Posts
2512Following
650Followers
1471buherator
buheratorBtw. this is the talk&slides by @ifsecure :
https://www.youtube.com/watch?v=U1kc7fcF5Ao
https://docs.google.com/presentation/d/1pAosPlKUw4uI5lfg7FVheTZAtI5mUy8iDeE4znprV34/edit
OpenSecurityTraining2
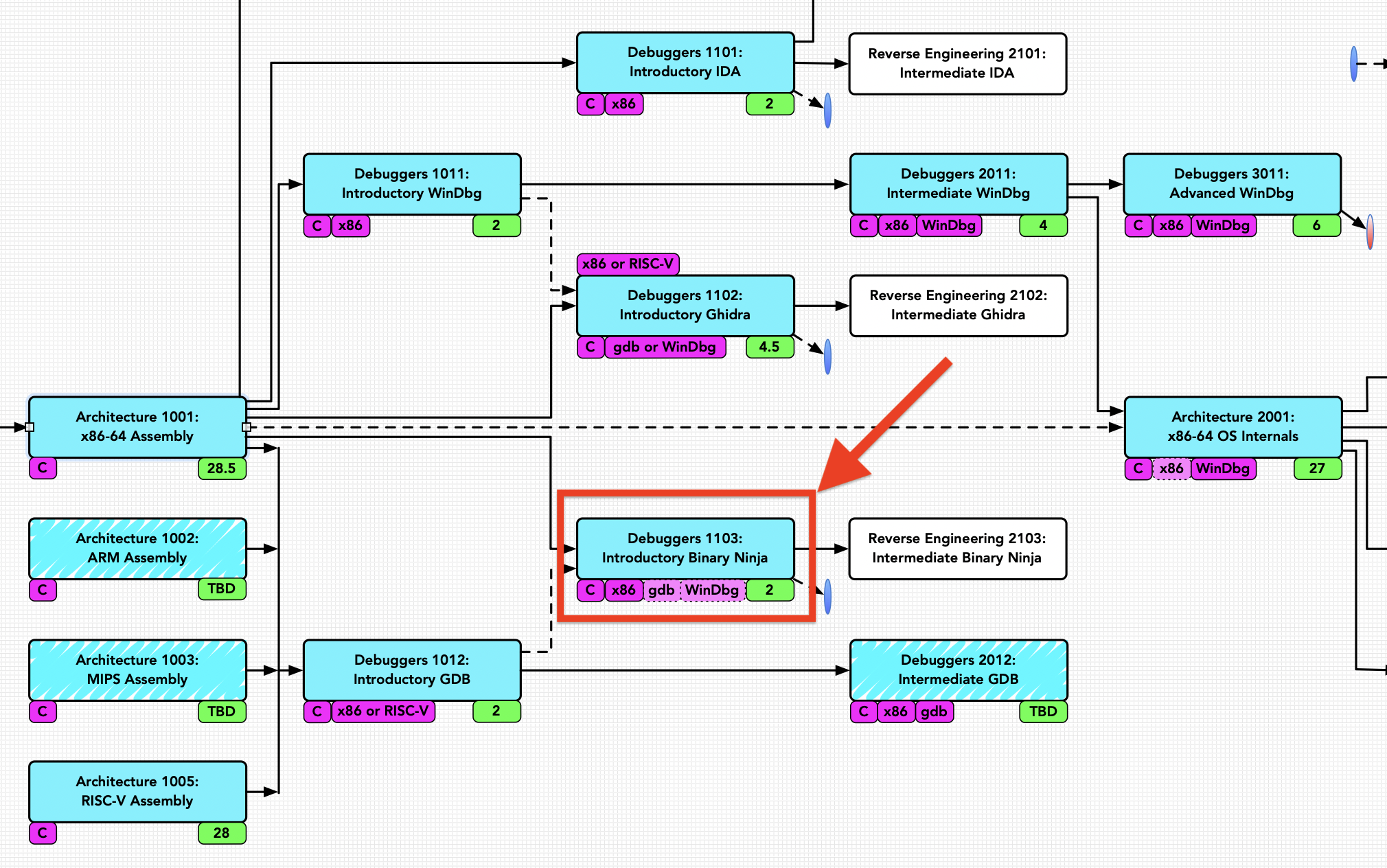
OpenSecurityTraining2@infosec.exchange📣"Debuggers 1103: Introductory Binary Ninja" is released!📣
https://ost2.fyi/Dbg1103
This class by Xusheng Li of Vector 35 @binaryninja provides students with a hands-on introduction to the free version of Binja as a debugger, thus providing decompilation support!
