Posts
3373Following
712Followers
1579buherator
buheratorhttps://github.com/moreveal/hash-resolver
buherator
buheratorhttps://scribe.rip/@cy1337/tracing-data-flow-with-pcode-f879278d9fc1
#Ghidra #ReverseEngineering
buherator
buheratorhttps://msrc.microsoft.com/blog/2025/04/zero-day-quest-2025-1.6-million-awarded-for-vulnerability-research/
Lukasz Olejnik
LukaszOlejnik@mastodon.socialRussia is quietly rewriting reality — but not through tanks or troops, but by feeding disinformation and propaganda into the tools people may increasingly trust to understand the world: AI chatbots. It's gaming of the system, feeding propaganda in ways that people might never know what’s happening. Efforts to influence chatbot results are growing, as former SEO marketers now use "generative engine optimization" (GEO) to boost visibility in AI-generated responses https://www.washingtonpost.com/technology/2025/04/17/llm-poisoning-grooming-chatbots-russia/
yossarian (1.3.6.1.4.1.55738)
yossarian@infosec.exchangei'm very excited about this new work my team at @trailofbits is doing: we're building an ASN.1 API for PyCA Cryptography, giving users direct access to the same memory-safe, high-performance DER parser that Cryptography already uses for X.509:
https://blog.trailofbits.com/2025/04/18/sneak-peek-a-new-asn.1-api-for-python/
buherator
buheratorhttps://www.darknavy.org/blog/a_first_glimpse_of_the_starlink_user_ternimal/
buherator
buheratorhttps://spaceraccoon.dev/cybersecurity-antipatterns-busywork-generators/
CFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a287bec
yy_destructor
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a287bec.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a287bec.json&colors=light
Alex Plaskett
alexjplaskett@bird.makeupA blog explaining V8 Parser Workflow with a case study by w1redch4d
Alex Plaskett
alexjplaskett@bird.makeupExploiting the Nespresso smart cards for fun and profit coffee
Seth Larson
sethmlarson@fosstodon.orgVery good thread from @inthehands, LLMs cement the patterns of today and actual engineering and long-term problem solving require slow careful iteration and improvement.
Paul Cantrell
inthehands@hachyderm.ioA thought experiment: what would code look like today if we’d had the best AI of today, but only the programming languages of 1955? Would it even be •possible• to build an iPhone??
And what if the coming Vibe Coding Future is (as I believe) preposterously oversold? Then we have a generation of developers who’ve avoided doing the kind of wrestling with problems one has to do to find one’s way to engineering improvements.
9/
why2025camp
why2025camp@chaos.socialWHY2025 is calling for art. Neon. Space. Synthwave. Light. Interactive magic. Show us what you’ve got. 🌌
→ https://why2025.org/post/318
#WHY2025 #ArtCall #HackersMakeArt
Trail of Bits
trailofbits@infosec.exchangeAttackers can use MCP servers to hack your system before tools are invoked.
We call this attack vector "line jumping." This is a critical vulnerability in which tool descriptions become prompt injection vectors during the initial tools/list request. This technique bypasses invocation controls, breaking connection isolation and rendering security checkpoints ineffective.
Even "human approval" fails: AI-enabled IDEs permit automatic execution, and users rarely recognize disguised malicious commands.
Read the blog: https://blog.trailofbits.com/2025/04/21/jumping-the-line-how-mcp-servers-can-attack-you-before-you-ever-use-them/
poptart
yeslikethefood@infosec.exchangeFact checking my exploit against the Erlang SSH bug and the blog I'm reading uses git to checkout OTP... then proceeds to ask ChatGPT to write a tool to diff the files between the versions... in git. What's worse is that the CVE reference that they link to has always had the exact commit of the fix.
