Posts
3368Following
712Followers
1580Allele Security Intelligence
alleleintel@infosec.exchangeWe wrote a blog post about a Linux kernel vulnerability we reported to Red Hat in July 2024. The vulnerability had been fixed upstream a year before, but Red Hat and derivatives distributions didn't backport the patch. It was assigned the CVE-2023-52922 after we reported it.
The vulnerability is a use-after-free read. We could abuse it to leak the encoded freelist pointer of an object. This allows an attacker to craft an encoded freelist pointer that decodes to an arbitrary address.
It also allows an attacker to leak the addresses of objects from the kernel heap, defeating physmap/heap address randomization.These primitives facilitate exploitation of the system by providing the attacker with useful primitives.
Additionally, we highlighted a typical pattern in the subsystem, as two similar vulnerabilities had been discovered. However, before publishing the blog post, we noticed that the patch for this vulnerability doesn't fix it. We could still trigger the use-after-free issue.
This finding confirms the point raised by the blog post. Furthermore, we discovered another vulnerability in the subsystem. An out-of-bounds read. We've reported them, and these two new vulnerabilities were already patched. A new blog post about them will be written.
Use-after-free vulnerability in CAN BCM subsystem leading to information disclosure (CVE-2023-52922)
Programming Quotes
programming_quotes@mastodon.socialA human being should be able to change a diaper, plan an invasion, butcher a hog, conn a ship, design a building, write a sonnet, balance accounts, build a wall, set a bone, comfort the dying, take orders, give orders, cooperate, act alone, solve equations, analyze a new problem, pitch manure, program a computer, cook a tasty meal, fight efficiently, die gallantly. Specialization is for insects.
— Robert A. Heinlein
eShard
