Posts
3381Following
713Followers
1580eShard
eshard@infosec.exchangeOur journey with our #iOS emulator continues.
We show how we reached the home screen, enabled multitouch, unlocked network access, and started running real apps 👉 https://eshard.com/posts/emulating-ios-14-with-qemu-part2
Command injection, SQLi, and hardcoded creds in Infoblox NETMRI. tsk tsk
https://support.infoblox.com/s/article/Infoblox-NetMRI-is-vulnerable-to-CVE-2025-32814
https://support.infoblox.com/s/article/Infoblox-NetMRI-is-vulnerable-to-CVE-2025-32813
https://support.infoblox.com/s/article/Infoblox-NetMRI-is-vulnerable-to-CVE-2025-32815
And we have a write-up now for these Infoblox NetMRI vulns.
https://rhinosecuritylabs.com/research/infoblox-multiple-cves/
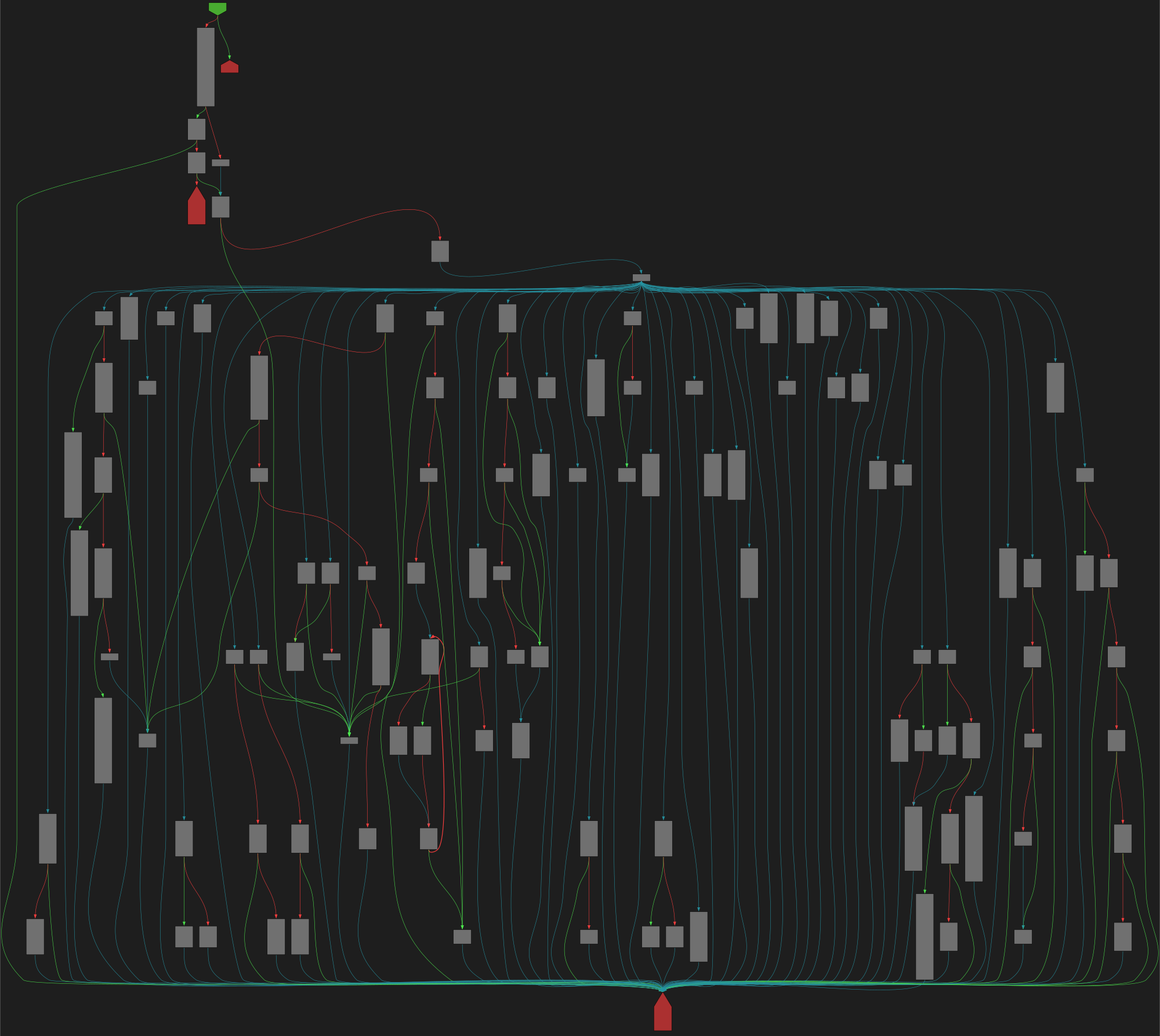
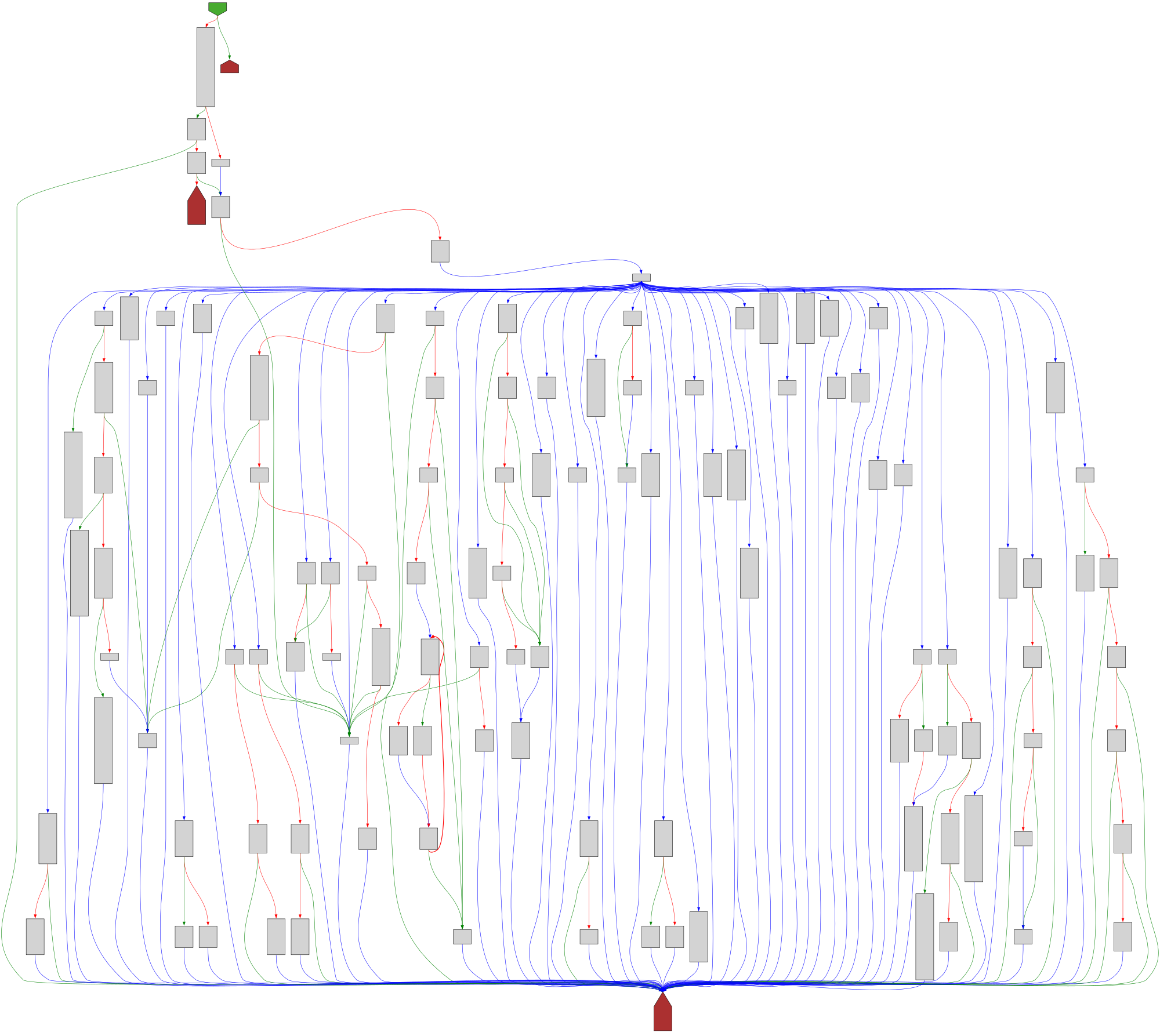
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 00478ea0
ssl3_ctrl
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00478ea0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00478ea0.json&colors=light
buherator
buherator(I just wrestled with some code that swear to God was optimized for the minimal number of semicolons...)