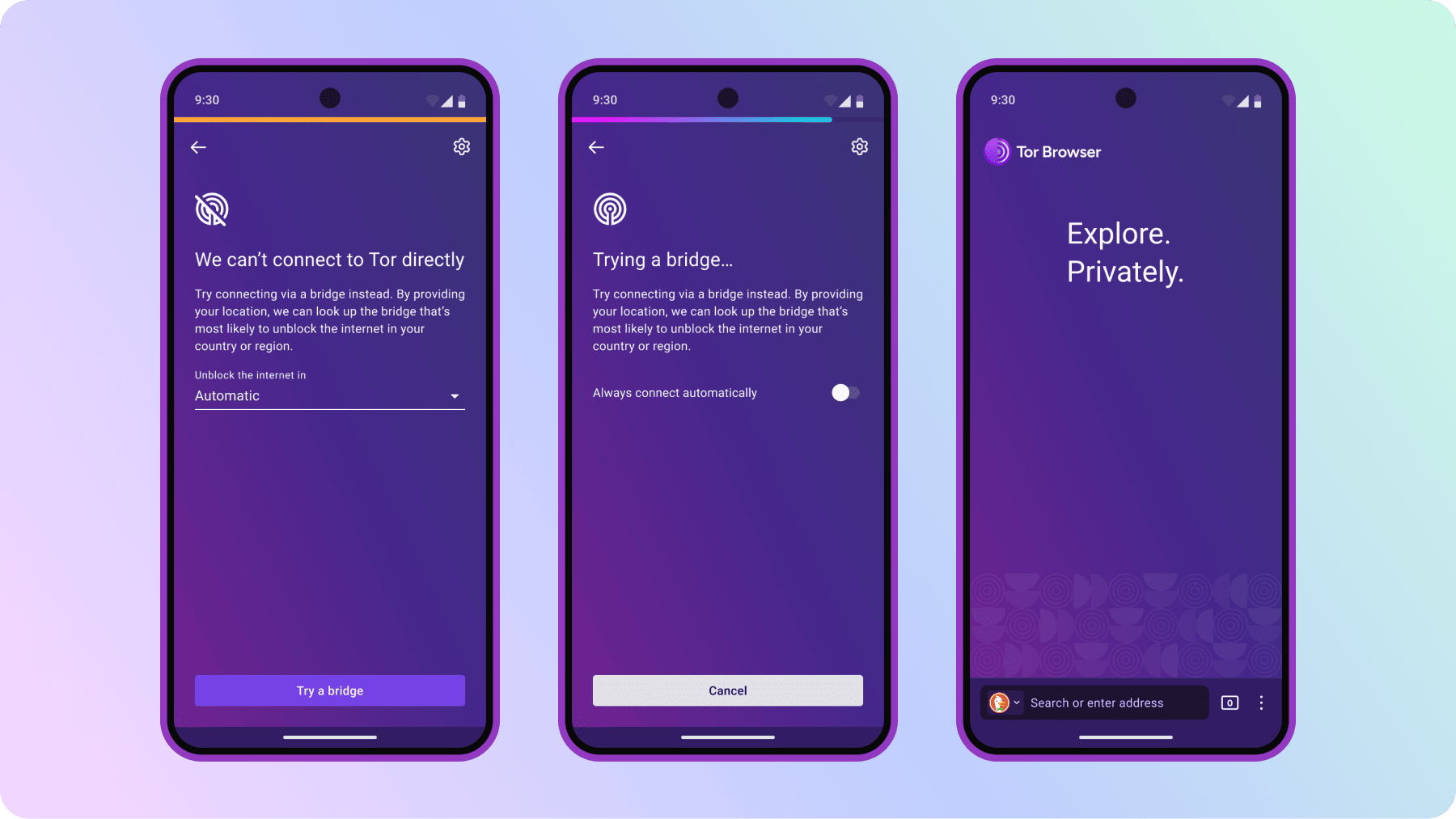
The Tor Project
torproject@mastodon.social🌐 Tor Browser 14.5 is here! Major improvements include:
• Connection Assist now on Android
• Added Belarusian, Bulgarian & Portuguese
• Improved log readability
• Better performance when quitting the app
Update today! #PrivacyMatters
https://blog.torproject.org/new-release-tor-browser-145/
Hacker News
h4ckernews@mastodon.socialReverse engineering the obfuscated TikTok VM
https://github.com/LukasOgunfeitimi/TikTok-ReverseEngineering
#HackerNews #ReverseEngineering #TikTok #VM #Obfuscation #CyberSecurity #TechInsights