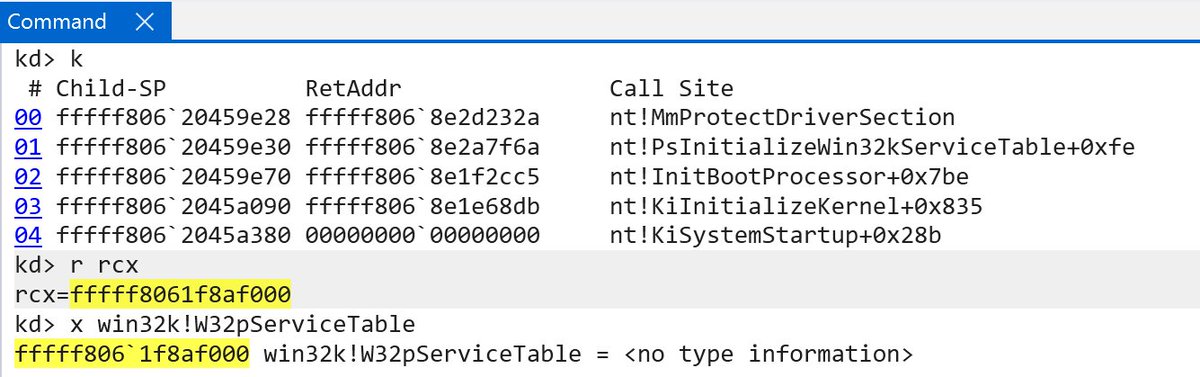
Connor McGarr
33y0re@bird.makeupI don't know which update specifically, but in a recent update of 24H2 it looks like the Win32k system call table is protected by Kernel Data Protection (read-only SLAT entry)! I believe CI!g_CiOptions and msseccore's SecKdpSe PE section were the only things using it before.