Posts
2734Following
681Followers
1505Malicious Actor
algernon@come-from.mad-scientist.club@buherator No, fel is huztam! Rogton 3 cimen is, mert nem tudtam donteni.
Ha lenne hajam, akkor most csinalnek magamnak jofajta punk frizurat. 
BlueSCSI
BlueSCSI@hachyderm.iobuherator
buheratorThis summer started off esp. bad, while official online services allowing the tracking of delays suspiciously started to disappear.
Train enthusiasts however built an unofficial website that showed accurate info about the position and delays of the trains based on scraped data.
Then the Minister of Transportation accused these guys of phishing (he pbbly doesn't know what that means), DoS and of course conspiring the opposition party, so the site was voluntarily taken down...
...but the code is open source, so now we have multiple sites with the same functionality :D
https://github.com/iben12/holavonat
#Hungary #StreisandEffect
~swapgs
swapgs@infosec.exchangePre-auth RCE in CentOS Web Panel (CVE-2025-48703) found by the friends at Fenrisk. This is beyond madness that Shodan finds 200k of these exposed publicly.
(this post is sponsored by strace®, because no one cares about ionCube)
Alan Coopersmith
alanc@hachyderm.ioFinally published today the second blog I'd promised for the #OracleSolaris 11.4.81 CBE release last month:
https://blogs.oracle.com/solaris/post/whats-new-in-the-solaris-modular-debugger-mdb-in-the-oracle-solaris-11481-cbe
A very deep dive into a narrow topic - what's changed in the Solaris Modular Debugger (mdb) since the previous CBE release in 2022. @cgerhard and others have put an impressive amount of work into making debugging easier and better for the users of this tool.
[realhackhistory@home]#
realhackhistory@chaos.socialHat tip to thegrugq for featuring this in his newsletter, a 1991 video of Italian hackers purporting to show them hacking a U.S. military system over x25. Has a real gonzo Max Headroom broadcast signal intrusion vibe with the masks & just general weird vibes, love it.
https://www.youtube.com/watch?v=43FyQlaA6YY
Tina
Tina@mastodon.ieDear Fedi,
For 3 years, I've been working with friends from the #FOSS world as a team of freelancers and it's been great: we love what we do and our clients are happy and stay with us for years.
But the terrible state of the world has badly affected our clients financially, and we find ourselves suddenly in need of more #work
We focus on systems design, development, and administration. We offer SRE-level quality and processes for companies that cannot afford a whole #SRE team
Boosts welcomed
buherator
buheratorhttps://www.youtube.com/watch?v=Z-keHkcTZD4
Also, lots of samples.
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250618-00/?p=111281
buherator
buheratorbuherator
buheratorc3voc releases
c3voc_releases@chaos.socialProject Vicigol - Reverse-engineering a 28-bit RISC CPU has been released on media.ccc.de and YouTube #gpn23 #HardwareandMaking #ZKMKubus #gpn23eng https://media.ccc.de/v/gpn23-144-project-vicigol-reverse-engineering-a-28-bit-risc-cpu https://www.youtube.com/watch?v=5I1OIrXnM1Q https://cfp.gulas.ch/gpn23/talk/KBQBE7/
Harry Sintonen
harrysintonen@infosec.exchangeInsecure defaults can lead to surprises. When creating FIFO sockets with systemd, be sure to note that SocketMode defaults to 0666 - that is world readable and writable. That is: any local user can communicate with the FIFO. If your FIFO is used to perform privileged operations you must ensure that either the FIFO file itself is located in secured location or set SocketMode to stricter value.
I spotted one such insecure use in cloud-init: the hotplug FIFO was world writable. This is CVE-2024-11584 and fixed in cloud-init 25.1.3.
The commit fixing this is in https://github.com/canonical/cloud-init/pull/6265
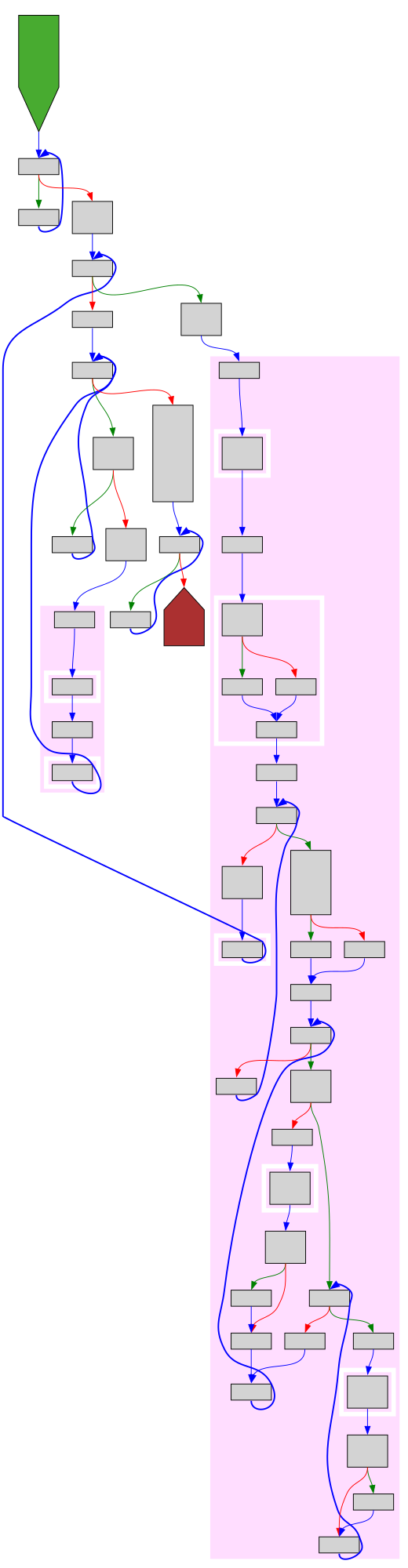
CFG Bot 🤖
cfgbot@mastodon.socialProject: pypy/pypy https://github.com/pypy/pypy
File: rpython/rlib/parsing/deterministic.py:217 https://github.com/pypy/pypy/blob/9abbb4f358a5c308aefb85652a229cc98f899e13/rpython/rlib/parsing/deterministic.py#L217
def make_code(self):
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fpypy%2Fpypy%2Fblob%2F9abbb4f358a5c308aefb85652a229cc98f899e13%2Frpython%2Frlib%2Fparsing%2Fdeterministic.py%23L217&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fpypy%2Fpypy%2Fblob%2F9abbb4f358a5c308aefb85652a229cc98f899e13%2Frpython%2Frlib%2Fparsing%2Fdeterministic.py%23L217&colors=light