Posts
2733Following
681Followers
1505buherator
buheratorbuherator
buheratorbetter chance of finding a bug than an idle CPU core."
https://fuzzinginfo.wordpress.com/wp-content/uploads/2012/05/ben_nagy_how_to_fail_at_fuzzing.pdf
Good luck ;)
Has anyone had/decided-not-to-have an intern specifically in a vuln research team? We're debating it at work but some people are skeptical WRT the amount of work we'd be putting in mentoring (we aren't prepared to half-ass it), vs the amount of business value we'd get out. Candidates are strong (having CVEs for example) but it's a big ask to put them on a fortigate (for example) and expect results - and at the same time, it's not fair to give an intern a hard project which is likely going to give them a confidence hit. How did you / how could I manage this? Ideally I don't want to give interns non-research work (like the usual 'set up a lab'), I know they want to be finding bugs. Plus we've got the university sponsoring it wanting clear projects and targets, which can be really difficult in a research team. Any tips? If it helps, our team looks at 0day/nday and our usual output is blogposts and fingerprinting scripts (usually fingerprinting via exploitation - we'd much rather exploit a vuln and detect that than rely on stuff like banners).
Open Source Security mailing list
oss_security@bird.makeupCVE-2025-4674: Go: cmd/go: unexpected command execution in untrusted VCS repositories https://www.openwall.com/lists/oss-security/2025/07/08/5
Using the Go toolchain in directories fetched using VCS tools (such as cloning Git or Mercurial repositories) can execute unexpected commands. Fixed in 1.24.5 & 1.23.11.
buherator
buheratorHandy #PowerShell tooling by EQ
https://blog.mantrainfosec.com/blog/17/automated-function-id-database-generation-in-ghidra-on-windows
buherator
buheratorAnother Windows CLFS exploit
https://starlabs.sg/blog/2025/07-my-blind-date-with-cve-2025-29824/
buherator
buheratorhttps://nina.chat/
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250716-00/?p=111383
buherator
buheratorhttps://u1f383.github.io/android/2025/07/16/an-interesting-cache-coherence-vulnerability-in-the-mali-gpu-driver.html
buherator
buheratorhttps://www.netspi.com/blog/technical-blog/red-teaming/cve-2025-4660-forescout-secureconnector-rce/
buherator
buheratorhttps://swarm.ptsecurity.com/daemon-ex-plist-lpe-via-macos-daemons/
CFG Bot 🤖
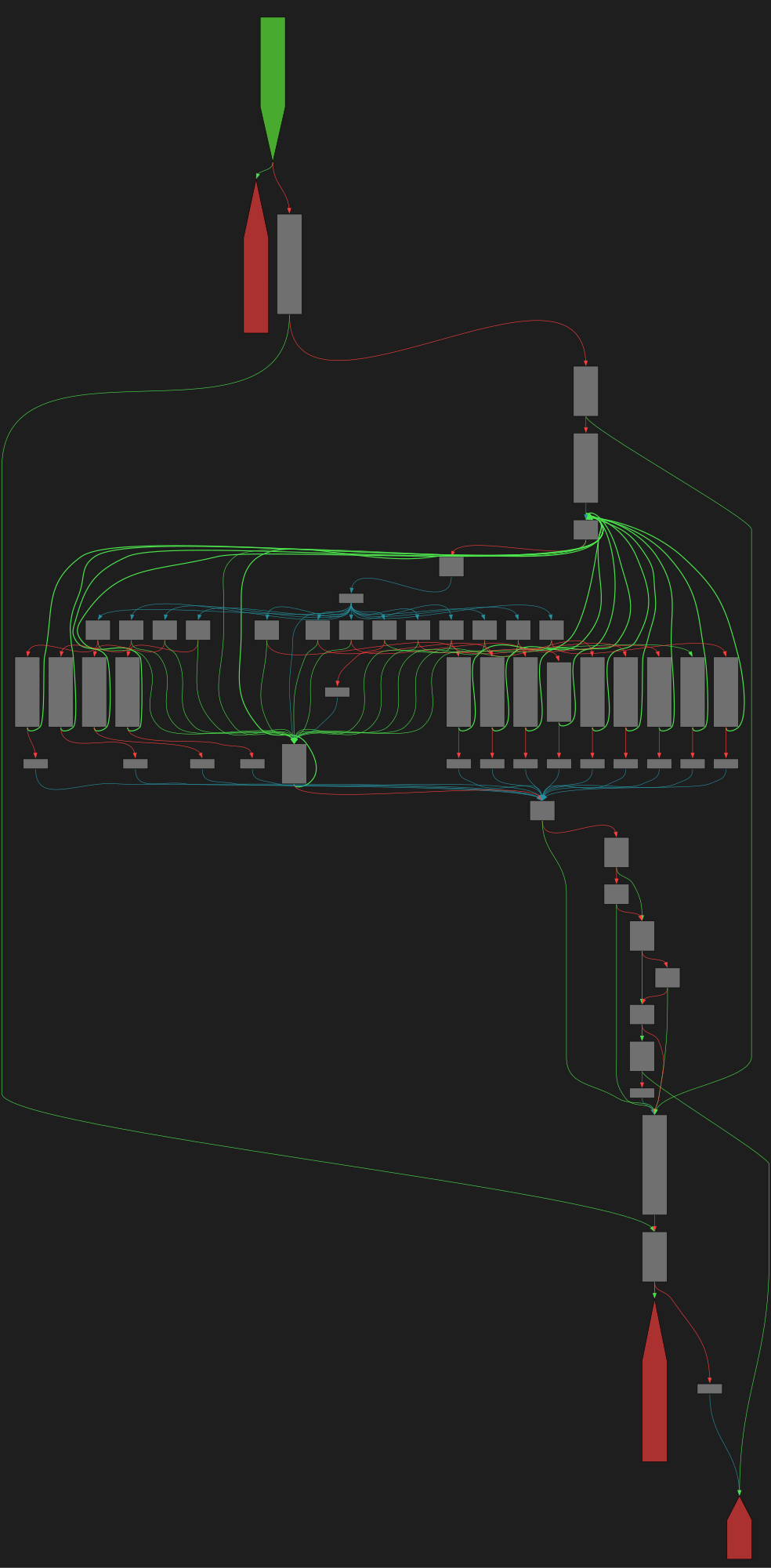
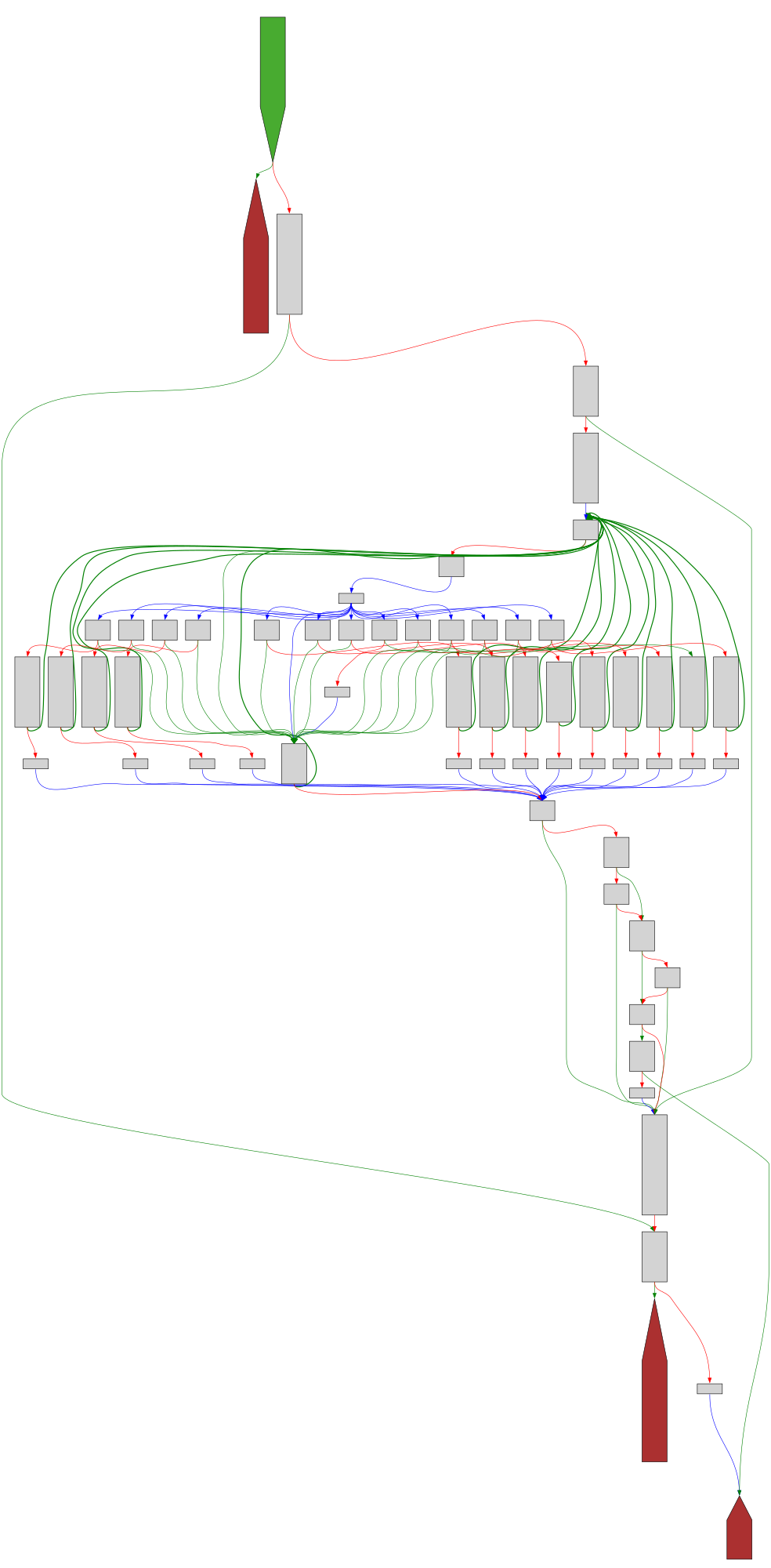
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 005c87c0
evp_kem_from_algorithm
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F005c87c0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F005c87c0.json&colors=light
Foone🏳️⚧️
foone@digipres.clubI want someone to make a video series where they exceed cable lengths and show what happens.
what happens if you have a 2km USB cable? what works and what breaks?
If you are enabling an AI feature scanning all your emails, consider this will also scan the emails people have sent you. This information could include personal or otherwise legally protected information.
If this data leaks later (as it regularly happens with these systems), this could mean severe legal consequences for you down the road.
YOU are responsible for protecting the data of others under your custody.
This includes the messages and emails others send to you.
cynicalsecurity 
cynicalsecurity@bsd.network
It has been a while but the latest edition of the Security Liberation Front is out!
Lorenzo Franceschi-Bicchierai
lorenzofb@infosec.exchangeNEW: Security researchers and CISA warn that hackers are exploiting a flaw in the Signal clone TeleMessage, which could lead to them stealing "plaintext usernames, passwords, and other sensitive data."
@h0wdy, the researcher who analyzed it said they were "in disbelief at the simplicity of this exploit."
Programming Quotes
programming_quotes@mastodon.social(...) Thinking this way will teach you two things about computers: One, there's no magic, no matter how much it looks like there is. There's just work to make things look like magic. And two, it's crazy in there.
— Paul Ford