eshard@infosec.exchangeWinDBG vs esReverse: same concept (time travel debugging), very different scope.
We break down the differences in our blog: https://eshard.com/posts/difference-between-windbg-and-esreverse
Frederik Braun �
freddy@security.plumbingThe fact that these apps can launch local web servers to collude with tracking scripts and completely de-anonymize the users is wild. It's appalling. But here is what's not new:
Native apps from huge advertising companies (née "social" networks) are nothing but a slot machine where you pay with your data.
Get off these apps. Remove them now. Best yet, get off these addictive shit sites. And if you can't, visit them in at truly privacy preserving browser. 2/3.
buherator
buheratorhttps://aoli.al/blogs/jdk-bug/
CFG Bot 🤖
cfgbot@mastodon.socialProject: kubernetes/kubernetes https://github.com/kubernetes/kubernetes
File: staging/src/k8s.io/api/core/v1/generated.pb.go:72936 https://github.com/kubernetes/kubernetes/blob/a62752db5110225a89a83ec844a5884413e550ff/staging/src/k8s.io/api/core/v1/generated.pb.go#L72936
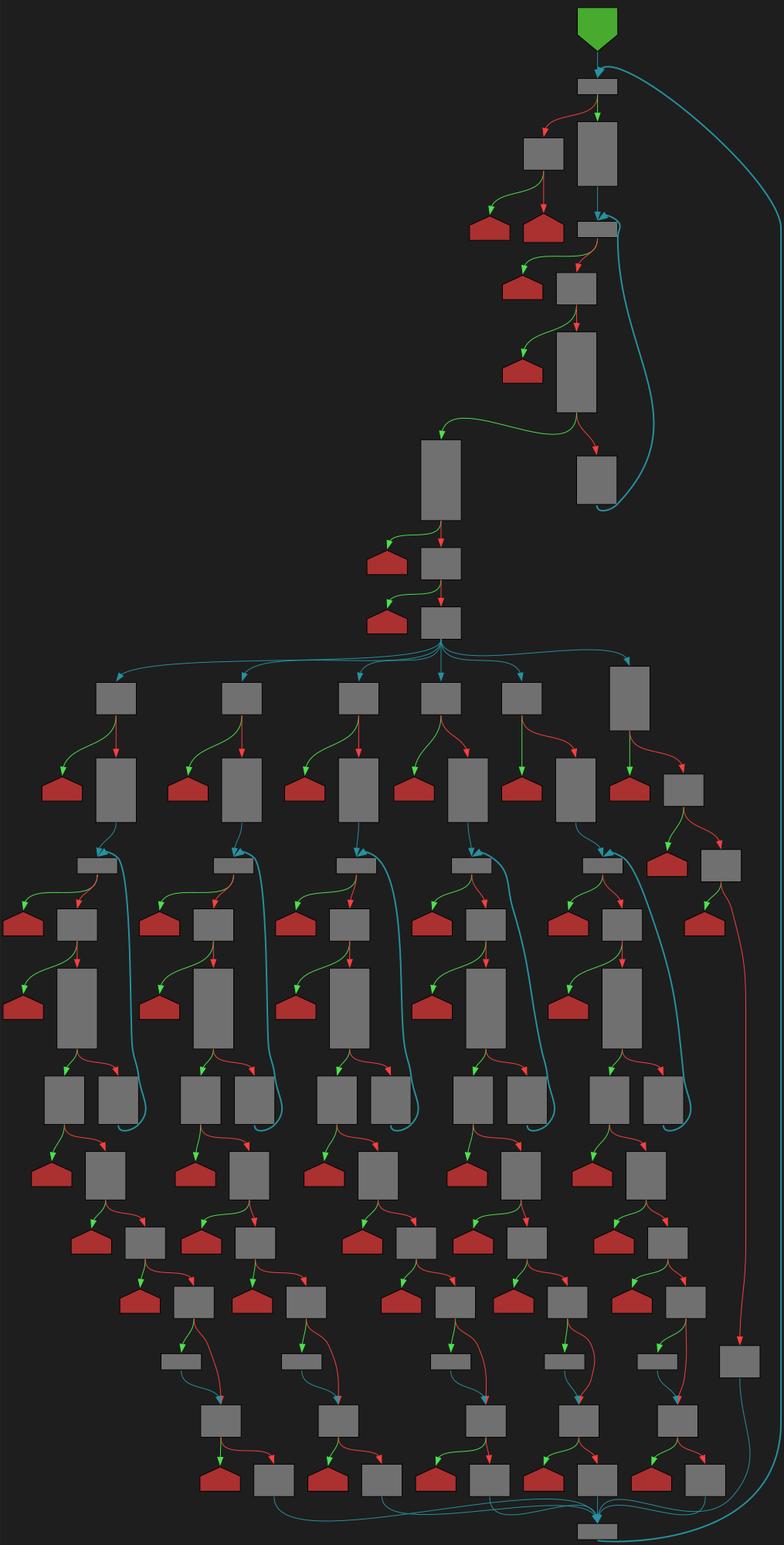
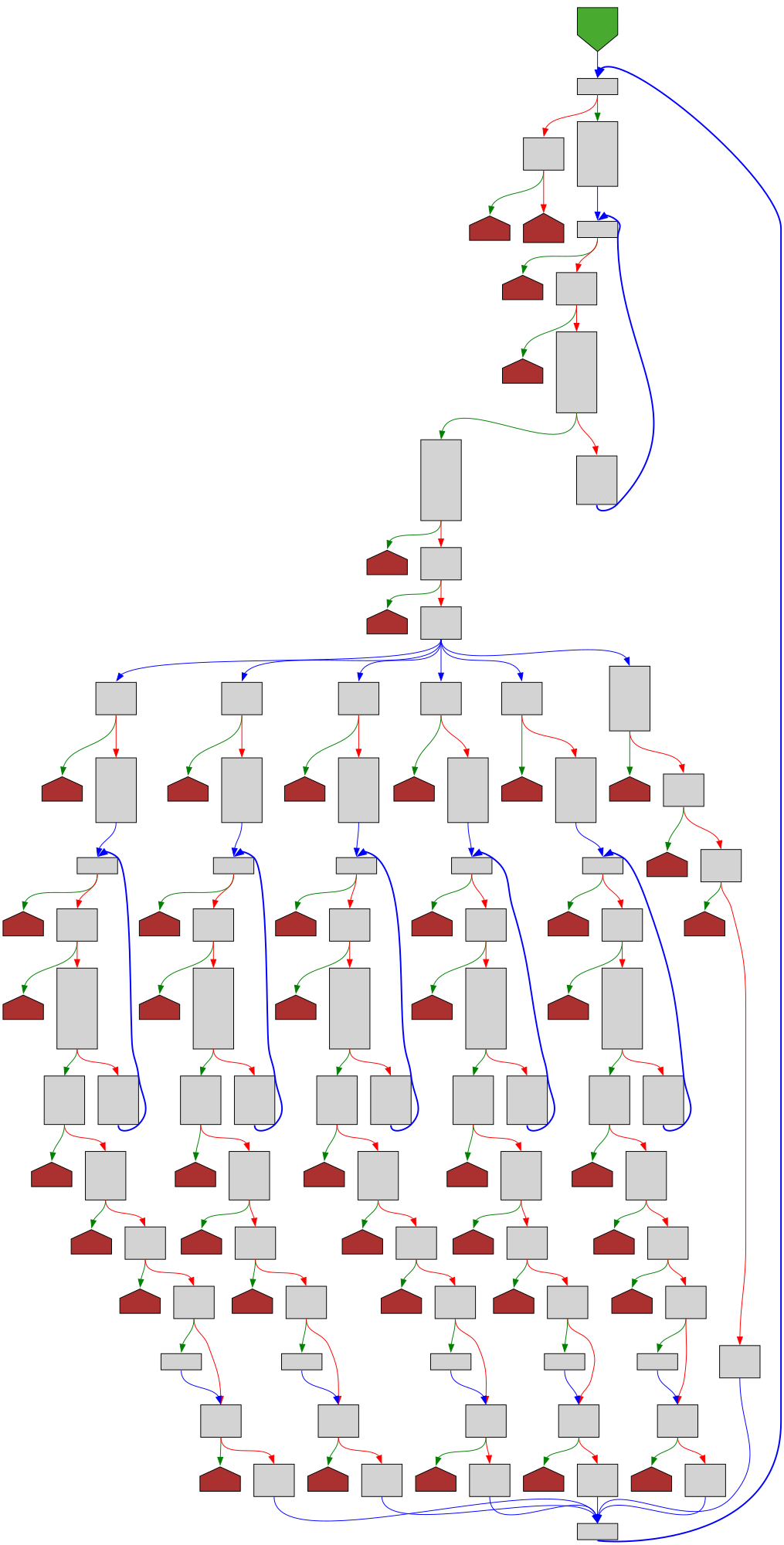
func (m *VolumeProjection) Unmarshal(dAtA []byte) error
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fkubernetes%2Fkubernetes%2Fblob%2Fa62752db5110225a89a83ec844a5884413e550ff%2Fstaging%2Fsrc%2Fk8s.io%2Fapi%2Fcore%2Fv1%2Fgenerated.pb.go%23L72936&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fkubernetes%2Fkubernetes%2Fblob%2Fa62752db5110225a89a83ec844a5884413e550ff%2Fstaging%2Fsrc%2Fk8s.io%2Fapi%2Fcore%2Fv1%2Fgenerated.pb.go%23L72936&colors=light
buherator
buheratorhttps://xania.org/202506/how-compiler-explorer-works
#fromBsky
Simple Sabotage Field Manual
simple_sabotage@mastodon.socialWhen you go to the lavatory, spend a longer time there than is necessary.
buherator
buheratorbuherator
buheratorbuherator
buheratorPravda has a story about Stalin visiting the fields at the countryside:
- How are we doing, how are we doing? - asked Comrade Stalin, jokingly
