Posts
3368Following
712Followers
1580
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Interesting Git repos of the week:
Strategy:
* https://github.com/timb-machine/security-research-governance-toolkit - I started releasing Portcullis' old security research governance toolkit
Detection:
* https://github.com/sandflysecurity/sandfly-forensic-scripts - @SandflySecurity have release scripts for collecting Linux artefacts
Exploitation:
* https://github.com/stealth/injectso - @steaith demonstrates how to inject .so files into running processes at will
* https://github.com/NeffIsBack/wsuks - have you ever wanted to MITM WSUS?
Data:
* https://github.com/public-api-lists/public-api-lists - does what it says on the tin
Development:
* https://github.com/sapdragon/syscalls-cpp - headers for direct syscall invocation
Sam Stepanyan  🐘
🐘
securestep9@infosec.exchange
Actively exploited vulnerability in CVE-2024-54085 in AMI MegaRAC gives attackers extraordinary control over server fleets by allowing a remote attacker to create an admin account without any authentication:
👇
https://arstechnica.com/security/2025/06/active-exploitation-of-ami-management-tool-imperils-thousands-of-servers/
Tom Schuster
evilpie@hachyderm.ioWhat's not to love about third-party software injecting itself into Firefox and causing crashes in the Rust standard library?
Sam Stepanyan  🐘
🐘
securestep9@infosec.exchange
#CISCO: Critical severity CVSS 10 CVE-2025-20281 and CVE-2025-20282 vulnerabilities allow an unauthenticated, remote attacker to execute arbitrary code on the underlying operating system as root! Updates released - patched now:
👇
https://thehackernews.com/2025/06/critical-rce-flaws-in-cisco-ise-and-ise.html
Stefan Lindbohm
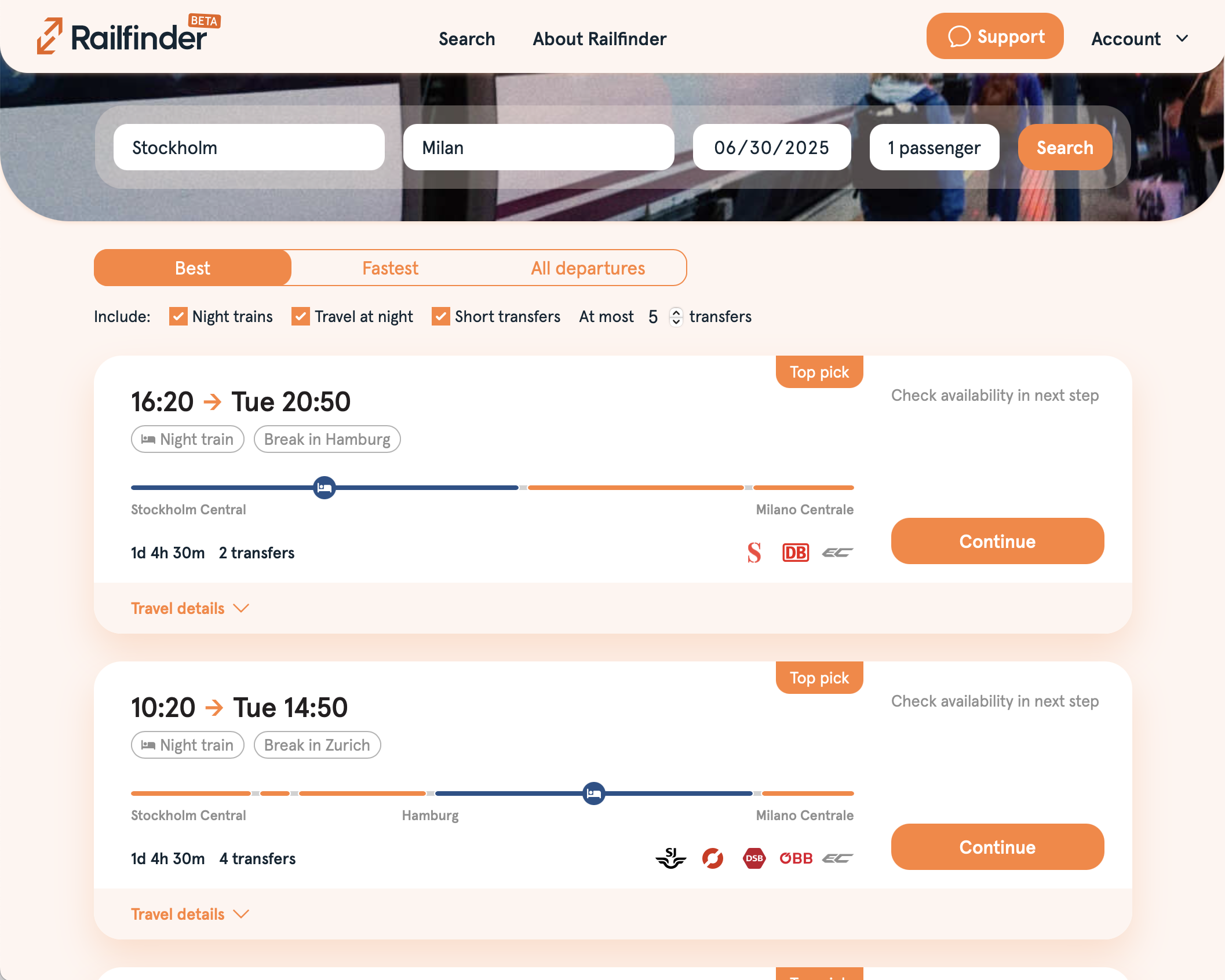
stefanlindbohm@mastodon.socialToday we’re quietly (and finally!) opening up Railfinder to the public! This is our beta version and - hopefully - the first step towards that one booking site for trains across Europe that we all dream of.
