Posts
3373Following
712Followers
1579CFG Bot 🤖
cfgbot@mastodon.socialProject: kubernetes/kubernetes https://github.com/kubernetes/kubernetes
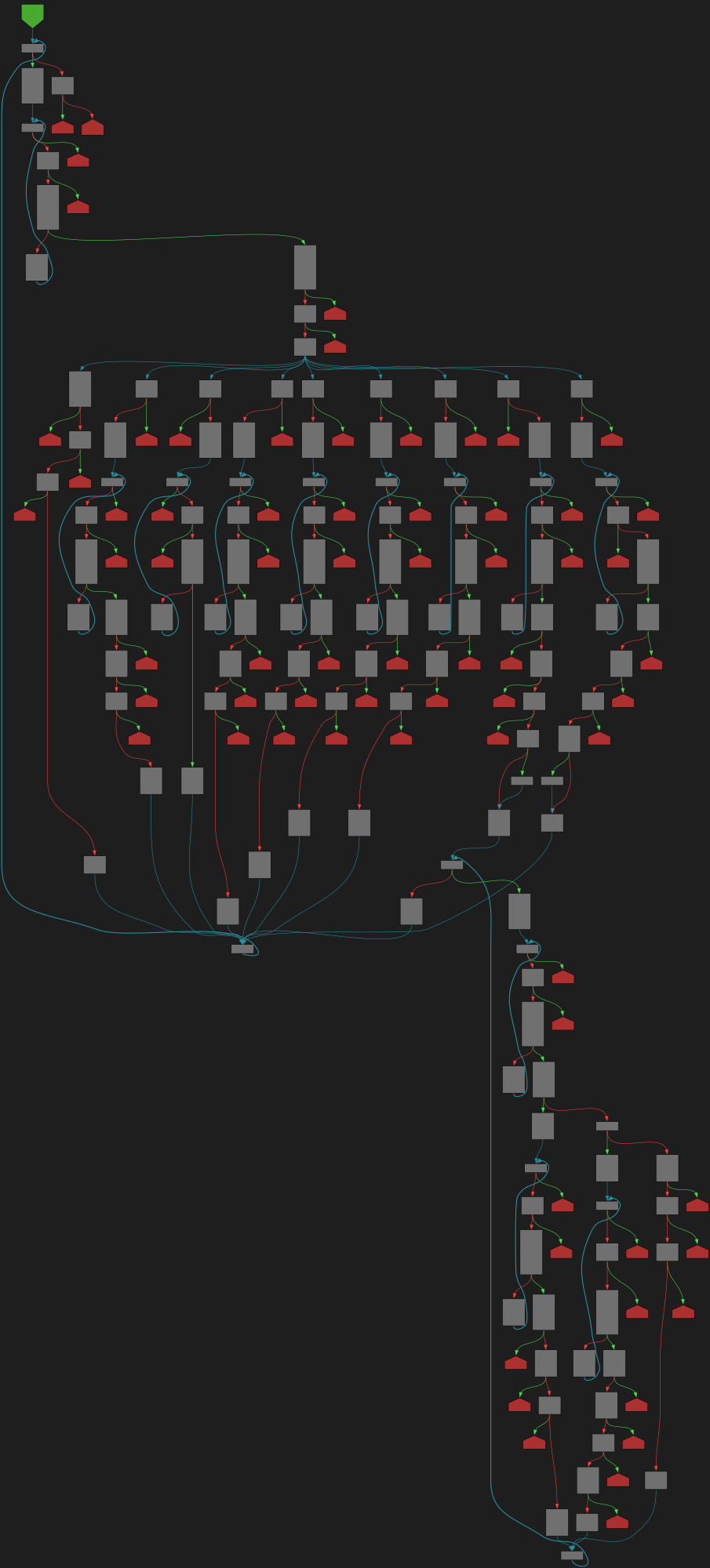
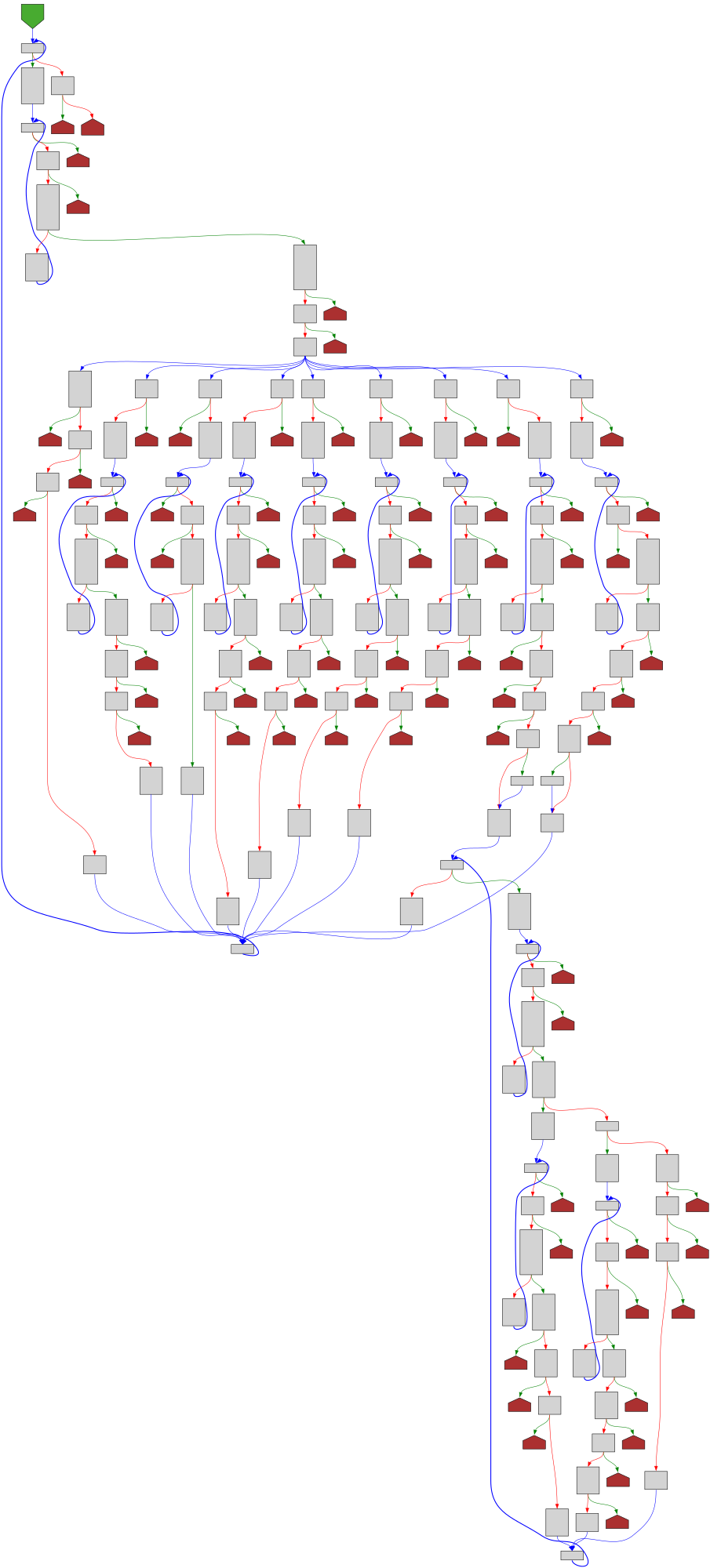
File: staging/src/k8s.io/api/certificates/v1/generated.pb.go:1378 https://github.com/kubernetes/kubernetes/blob/a62752db5110225a89a83ec844a5884413e550ff/staging/src/k8s.io/api/certificates/v1/generated.pb.go#L1378
func (m *CertificateSigningRequestSpec) Unmarshal(dAtA []byte) error
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fkubernetes%2Fkubernetes%2Fblob%2Fa62752db5110225a89a83ec844a5884413e550ff%2Fstaging%2Fsrc%2Fk8s.io%2Fapi%2Fcertificates%2Fv1%2Fgenerated.pb.go%23L1378&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fkubernetes%2Fkubernetes%2Fblob%2Fa62752db5110225a89a83ec844a5884413e550ff%2Fstaging%2Fsrc%2Fk8s.io%2Fapi%2Fcertificates%2Fv1%2Fgenerated.pb.go%23L1378&colors=light
buherator
buheratorscott f
