Posts
3373Following
712Followers
1579Ken Shirriff
kenshirriff@oldbytes.spaceIntel's 386 processor (1985) moved the x86 architecture to 32 bits, but it needed to be backward compatible with earlier 16 and 8-bit processors. As a result, it needed complicated circuitry for its internal registers: six different circuits for 30 registers. Let's look at the silicon circuits. 1/N
buherator
buheratorhttps://binsec.github.io/nutshells/usenix-sec-25.html
/via @exploitsclub
buherator
buheratorhttps://github.com/SimaArasteh/binpool
/via @exploitsclub
buherator
buheratorhttps://xia0.sh/blog/visit-the-map/visit-the-map
/via @exploitsclub
Ars Technica
arstechnica@mastodon.socialGoogle is quietly testing ads in AI chatbots
Unsurprisingly, an advertising company is finding more places to run ads.
https://arstechnica.com/ai/2025/05/google-is-quietly-testing-ads-in-ai-chatbots/?utm_brand=arstechnica&utm_social-type=owned&utm_source=mastodon&utm_medium=social
buherator
buheratoradafruit
adafruit@mastodon.cloud🔐 The SLB 9670VQ2.0 FW7.85 SPI TPM module sounds like something your cat would type mid-zoom call — but it's actually a serious piece of security hardware.
This TPM (Trusted Platform Module) chip is used in motherboards and SBCs to store crypto keys, generate true random numbers, and keep your hardware’s trust chain tight, even if the rest of your system isn’t Fort Knox. TPM 2.0 is even a requirement for modern OSes like Windows 11.
CVE Program
CVE_Program@mastodon.socialA BIG WELCOME to these 7 CVE Numbering Authority (#CNA) partners that joined the #CVE Program in April!!!
* CTOne
* Insyde Software
* Jaspersoft
* Sandisk
* Spotfire
* The Qt Company
* TP-Link
Join: https://www.cve.org/PartnerInformation/Partner#HowToBecomeAPartner
Taggart
mttaggart@infosec.exchangeHow to win my instant support as a customer:
"We have decided not to focus on generative AI features, and instead reinvest heavily in quality assurance for our core products through hiring, training, and process development."
Taggart
mttaggart@infosec.exchangeSince @wdormann is quoted in this piece and I can't find Dan Wade's handle, I'm tagging him in.
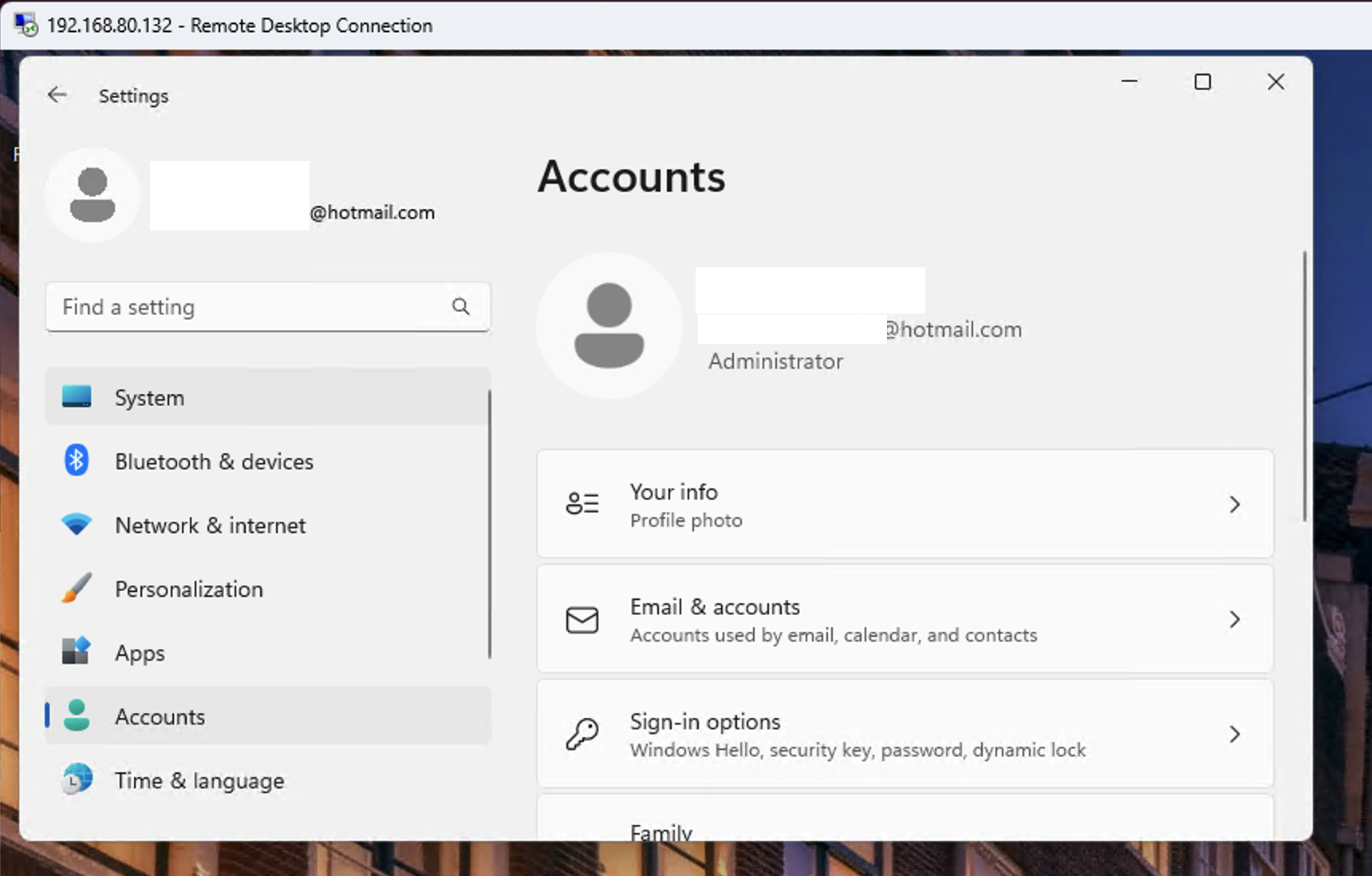
Is this suggesting that the RDP cred cache never gets updated? Ever ever?
Also what's up with this?