Lots of work has gone into this and equally lots still to do before reach that vision, but if you’d like to try what we’be built you can now just go to https://www.railfinder.eu and have a go!
Any and all feedback more than welcome 🙏
Kevin Beaumont
GossiTheDog@cyberplace.socialHelp request. My brother has Stage 4 colorectal cancer.
His life insurance has refused to pay out on a technicality, meaning he and his loved ones cannot afford the mortgage on their home.
I've never asked for anything in return for infosec stuff, but if you have anything spare, please chuck it this direction instead:
 radare
radare 
radareorg@infosec.exchange
🚀 Ghidra users! Looking for more power & flexibility in your reverse engineering workflow? Try ghidra-r2web — the plugin that lets you attach multiple Radare2 instances to your main #Ghidra session!
We need ideas, bug reports, feature requests and contributors to make this plugin shine! https://github.com/radareorg/ghidra-r2web
CFG Bot 🤖
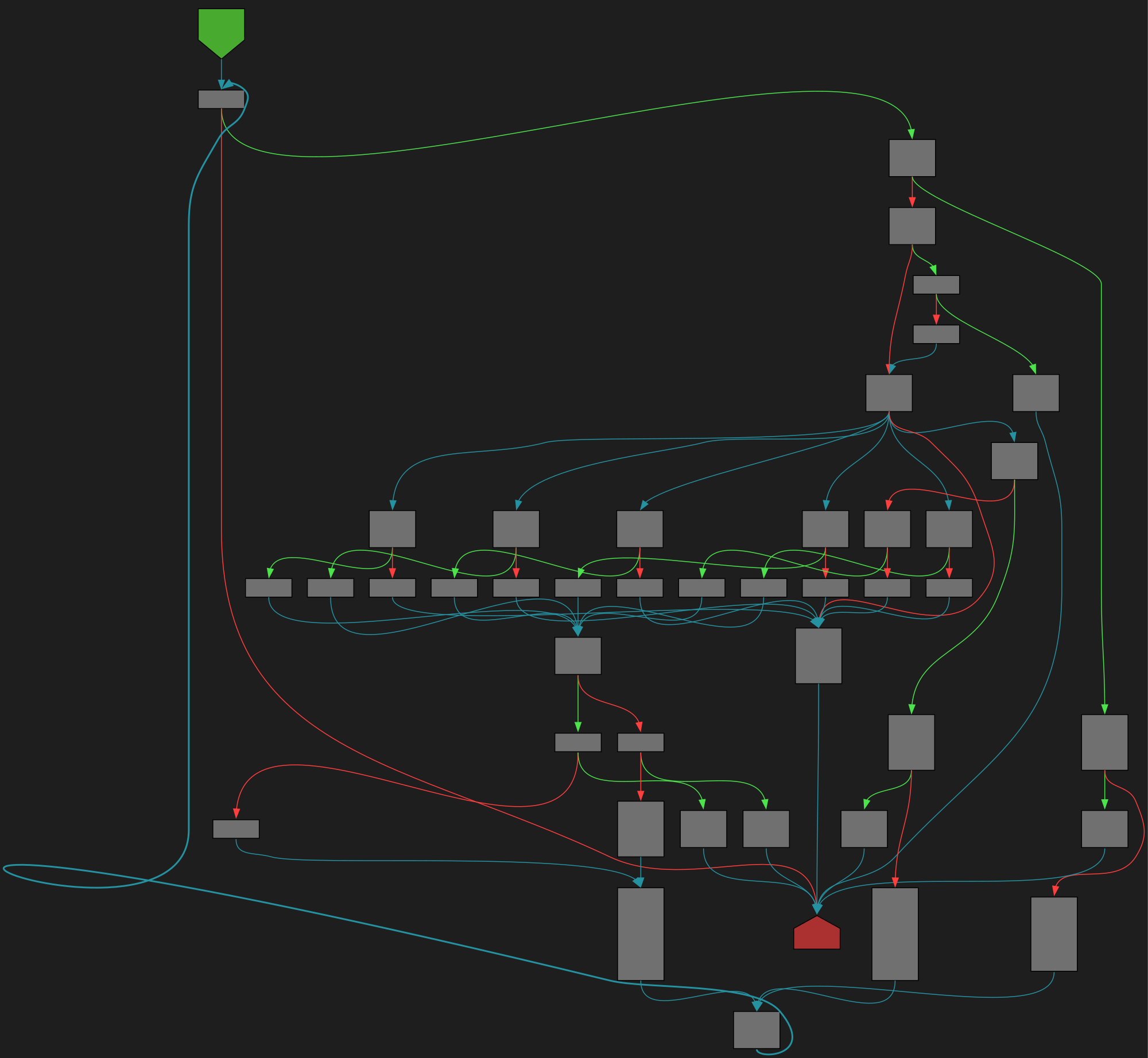
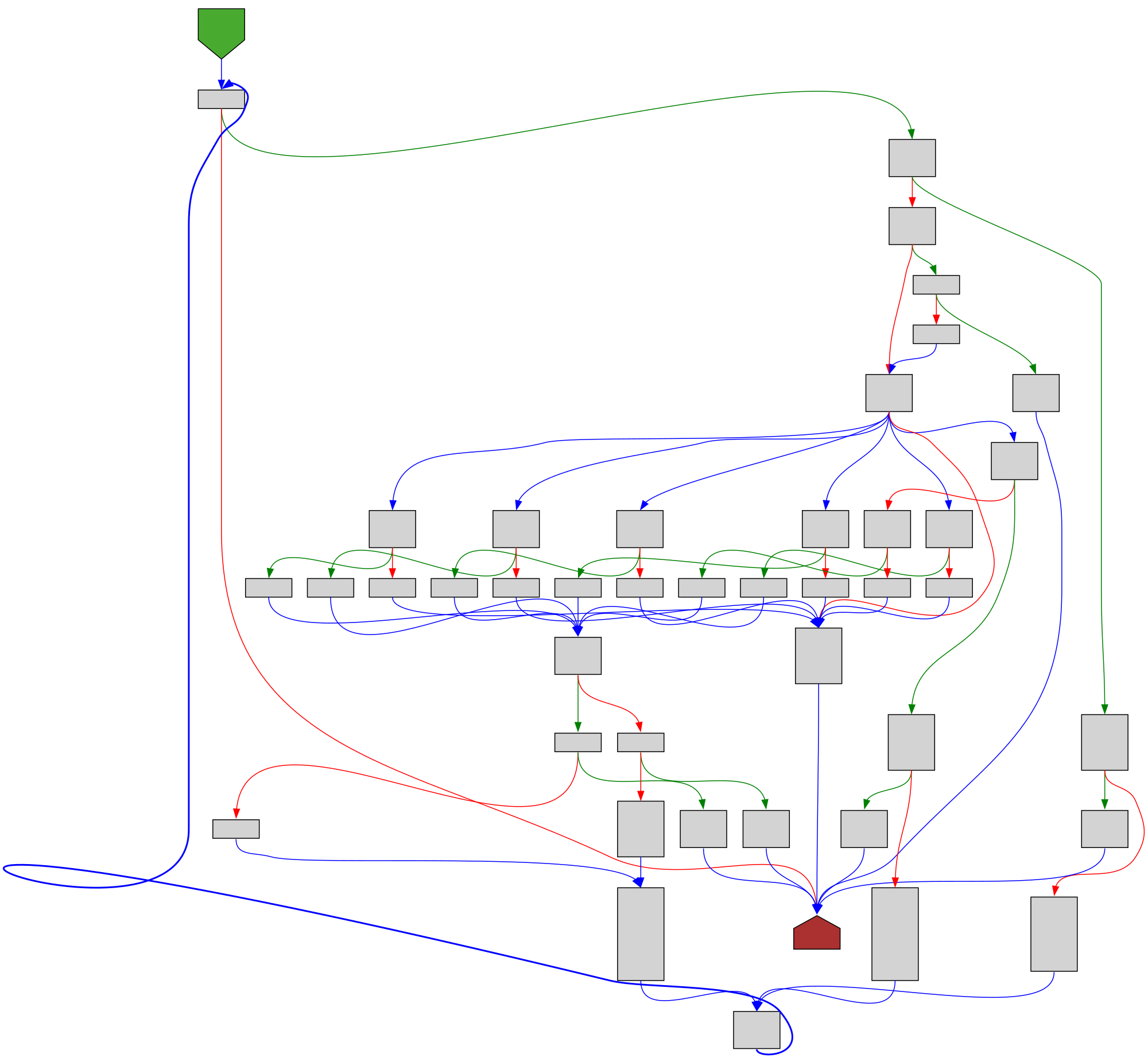
cfgbot@mastodon.socialProject: kubernetes/kubernetes https://github.com/kubernetes/kubernetes
File: vendor/golang.org/x/text/encoding/japanese/eucjp.go:124 https://github.com/kubernetes/kubernetes/blob/a62752db5110225a89a83ec844a5884413e550ff/vendor/golang.org/x/text/encoding/japanese/eucjp.go#L124
func (eucJPEncoder) Transform(dst, src []byte, atEOF bool) (nDst, nSrc int, err error)
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fkubernetes%2Fkubernetes%2Fblob%2Fa62752db5110225a89a83ec844a5884413e550ff%2Fvendor%2Fgolang.org%2Fx%2Ftext%2Fencoding%2Fjapanese%2Feucjp.go%23L124&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fkubernetes%2Fkubernetes%2Fblob%2Fa62752db5110225a89a83ec844a5884413e550ff%2Fvendor%2Fgolang.org%2Fx%2Ftext%2Fencoding%2Fjapanese%2Feucjp.go%23L124&colors=light
Elena Rossini ⁂
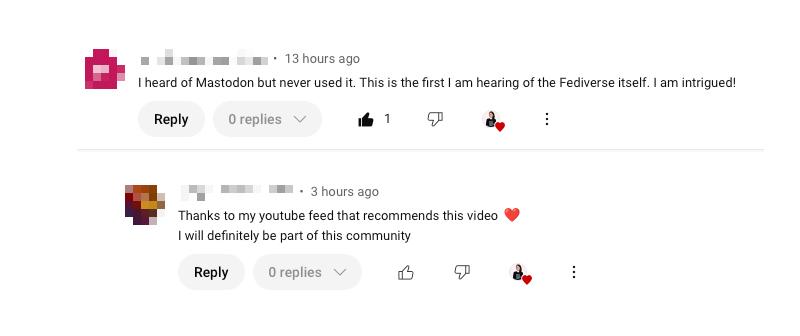
_elena@mastodon.socialGood morning Fedi friends!