scott@carfree.citylocal restaurants I love you but please have a website that isn't your instagram profile and has your hours of business on it. kthx
buherator
buheratorbuherator
buheratorhttps://www.lrqa.com/en/cyber-labs/remote-code-execution-in-broadcom-altiris-irm/
blacktop
blacktop@mastodon.socialHigh level diff of iOS 18.6 beta2 vs. iOS 18.6 beta3 🎉
https://github.com/blacktop/ipsw-diffs/blob/main/18_6_22G5064d__vs_18_6_22G5073b/README.md
Sass, David
sassdawe@infosec.exchangeWHAT IS THIS SOURCERY?!
#Winget has #DSC support now?!
I can start #WindowsSandbox and have the required security tools installed #automagically!
https://github.com/microsoft/winget-dsc/tree/main/samples/DscResources/Microsoft.WindowsSandbox.DSC
There’s an entire rant buried in here but, in short, I absolutely agree.
buherator
buheratorhttps://karmainsecurity.com/KIS-2025-04
buherator
buheratorBtw. this is the talk&slides by @ifsecure :
https://www.youtube.com/watch?v=U1kc7fcF5Ao
https://docs.google.com/presentation/d/1pAosPlKUw4uI5lfg7FVheTZAtI5mUy8iDeE4znprV34/edit