- We're fine, we're fine - replied the workers, jokingly
Łukasz 
maldr0id@infosec.exchange
Communist Poland was exceptionally good at making fun of secret police and egomaniacal leaders.
If my American friends need some good authoritarian jokes so that they can keep their spirits up for the long run I can suggest some!
hanno
hanno@mastodon.socialIn case anyone here has connections with the Python team: can you please tell them to update their docs on XML security? The way it is is quite misleading, and it's been annoying me for a while. I raised this a while ago in their issue tracker, but it got no reaction whatsoever. https://github.com/python/cpython/issues/127502 🧵
Computer History Museum 🇸🇮
muzej@mastodon.socialPHP just turned 30! 🎉 Did you create guestbooks for your website like the early users of the language? 📜 Do you remember technologies like PHP-Nuke, phpBB, or browsing vBulletin forums? 💻
Jael Koh
_jaelkoh@bird.makeupThe slides for @offensive_con talk "Hunting for overlooked cookies in Windows 11 KTM and baking exploits for them" by @saidelike and I are here:
https://docs.google.com/presentation/d/1M_ziQt6rZA01ghsv0qo7lhqyOLIZYNnV-qjHWun6A1g/edit?usp=sharing
Zack Weinberg
zwol@hackers.townanother day, another binary file format with a badly designed magic number
not gonna call it out specifically but here are some RFC2113 MUSTs for magic number design:
MUST be the very first N bytes in the file
MUST be at least four bytes long, eight is better
MUST include at least one byte with the high bit set
MUST include a byte sequence that is invalid UTF-8
SHOULD include a zero byte, but you can usually get away with having that be part of the overall version number that immediately follows the magic number (did I mention that you really SHOULD put an overall version number right after the magic number, unless you know and have documented exactly why it's not necessary, e.g. PNG?)
good examples:
- PNG
- ELF
bad examples:
- GIF
- PE