My decision to upload the Fedi promo video to YouTube 2 weeks ago was really controversial.
@randahl posted a nice message about the video & encouraged his followers to like / comment on it so the YouTube algorithm would serve it to more people. He was inundated by hostile comments for days. Sorry Randahl!
Well, exhibit A of why this was a good decision in hindsight (see pic).
How else are people going to hear about the Fediverse?
As always thank for the support ❤️
buherator
buheratorhttps://github.com/radareorg/ghidra-r2web/releases/tag/ghidra-11.4
I cut down the release to support the last 3 minor Ghidra versions (11.4, 11.3.x, 11.2.y), if you need supoort for older versions, please let us know by opening an Issue!
#Ghidra #radare2
buherator
buheratorhttps://msrc.microsoft.com/blog/2025/06/redirectionguard-mitigating-unsafe-junction-traversal-in-windows/
Lukasz Olejnik
LukaszOlejnik@mastodon.socialCyberattack caused the first confirmed patient death due to a Russian cybercriminal group ransomware tool written in Rust. It disrupted Synnovis pathology services in 2024, delaying critical blood test results. Investigation found 170 patients harmed total: 2 major harm cases, 11 moderate harm, 120 minor harm incidents from the breach. https://news.sky.com/story/patient-death-linked-to-cyber-attack-on-nhs-hospital-trust-says-13388485
Michael Veale
mikarv@someone.elses.computerif you run a child abuse helpline, perhaps don’t install Meta and Snap pixels. Recent fine announced earlier this month from the Norwegian DPA https://gdprhub.eu/index.php?title=Datatilsynet_(Norway)_-_NO_-_DPA_-_24/01055-10&mtc=today
dragosr
dragosr@chaos.socialCritical Meshtastic Vulnerability:
CVE-2025-52464: Meshtastic 2.5.0–2.6.10 shipped cloned or low-entropy X25519 keys via vendor pre-flash + weak RNG.
Collisions let attackers decrypt LoRa direct-msgs, replay/forge admin RPCs, hijack nodes; no forward secrecy, so old captures stay cleartext.
Firmware 2.6.11 defers key-gen, hardens entropy, flags compromised pairs.
I learned something today: Google's Gemini "AI" on phones accesses your data from "Phones, Messages, WhatsApp" and other stuff whether you have Gemini turned on or not. It just keeps the data longer if you turn it on. Oh, and lets it be reviewed by humans (!) for Google's advantage in training "AI" etc.
But this only came to my attention because of an upcoming change: it's going to start keeping your data long-term even if you turn it "off": "#Gemini will soon be able to help you use Phone, #Messages, #WhatsApp, and Utilities on your phone, whether your Gemini Apps Activity is on or off."
This is, of course, a #privacy and #security #nightmare.
If this is baked into Android, and therefore not removable, I'd have to say I'd recommend against using Android at all starting July 7th.
#spyware #AI #LLM #Google #spying #phone #Android #private #data
Eric Woodruff [MS MVP] 
ericonidentity@infosec.exchange
At @WEareTROOPERS I dropped new research on #nOAuth, an abuse of #EntraID that allows you to spoof users in vulnerable SaaS applications.
The attack is still alive and well.
You can read all about it here:
https://www.semperis.com/blog/noauth-abuse-alert-full-account-takeover
Project Zero Bot
p0botMacOS Sandbox Escape via Double Free in coreaudiod/CoreAudio Framework
https://project-zero.issues.chromium.org/issues/406271181
CVE-2025-31235