Posts
2956Following
697Followers
1541SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchange💻 Have you read our recent publication?
Two Use After Free (UAF) vulnerabilities were discovered within Chrome’s Browser process by one of our researchers at SSD Labs: https://ssd-disclosure.com/ssd-advisory-miracleptr-sandbox/
Alex Plaskett
alexjplaskett@bird.makeupWriting a Windows ARM64 Debugger for Reverse Engineering - KoiDbg by @keowu
https://keowu.re/posts/Writing-a-Windows-ARM64-Debugger-for-Reverse-Engineering-KoiDbg/
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgI've written an unhealthy amount of words on "the cloud" and specifically Europe's woes. In the post below I tie many articles together into a hopefully useful overview. It may be good to know that nothing I write on the cloud is novel or original, I mostly hope to report things as they are. Which is scary enough already! https://berthub.eu/articles/posts/cloud-overview/
/r/netsec
_r_netsec@infosec.exchangeOne-Click RCE in ASUS’s Preinstalled Driver Software https://mrbruh.com/asusdriverhub/
lcamtuf 


lcamtuf@infosec.exchange
Sierpiński triangle? In my bitwise AND?
https://lcamtuf.substack.com/p/sierpinski-triangle-in-my-bitwise
David Gerard
davidgerard@circumstances.runStudy: Your coworkers hate you for using AI at work
https://pivot-to-ai.com/2025/05/10/your-coworkers-hate-you-for-using-ai-at-work/ - text
https://www.youtube.com/watch?v=ONx7IFkX9OE&list=UU9rJrMVgcXTfa8xuMnbhAEA - video
"Hey, we're gonna take a screenshot of your PC every five seconds to feed our AI, mmkay? Oh wait, you want a screenshot of a meeting slide? Heck no we don't want your COMPANY to sue us!"
-Microsoft, definitely
Bart Groothuis
bartgroothuis@mastodon.onlineI am surprised this isn’t getting the attention it deserves: Hungarian military intelligence is apparently mapping what the response in parts of Ukraine will be when Orban would march in with his army. Ukraine has several Hungarian populated pockets and Putin encouraged orban several times to grab that land from Ukraine. War is not a game, so this should be seriously addressed, Kaja Kallas and Mark Rutte!
buherator
buheratorhttps://intrigus.org/research/2025/04/15/fixing-decompilation-of-stack-clash-protected-binaries/
#Ghidra #BinaryNinja #ReverseEngineering
buherator
buheratorhttps://googleprojectzero.blogspot.com/2025/05/breaking-sound-barrier-part-i-fuzzing.html
Unnamed TNG skant beefcake
researchfairy@scholar.social"Wrong but plausible" is a feature and not a bug for LLMs if you're looking for a system to deploy where you can use it, say, to fine-tune insurance reimbursements to the exact dollar amount you wanted and have it produce the justifications needed to get there at an industrial scale
Nicolas Grégoire
agarri.fr@bsky.brid.gyXWiki has been compromised, and all personal wikis have been deleted. That includes mine, named XHE for "XML Hacking Encycopledia" 😢
a baby is making a sad face wh...
