Posts
2575Following
631Followers
1418William R. Messmer
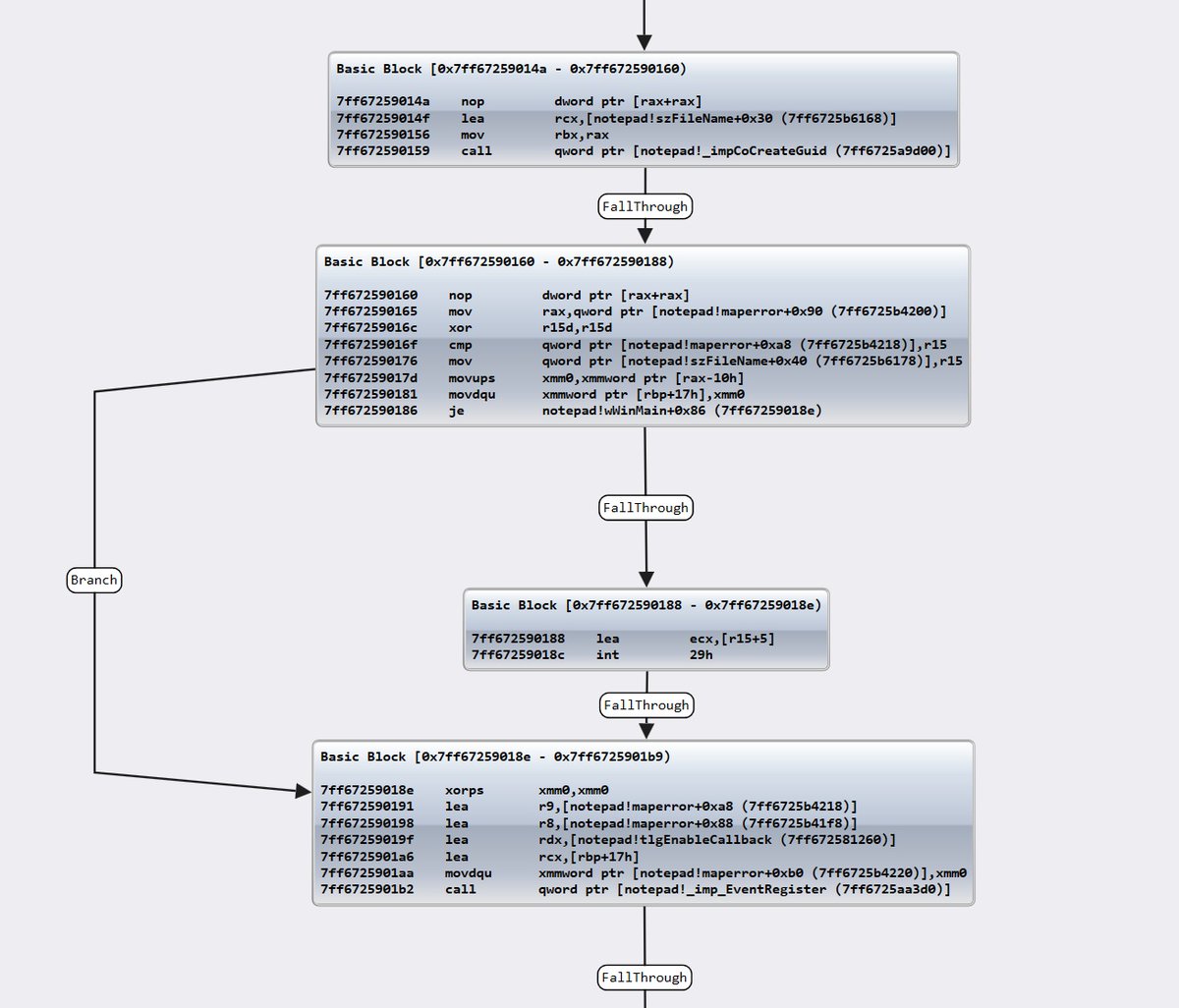
wmessmer@bird.makeupClicking this will bring up a graph view of the control flow of the function. Think of it as a visual representation of the 'uf' command:
William R. Messmer
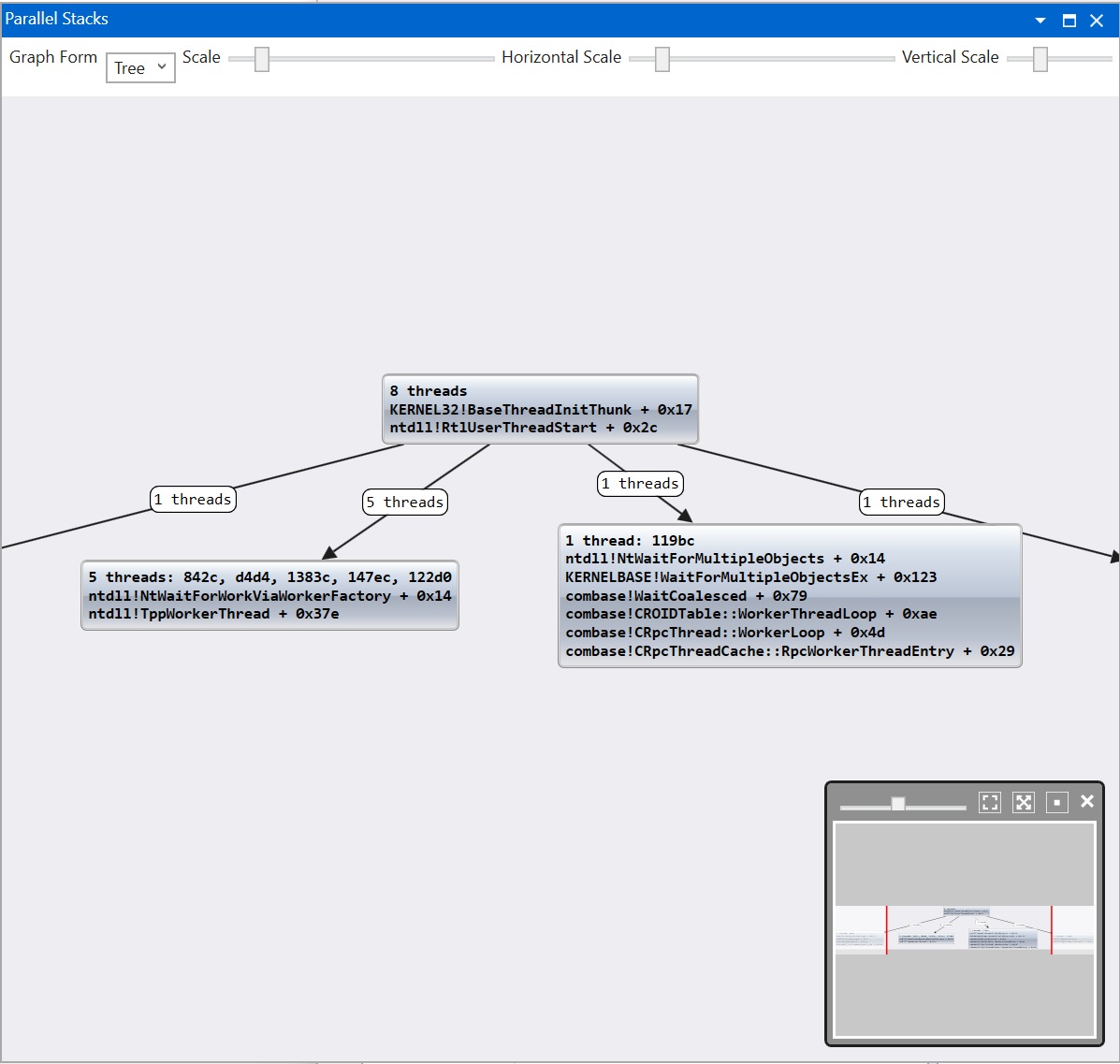
wmessmer@bird.makeupIf you click "Parallel Stacks", you'll see a visualized tree view of the call stacks in the process... something *similar* to what you might see in VS:
William R. Messmer
wmessmer@bird.makeupIf you update WinDbg today (1.2504.15001.0), you might notice another icon in the View tab of the ribbon, one called "Parallel Stacks". While incredibly useful in its own right, this isn't just a parallel stacks view. It's the introduction of graph visualization for extensions!
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Kinda want a DirBuster style list of headers at this point, so many times, we see new CVEs stemming from headers with magical properties.
✧✦Catherine✦✧
whitequark@mastodon.socialShow content
OH: see, if you slit your wrists, at least you accomplish something in the end. unlike doing a CTF
/r/netsec
_r_netsec@infosec.exchangeFire In The Hole, We’re Breaching The Vault - Commvault Remote Code Execution (CVE-2025-34028) - watchTowr Labs https://labs.watchtowr.com/fire-in-the-hole-were-breaching-the-vault-commvault-remote-code-execution-cve-2025-34028/
buherator
buheratorhttps://0xdeadc0de.xyz/blog/cve-2025-1731_cve-2025-1732
SSH tunnels FTW!
