Posts
2589Following
627Followers
1403Graham Sutherland / Polynomial
gsuberland@chaos.socialTIC80 jam just kicked off, with a DJ set from Commander Homer!
Washi
washi@infosec.exchangeAfter #flareon11 challenge 7, I got inspired to build tooling for #dotnet Native AOT reverse engineering.
As such, I built a #Ghidra Analyzer that can automatically recover most .NET types, methods and frozen objects (e.g., strings).
👉https://blog.washi.dev/posts/recovering-nativeaot-metadata/
/r/netsec
_r_netsec@infosec.exchangeCVE-2025-25364: Speedify VPN MacOS privilege Escalation https://blog.securelayer7.net/cve-2025-25364-speedify-vpn-macos-escalation/
Glyn Moody
glynmoody@mastodon.socialTake Action: Defend the @internetarchive - https://blog.archive.org/2025/04/17/take-action-defend-the-internet-archive/ "This lawsuit is an existential threat to the Internet Archive and everything we preserve—including the Wayback Machine, a cornerstone of memory and preservation on the internet." please sign the open letter if you can
This one's kind of fun.
https://github.com/fastify/fastify/security/advisories/GHSA-mg2h-6x62-wpwc
sev:HIGH 7.5 - CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N
Fastify is a fast and low overhead web framework, for Node.js. In versions 5.0.0 to 5.3.0, applications that specify different validation strategies for different content types have a possibility to bypass validation by providing a slightly altered content type such as with different casing or altered whitespacing before
;. This issue has been patched in version 5.3.1. A workaround involves not specifying individual content types in the schema.
I don't normally care about video games, especially with vulns, but this might be worth looking into. NamelessMC published 1 sev:CRIT, 4 sev:HIGH, and 1 sev:MED advisories since yesterday.
Why I care:
NamelessMC is a free, easy to use & powerful website software for Minecraft servers.
I have heard that Minecraft is used by predators to meet and influence or extort children, so if you know anyone running a Minecraft server that is used by kids, maybe make sure they know to keep it patched.
Tim Carstens Ⓥ✨ is hacking zk
intoverflow@bird.makeupFun fact:
💁 The oldest known buffer overflow vuln dates back to UNIX V6 login
💁♀️ It appeared in a 1981 post by Truscott & Ellis (better known for inventing Usenet)
💁♂️ The next overflow vuln was fingerd, 1988
Bonus fact:
🙅 The login vuln isn’t real:
https://www.tuhs.org/cgi-bin/utree.pl?file=V6/usr/source/s1/login.c
Open Source Security mailing list
oss_security@bird.makeupMultiple vulnerabilities in libxml2 https://www.openwall.com/lists/oss-security/2025/04/17/3
CVE-2025-32414: Buffer overflow when parsing text streams with Python API
Python Package Index contains outdated and unsanctioned vulnerable upload
CVE-2025-32415: Heap-based Buffer Overflow in xmlSchemaIDCFillNodeTables
Jason Scott
textfiles@mastodon.archive.orgIt was only a matter of time - a contracted, approved grant to the Internet Archive was cut with no warning.
RCE in Webex. Nice.
sev:HIGH 8.8 - CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
A vulnerability in the custom URL parser of Cisco Webex App could allow an unauthenticated, remote attacker to persuade a user to download arbitrary files, which could allow the attacker to execute arbitrary commands on the host of the targeted user. This vulnerability is due to insufficient input validation when Cisco Webex App processes a meeting invite link. An attacker could exploit this vulnerability by persuading a user to click a crafted meeting invite link and download arbitrary files. A successful exploit could allow the attacker to execute arbitrary commands with the privileges of the targeted user.
David Chisnall (*Now with 50% more sarcasm!*)
david_chisnall@infosec.exchangeThe first edition of the #CHERIoT book has been published!
The eBook editions are available for purchase now from a few retailers, print editions will take a bit longer to appear (up to two weeks). And, of course, the drafts of the second edition remain free (HTML, ePub, PDF) from the CHERIoT site
Thanks to Discribe Hub for funding a lot of the work on this edition!
buherator
buheratorhttps://www.openwall.com/lists/oss-security/2025/04/18/1
Exploit published ^
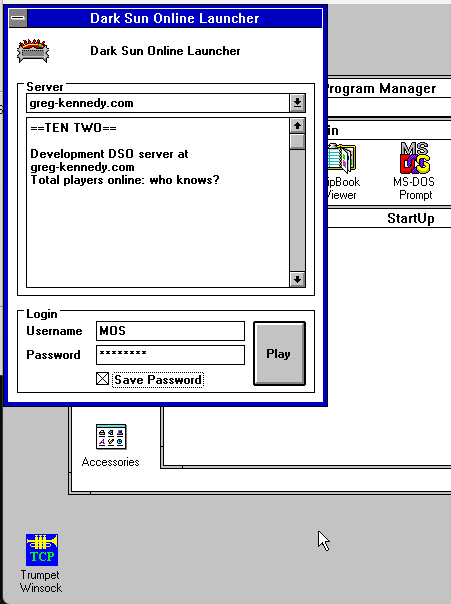
buherator
buheratorQuite proud of myself for successfully building a Windows 16-bit application that runs on Windows 3.1 - all dialog-based, and it makes network connections, too! Compiled with Visual C++ 1.52 on XP, it works on this old system. Consumes 14kb disk space and does everything in even less RAM :)
~swapgs
swapgs@infosec.exchange@buherator IIRC you get a GHSA ID every time you report something through https://github.com/php/php-src/security/, so this one must have been closed as N/A because it's now in https://github.com/php/php-src/issues/18209.
Anyway it's a nice writeup, and apparently a stable bug that will be useful to bypass disable_functions on a bunch of PHP releases!
Andrea Allievi
aall86@bird.makeuphttps://techcommunity.microsoft.com/blog/windows-itpro-blog/hotpatch-for-windows-client-now-available/4399808 Finally! I personally worked on Hotpatch, together with my team 3 years ago... and now is finally approaching client versions of Windows... Yuuuyuuu!