Binary Ninja
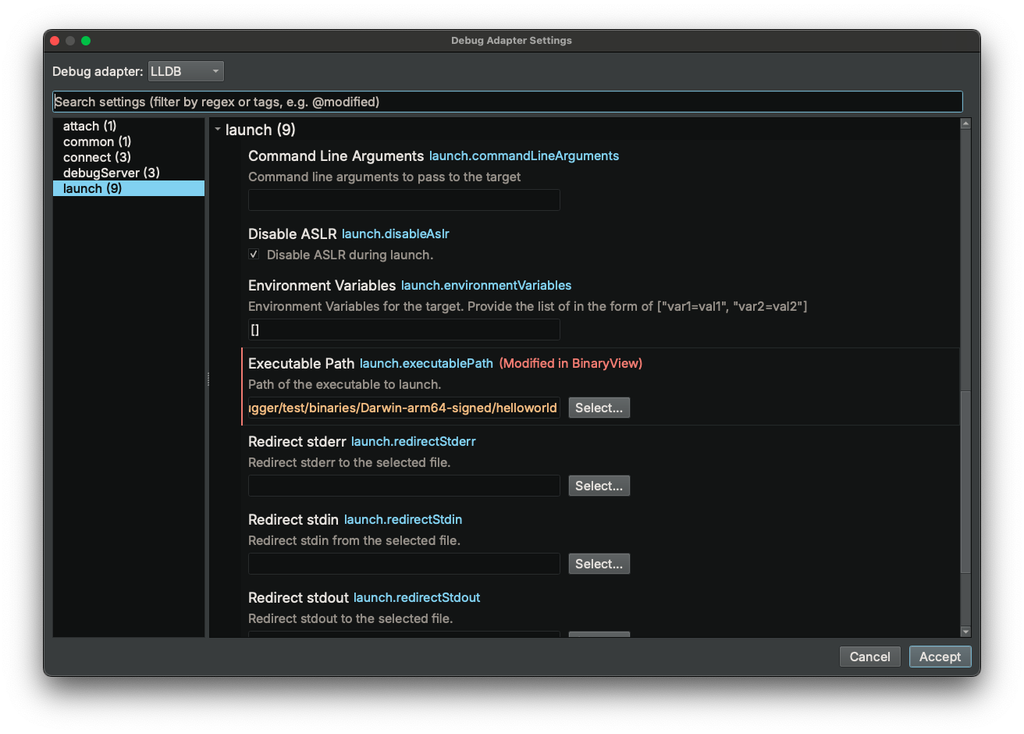
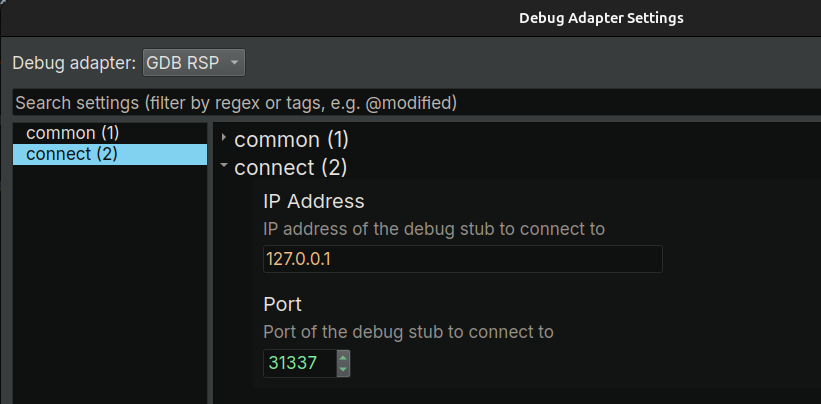
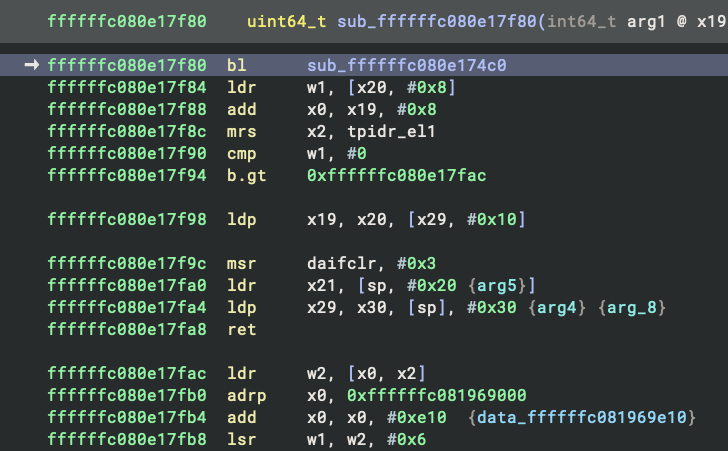
binaryninja@infosec.exchangeBinary Ninja 5.0 brings big updates to the debugger: a cleaner adapter settings UI, smarter analysis that won’t slow down your session, and new backends including rr and Corellium. Faster and more flexible debugging, whether local or remote! https://binary.ninja/2025/04/23/5.0-gallifrey.html#debugger
Jan Schaumann
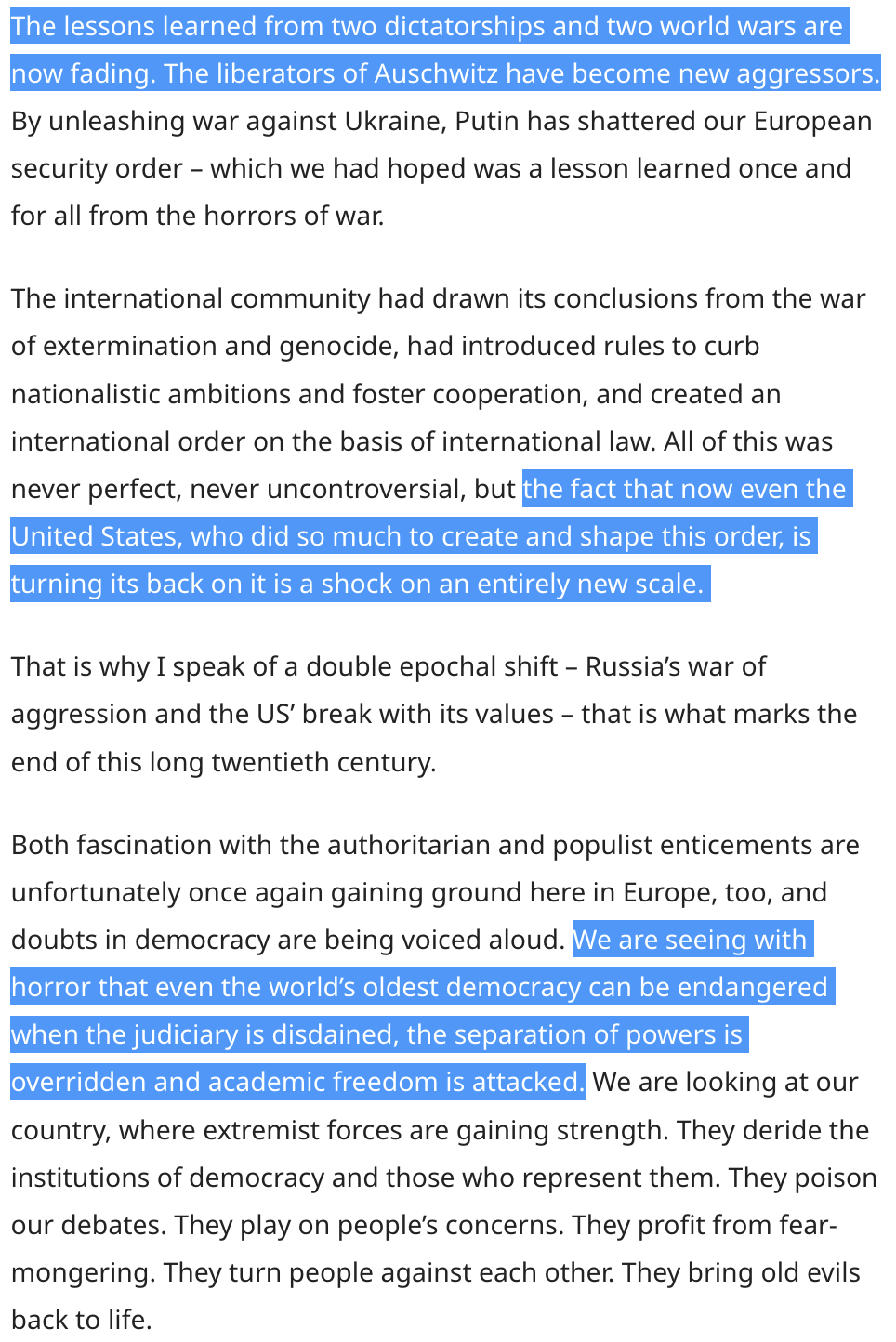
jschauma@mstdn.socialGerman President Steinmeier's speech commemorating the 80th anniversary of the end of World War II:
You want to read the whole thing, but the part below and the emphasis on the importance of learning from the past instead of describing it as a "cult of guilt" were powerful and eloquent. No words were minced, and we need more of that.
Tamas K Lengyel
tklengyel@discuss.systemsNow this looks like a pretty kick ass project: FUZZUER: Enabling Fuzzing of
UEFI Interfaces on EDK-2 https://www.ndss-symposium.org/wp-content/uploads/2025-400-paper.pdf and source at https://github.com/BreakingBoot/FuzzUEr
Tamas K Lengyel
tklengyel@discuss.systemsFinally a paper on malware fuzzing! PFUZZER: Practical, Sound, and Effective Multi-path Analysis of
Environment-sensitive Malware with Coverage-guided Fuzzing https://www.diag.uniroma1.it/~delia/papers/eurosp25-pfuzzer.pdf