Like all current #OST2 classes, the core content is made fully public, and you only need to register if you want to post to the discussion board or track your class progress. This mini-class takes approximately 2 hours to complete, and can be used as standalone cross-training for people who know other reverse engineering tools, or by students learning assembly for the first time in the https://ost2.fyi/Arch1001 x86-64 Assembly class.
buherator
buheratorhttps://www.openwall.com/lists/oss-security/2025/07/11/2
CVE-2025-7424 CVE-2025-7425
#OSS #FOSS
buherator
buherator- CVE-2025-1735 SQLi via pgsql (related to CVE-2025-1094)
https://github.com/php/php-src/security/advisories/GHSA-hrwm-9436-5mv3
- CVE-2025-1220 SSRF via fsockopen()
https://github.com/php/php-src/security/advisories/GHSA-3cr5-j632-f35r
- CVE-2025-6491 NULL deref in SOAP handling
https://github.com/php/php-src/security/advisories/GHSA-453j-q27h-5p8x
Valerie Aurora 🇺🇦
vaurora@mstdn.socialWant to influence the rules for vulnerability handling for every internet-connected product sold in the EU? Of course you do!
You are invited to the vulnerability handling deep dive session for the Cyber Resilience Act. July 22, online, free registration:
https://www.stan4cra.eu/event-details/deep-dive-session-vulnerability-handling
More info: https://www.stan4cra.eu/resources
/r/netsec
_r_netsec@infosec.exchangeRevisiting automating MS-RPC vulnerability research and making the tool open source https://www.incendium.rocks/posts/Revisiting-MS-RPC-Vulnerability-Research-automation/
Ian Campbell
neurovagrant@masto.deoan.orgThis is fun. Google Gemini’s “Summarize email” function is vulnerable to invisible prompt injection utilized to deceive users, including with fake security alerts.
buherator
buherator/index.xml
/feed.xml
#syndication
No-AI and solid end-to-end encryption is the new tech hype.
If you don't invest heavily in solid end-to-end encryption, privacy-protective and No-AI features, you will be left behind. People might even laugh at you.
Tell everyone.
buherator
buheratorhttps://swarm.ptsecurity.com/buried-in-the-log-exploiting-a-20-years-old-ntfs-vulnerability/
I think I missed this one about CVE-2025-49689
Marco Ivaldi
raptor@infosec.exchange[CVE-2025-38001] #Exploiting All Google #kernelCTF Instances And Debian 12 With A #0Day For $82k: A RBTree Family Drama (Part One: LTS & COS)
DocAtCDI