The DFIR Report
TheDFIRReport@infosec.exchange🎯 THIS SATURDAY: DFIR Labs CTF 🎯
⏰ June 7 | 1630–2030 UTC
🔗 Register Now → https://dfirlabs.thedfirreport.com/ctf
🚀 DFIR Labs CTF is back!
💥 Only $9.99 to join
💥 Choose Elastic or Splunk
💥 Access a brand-new, unreleased case
💥 Top 5 get invited to join The DFIR Report team!
📣 Hear from past participants:
⭐ “Real case makes it different!”
🚀 “Great hands-on learning experience”
💯 “Excellent CTF, super responsive and realistic”
Don’t miss your chance to level up with real-world incident response challenges.
Marcel Waldvogel
marcel@waldvogel.familyBoth #Yandex and #Meta used obfuscation techniques to hide that the traffic occured and/or that the apps were listening to these requests:
➡️ Meta traffic was using #WebRTC, which does not show up in the browser's developer tools
➡️ Yandex traffic looked non-local
➡️ Yandex apps started listening only after several days
BTW: Apparently, Meta stopped doing this yesterday. But they probably still have the mapping DB.
All the details by the researchers here.
https://localmess.github.io/
buherator
buheratorhttps://telex.hu/techtud/2025/06/03/hekkertamadas-paprika-csoport-erettsegi-adatbazis-masolas-oktatasi-hivatal
Wonder if perpetrators are in fact Hungarian (as the name suggests), or just using some LLM translator?
Alexandre Borges
alexandreborges@infosec.exchangeCisco IOS XE WLC Arbitrary File Upload Vulnerability (CVE-2025-20188) Analysis:
#cybersecurity #xxe #infosec #cve #vulnerability #threathunting #exploitation
Karl Voit 
publicvoit@graz.social
Every project should have a "cursed"-page like that: 😆
"Cursed knowledge we have learned as a result of building #Immich that we wish we never knew."
https://immich.app/cursed-knowledge/
🤓
Samuel Groß
saelo@chaos.socialhttps://chromereleases.googleblog.com/2025/06/stable-channel-update-for-desktop.html
Some cool things to note though: (1) the bug was mitigated via finch kill switch (https://developer.chrome.com/docs/web-platform/chrome-finch) one day after the report from TAG (2) we also fixed the V8 Sandbox bypass within 7 days even though it's not yet considered a security boundary.
And I've also updated our V8 Exploit Tracker sheet now: https://docs.google.com/document/d/1njn2dd5_6PB7oZGTmkmoihYnVcJEgRwEFxhHnGoptLk/edit?usp=sharing (see the 2025 tab) :)
Ars Technica
arstechnica@mastodon.socialMeta and Yandex are de-anonymizing Android users’ web browsing identifiers
Abuse allows Meta and Yandex to attach persistent identifiers to detailed browsing histories.
https://arstechnica.com/security/2025/06/headline-to-come/?utm_brand=arstechnica&utm_social-type=owned&utm_source=mastodon&utm_medium=social
/r/netsec
_r_netsec@infosec.exchangeHow to build a high-performance network fuzzer with LibAFL and libdesock https://lolcads.github.io/posts/2025/05/high_performance_network_fuzzing/
buherator
buheratorbuherator
buheratorhttps://talosintelligence.com/vulnerability_reports/TALOS-2024-2123
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2124
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2126
CVE-2024-52561 CVE-2024-54189 CVE-2024-36486
Eniko Fox
eniko@mastodon.gamedev.placeIf you wanna automatically produce shit code and spend your time babysitting the lying machine then that's a you problem. I'm sure you'll make a consultant who bills out at $150/hour very happy some day. But your character flaws have nothing to do with me so keep that shit to yourself