Posts
2501Following
650Followers
1469buherator
buheratorhttps://karmainsecurity.com/KIS-2025-03
buherator
buheratorhttps://blog.himanshuanand.com/posts/discovered-a-libpng-vulnerability-11-years-after-it-was-patched/
buherator
buheratorhttps://www.netspi.com/blog/technical-blog/network-pentesting/remote-code-execution-sailpoint-iqservice/
buherator
buheratorhttps://slcyber.io/assetnote-security-research-center/abusing-windows-net-quirks-and-unicode-normalization-to-exploit-dnn-dotnetnuke/
astralia
astralia@infosec.exchangeComputer engineer interested on #cybersecurity and #reverseengineering looking for job.
Maybe I do not have the skills, but one thing i can say is that I’m pretty good on getting my shit done, even if is something new to me.
#jobsearch
HN Security
hnsec@infosec.exchangeIn our last blog post, our colleague Gianluca shares the story of a lucky discovery: a bug initially spotted during a routine assessment turned out to be a high impact vulnerability in Microsoft Graph API — earning a $3,000 bounty.
John Carlos Baez
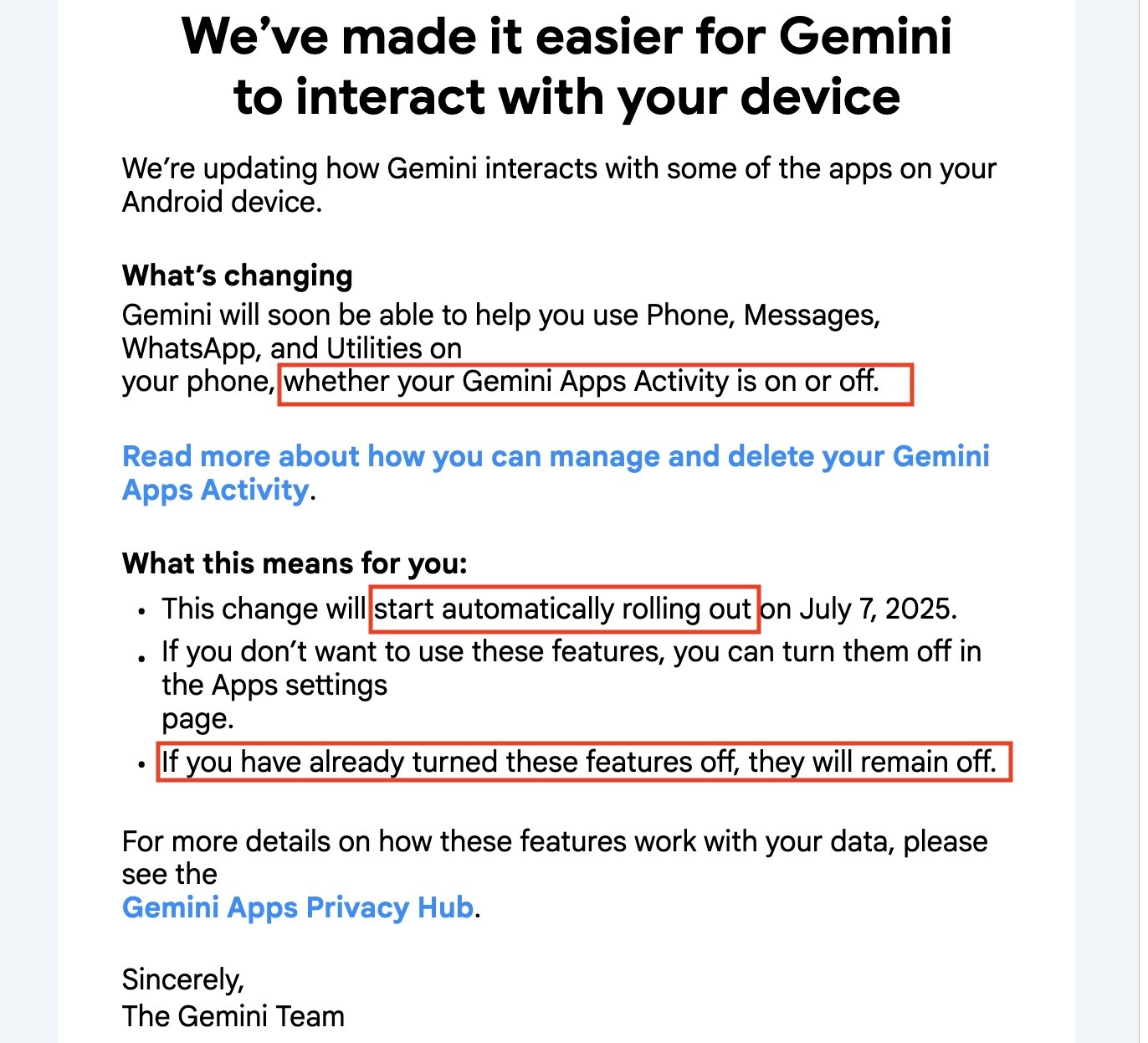
johncarlosbaez@mathstodon.xyzIf you've turned it off it will stay off...