DocAtCDI@mastodon.socialMy office computer just crashed and now all the other computers have slowed down so they can see whats happening.
daniel:// stenberg://
bagder@mastodon.socialalgernon ludd can't think of a funny name atm
algernon@come-from.mad-scientist.clubI just released #iocaine version 2.5.0, probably the last 2.x version, as I'm starting to lay out the roadmap for 3.0.
Apart from a couple of handy new features to aid in bot detection and data collection, there's an important fix in it too: previously, the built-in templates did not escape the generated text properly, which could lead to all kinds of weirdness. Now they do.
The templates also have access to a new filter - urlencode -, which helps escaping random text generated to be used as URLs.
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@eupolicy.socialEurope appears to just have given up on doing anything technical. Perhaps we should hurry up & stop pretending we want to do anything ourselves, so we can speed up getting to our eventual destiny of a full time holiday destination for American, Chinese and Russian tourists. And mind you, that is the _best_ outcome I can see right now. https://therecord.media/spain-awards-contracts-huawei-intelligence-agency-wiretaps
eprint
eprint@ioc.exchange#eprint Replication of Quantum Factorisation Records with an 8-bit Home Computer, an Abacus, and a Dog by Peter Gutmann, Stephan Neuhaus (https://ia.cr/2025/1237)
chiefpie
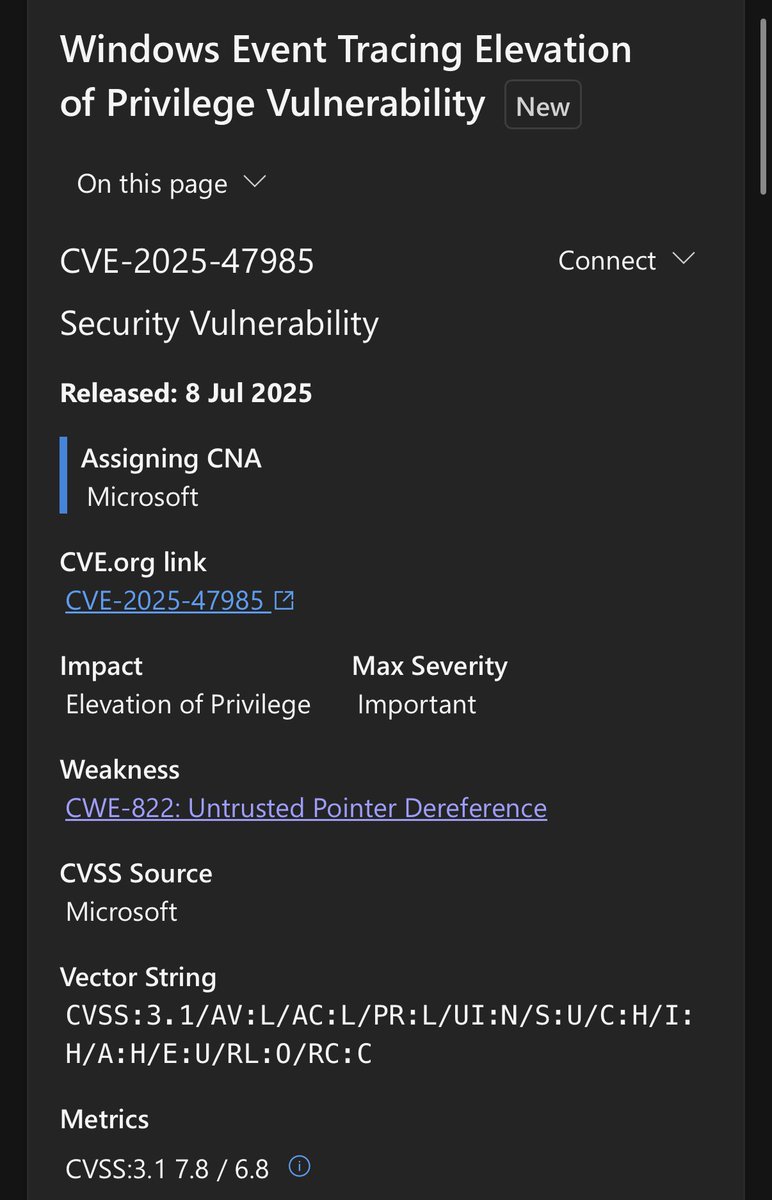
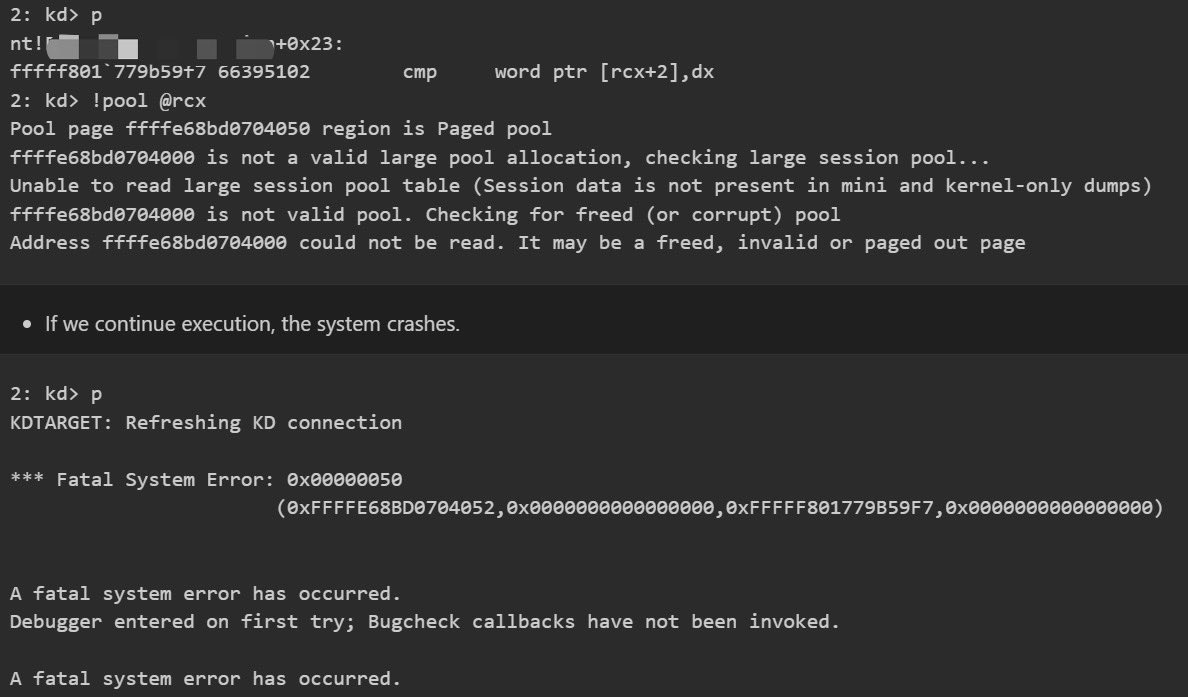
cplearns2h4ck@bird.makeupSome of my bugs in Windows Kernel ETW have been fixed by MSRC this month.
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-47985
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-49660
These bugs are triggered from NTOS syscall.
algernon ludd can't think of a funny name atm
algernon@come-from.mad-scientist.clubGetting started with iocaine is now online.
From nothing to running iocaine + Caddy with ai.robots.txt's robots.json and a few metrics as a starting point.
Contains #Roto, #Lua, and #Fennel - and a few tests too, for each.
Greg Linares (Laughing Mantis)
laughing_mantis@bird.makeupTruly humbled to share I had the honor of being a guest on the legendary @darknetdiaries. We talked about some wild stories, the epic screw ups, and others adventures. Really grateful for the chance to tell a few tales and hope it resonates with some