OpenSecurityTraining2
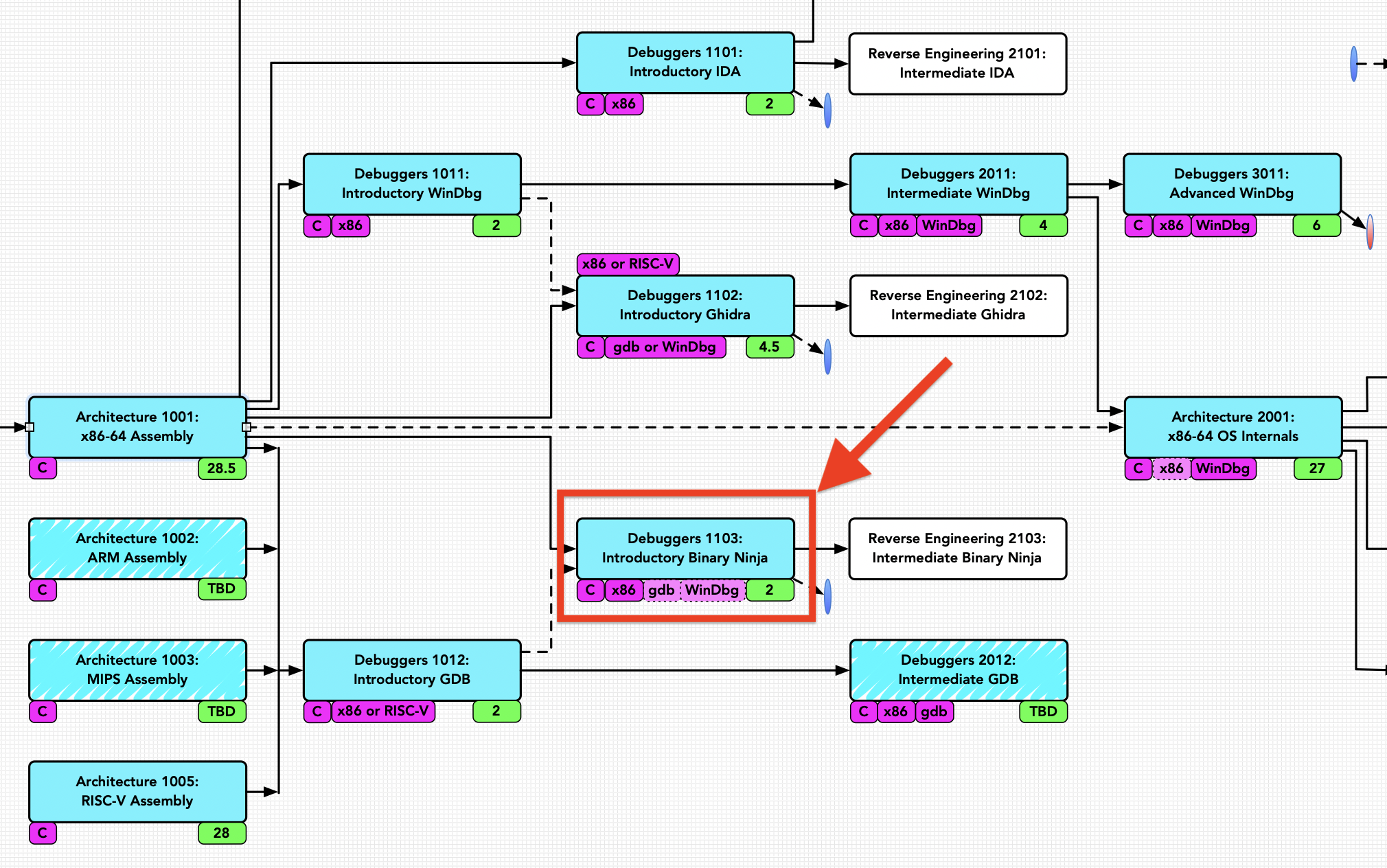
OpenSecurityTraining2@infosec.exchange📣"Debuggers 1103: Introductory Binary Ninja" is released!📣
https://ost2.fyi/Dbg1103
This class by Xusheng Li of Vector 35 @binaryninja provides students with a hands-on introduction to the free version of Binja as a debugger, thus providing decompilation support!
Like all current #OST2 classes, the core content is made fully public, and you only need to register if you want to post to the discussion board or track your class progress. This mini-class takes approximately 2 hours to complete, and can be used as standalone cross-training for people who know other reverse engineering tools, or by students learning assembly for the first time in the https://ost2.fyi/Arch1001 x86-64 Assembly class.
buherator
buheratorhttps://www.openwall.com/lists/oss-security/2025/07/11/2
CVE-2025-7424 CVE-2025-7425
#OSS #FOSS
buherator
buherator- CVE-2025-1735 SQLi via pgsql (related to CVE-2025-1094)
https://github.com/php/php-src/security/advisories/GHSA-hrwm-9436-5mv3
- CVE-2025-1220 SSRF via fsockopen()
https://github.com/php/php-src/security/advisories/GHSA-3cr5-j632-f35r
- CVE-2025-6491 NULL deref in SOAP handling
https://github.com/php/php-src/security/advisories/GHSA-453j-q27h-5p8x
Valerie Aurora 🇺🇦
vaurora@mstdn.socialWant to influence the rules for vulnerability handling for every internet-connected product sold in the EU? Of course you do!
You are invited to the vulnerability handling deep dive session for the Cyber Resilience Act. July 22, online, free registration:
https://www.stan4cra.eu/event-details/deep-dive-session-vulnerability-handling
More info: https://www.stan4cra.eu/resources
/r/netsec
_r_netsec@infosec.exchangeRevisiting automating MS-RPC vulnerability research and making the tool open source https://www.incendium.rocks/posts/Revisiting-MS-RPC-Vulnerability-Research-automation/
buherator
buherator/index.xml
/feed.xml
#syndication