... but it will be on.
Gabriele Svelto
gabrielesvelto@mas.toIf you have an Intel Raptor Lake system and you're in the northern hemisphere, chances are that your machine is crashing more often because of the summer heat. I know because I can literally see which EU countries have been affected by heat waves by looking at the locales of Firefox crash reports coming from Raptor Lake systems.
buherator
buheratorinternetarchive
internetarchive@mastodon.archive.orgWhat does the web mean to you?
As we celebrate 1 trillion webpages archived in the Wayback Machine, we want to hear your story. Why does preserving the web matter to you?
📝 Share your story now: https://forms.gle/c3XqotHUToKe2pZw5
Soatok Dreamseeker
soatok@furry.engineerChecklists Are The Thief Of Joy
I have never seen security and privacy checklists used for any other purpose but deception. After pondering this observation, I'm left seriously doubting if comparison checklists have any valid use case except to manipulate the unsuspecting. But before we get into that, I'd like to share why we're talking about this today. Recently, another person beat me to the punch of implementing MLS (RFC 9420) in TypeScript.
http://soatok.blog/2025/07/07/checklists-are-the-thief-of-joy/
Charlie Balogh
chainq@mastodon.socialSoftware dependencies are subject to Brandolini's law (a.k.a the Bullshit Asymmetry Principle), which states:
"The amount of energy needed to refute bullshit is an order of magnitude bigger than that needed to produce it."
However, I also find that in any software project, the amount of effort needed to get rid of an external dependency is an order of magnitude bigger than it took to add it.
Conclusion: most software is largely made of bullshit.
eShard
eshard@infosec.exchangePost-quantum crypto resists quantum computers, not physical attacks.
On July 10, we're live with PQShield to show how side-channel and fault injection techniques still break schemes like ML-KEM, and how to protect your implementations.
Register now:
🔵 11am CEST: https://pqshield.zoom.us/webinar/register/WN_GUBZIV41QDGiROlkbuUsPg#/registration
🔵 6pm CEST: https://pqshield.zoom.us/webinar/register/WN_6WZOefg3T06jQW6ind_bqw#/registration
#pqc #postquantumcryptography #sidechannel #faultinjection #hardware #hardwarehacking #hardwaresecurity
RPGPGM
rpgpgm@mastodon.socialNew IBM Redbook about modernization on the IBM Power and IBM i was published on May 20, 2025.
💙 #IBMi #rpgpgm #IBMChampion
https://www.rpgpgm.com/2025/07/new-modernization-techniques-redbook.html
OpenSecurityTraining2
OpenSecurityTraining2@infosec.exchange📢Call for beta testers!📢
Microsoft mandated the presence of Trusted Platform Modules for new Windows 11 machines. Now's a good time for security experts & hackers to familiarize themselves with what TPMs are, and what they can (and can't) add to the security of a system. You can do that by joining the beta test of the OST2 class "Trusted Computing 2202: TPM 2.0 Programming using Python and the tpm2-pytss libraries" by William Roberts (maker of the tpm2-pytss library) which will start July 14th and run for 1 month. It will take ~8 hours to complete.
https://forms.gle/cbBazgq7m24QSxTD6
PSConfEU
psconf.eu@bsky.brid.gy💣 CLIXML #deserialization in #PowerShell isn't harmless…
At #PSConfEU 2025, Alexander Andersson showed how it enables:
✔ Lateral movement
✔ Privilege escalation
✔ Guest-to-host VM breakouts
🎟️ Early bird 2026 tickets → psconf.eu
#Security #CLIXML
- YouTube
buherator
buheratorhttps://labs.watchtowr.com/how-much-more-must-we-bleed-citrix-netscaler-memory-disclosure-citrixbleed-2-cve-2025-5777/
buherator
buheratorhttp://addxorrol.blogspot.com/2025/07/a-non-anthropomorphized-view-of-llms.html