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchange🚨 New advisory was just published! 🚨
Two Use After Free (UAF) vulnerabilities were discovered within Chrome’s Browser process by one of our researchers at SSD Labs:
https://ssd-disclosure.com/ssd-advisory-miracleptr-sandbox/
daniel:// stenberg://
bagder@mastodon.socialHow the CNA thing is working out for #curl
https://daniel.haxx.se/blog/2025/04/24/how-the-cna-thing-is-working-out/
buherator
buheratorhttps://blog.ret2.io/2025/04/23/pwn2own-soho-2024-diskstation/
buherator
buheratorbuherator
buherator- Some rich text + images hosted online for the event
- Subscription form to get updates
- Stats about expected attendance
- ??? (this is my first time)
Edit: I don't charge anything for the event, so percentage commission can work.
buherator
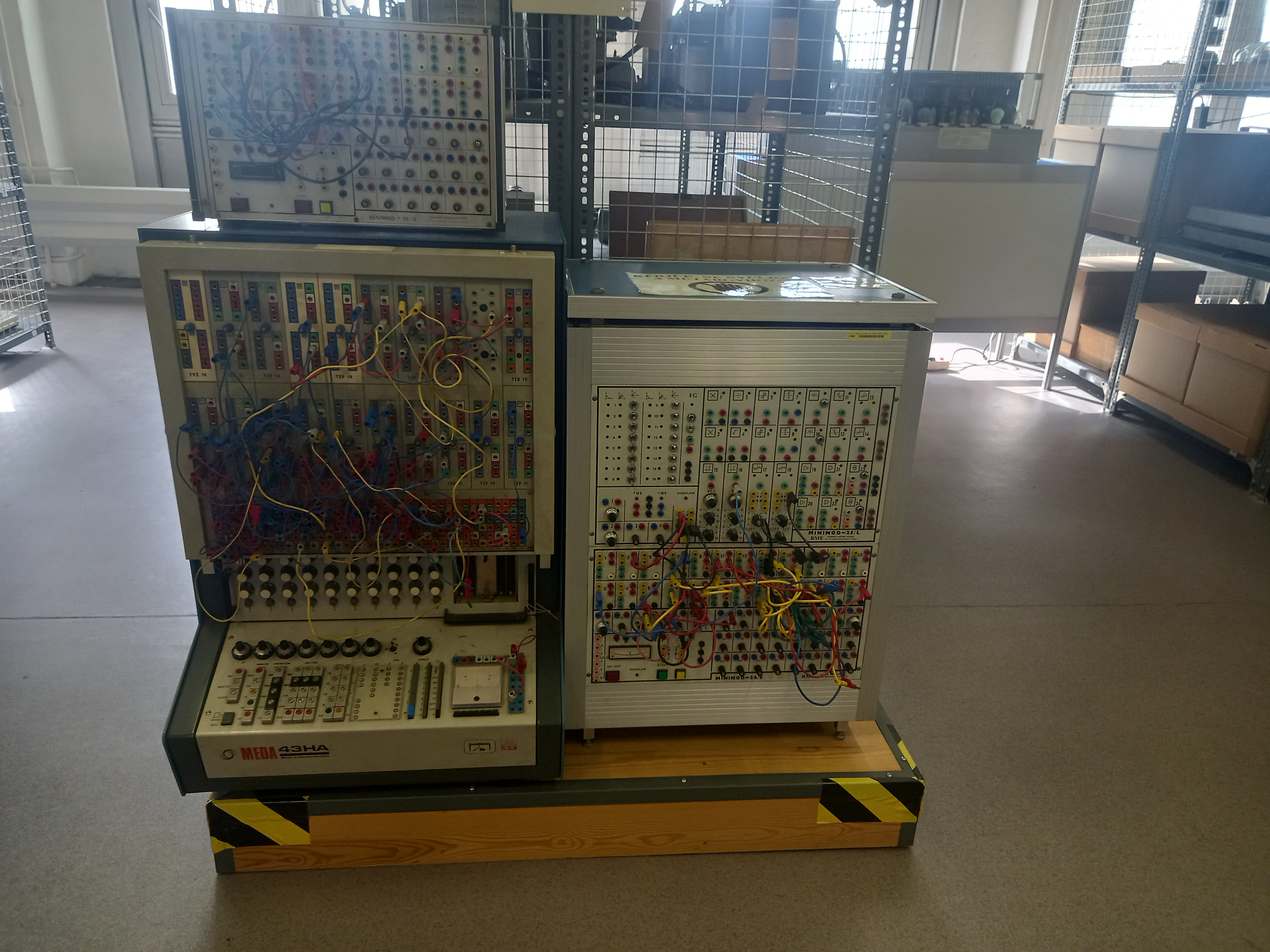
buheratorhttps://muzeuldecalculatoare.ro/2020/06/11/the-meda-43-analog-hybrid-computer/
Synacktiv
synacktiv@bird.makeupThe FastCGI library, mostly used in embedded equipment, was vulnerable for decades to an integer overflow over the IPC socket in 32-bits architecture. Check out how @shiropycatchown found it and exploited it for RCE!
https://www.synacktiv.com/en/publications/cve-2025-23016-exploiting-the-fastcgi-library
Mike Stone
mike@fosstodon.orgI know Chrome is the browser everybody loves to hate, but I think most would agree this would be very bad.