Old credentials continue working for RDP—even from brand-new machines.
That makes no sense at all.
Mr. Bitterness
wdormann@infosec.exchange@GossiTheDog @mttaggart
Thanks.
Yes, you can still RDP in with the old password after the account has been switched to passwordless. No Microsoft Authenticator required.
Limnetic Villains
limneticvillains@mastodon.onlineTomorrow is Bandcamp Friday. I've got fuck all money for the next 2 weeks, someone bought my discography the other day and I won't starve to death but if you dig obscure indie music of the dark electro rock type pokemon, perhaps consider buying my music tomorrow via Bandcamp! Shares help. Checking my music out and commenting on it helps! #bandcampfriday #music #art #fedimusic #fedimusicians #bandcamp
Https://Limneticvillains.bandcamp.com
Also I'm on Faircamp! https://negativevoid.art/limnetic
Thank you Fediverse.
buherator
buheratorhttps://www.bbc.com/news/articles/czd3mey1ej2o
- The main news is about Meta's consent or pay model makes users "choose between paying for a monthly subscription or letting Meta *combine data it has collected on Facebook and Instagram*", and how EU ruled this non-compliant with #DMA.
- It then links to another article about a model where where you can pay for *ad-free* Facebook. Ad-free is not the same as combining data from different platforms!
- There is no link to the EU source, but we get a full section about Meta's plans with AI, that has *nothing* to do with the original topic.
- In the middle of this mess we get a totally out of context paragraph explaining what Meta is?!
Was this all written by an LLM?
Does anyone happen to know what this regulation is actually about?
#EU #DMA #Meta #privacy #journalism
yossarian (1.3.6.1.4.1.55738)
yossarian@infosec.exchangemy colleague @DarkaMaul has put out a new post on the @trailofbits blog on how we worked with @pypi's maintainers to slash PyPI test run times from ~160s to ~30s despite overall test counts growing by 17% (3900 to 4700+):
https://blog.trailofbits.com/2025/05/01/making-pypis-test-suite-81-faster/
this is some of my favorite kind of work: faster test suites means that developers run tests locally more often, and are less hesitant to add new tests (especially parametric ones). another great example of security and performance/reliability engineering dovetailing.