Posts
3368Following
712Followers
1580Jason Scott
textfiles@mastodon.archive.orgIt was only a matter of time - a contracted, approved grant to the Internet Archive was cut with no warning.
David Chisnall (*Now with 50% more sarcasm!*)
david_chisnall@infosec.exchangeThe first edition of the #CHERIoT book has been published!
The eBook editions are available for purchase now from a few retailers, print editions will take a bit longer to appear (up to two weeks). And, of course, the drafts of the second edition remain free (HTML, ePub, PDF) from the CHERIoT site
Thanks to Discribe Hub for funding a lot of the work on this edition!
buherator
buheratorhttps://www.openwall.com/lists/oss-security/2025/04/18/1
Exploit published ^
buherator
buheratorQuite proud of myself for successfully building a Windows 16-bit application that runs on Windows 3.1 - all dialog-based, and it makes network connections, too! Compiled with Visual C++ 1.52 on XP, it works on this old system. Consumes 14kb disk space and does everything in even less RAM :)
~swapgs
swapgs@infosec.exchange@buherator IIRC you get a GHSA ID every time you report something through https://github.com/php/php-src/security/, so this one must have been closed as N/A because it's now in https://github.com/php/php-src/issues/18209.
Anyway it's a nice writeup, and apparently a stable bug that will be useful to bypass disable_functions on a bunch of PHP releases!
Andrea Allievi
aall86@bird.makeuphttps://techcommunity.microsoft.com/blog/windows-itpro-blog/hotpatch-for-windows-client-now-available/4399808 Finally! I personally worked on Hotpatch, together with my team 3 years ago... and now is finally approaching client versions of Windows... Yuuuyuuu!
hasherezade
hasherezade@bird.makeupMy new blog for Check Point Research - check it out! 💙 // #ProcessInjection : #WaitingThreadHijacking
Satoshi Tanda
standa_t@bird.makeupI am thrilled to be back and offer the in-person training once again at Hexacon, the fabulous conf. in Paris
https://hexacon.fr/trainer/tanda/
Get hands-on experience with virtualization and learn real-world applications and bugs of them!
The tickets will be available for purchase soon.
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Interesting links of the week:
Strategy:
* https://en.wikipedia.org/wiki/SIPOC - modelling systems with SIPOC
* https://www.thecvefoundation.org/ - the CVE foundation
* https://euvd.enisa.europa.eu/ - EU bug jail
* https://xntrik.wtf/aisa2024/ - @xntrik maps threats with https://threatcl.github.io/
* https://threatspec.org/ - the ThreatSpec
Threats:
* https://cloud.google.com/blog/topics/threat-intelligence/windows-rogue-remote-desktop-protocol - a novel phishing attack involving RDP
Detection:
* https://rulehound.com/rules - a single place to find interesting detection engineering ideas
Bugs:
* https://bugs.chromium.org/p/chromium/issues/detail?id=584535 - an 11 year old bug in every browser, still not dead!
Exploitation:
* https://silentsignal.github.io/BelowMI/ - memory management on System i courtesy of @buherator
* https://github.com/N1ckDunn/SOSLInjection/blob/main/SOSLInjection.pdf - Sal''esforce \o/
* https://github.com/N1ckDunn/DoubleFetch/blob/main/Double-FetchVulnerabilitiesInC.pdf - exploiting double fetch
Hard hacks:
* https://xairy.io/articles/thinkpad-xdci - emulating USB on a ThinkPad
* https://www.rtl-sdr.com/dragonos-lte-imsi-sniffing-using-the-lte-sniffer-tool-and-an-ettus-x310-sdr/ - build your own LTE sniffer
* https://blog.sesse.net/blog/tech/2025-04-05-10-57_cisco_2504_password_extraction.html - extracting passwords from Cisco WLC
* https://www.prizmlabs.io/post/remote-rootkits-uncovering-a-0-click-rce-in-the-supernote-nomad-e-ink-tablet - exploiting the Nomad e-ink tablet
Nerd:
* https://ukparliament.github.io/ontologies/meta/bots/ - UK parliamentary bots
* https://mwl.io/fiction/crime - Git drives people to murder
* https://changelog.complete.org/archives/10768-announcing-the-nncpnet-email-network - building a new mail protocol
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
My cross-platform and cross-browser NTLM bug is public:
https://issues.chromium.org/issues/40080133
Kudos to @Bitquark who reported it separately.
Kudos also to @torproject and @mozilla who did make efforts.
Linux Kernel Security
linkersec@infosec.exchangeKernel-Hack-Drill: Environment For Developing Linux Kernel Exploits
Alexander Popov @a13xp0p0v published the slides from his talk at Zer0Con 2025. In this talk, he presented the kernel-hack-drill open-source project and showed how it helped him to exploit CVE-2024-50264 in the Linux kernel.
Slides: https://a13xp0p0v.github.io/img/Alexander_Popov-Kernel_Hack_Drill-Zer0Con.pdf
Project: https://github.com/a13xp0p0v/kernel-hack-drill
Mr. Bitterness
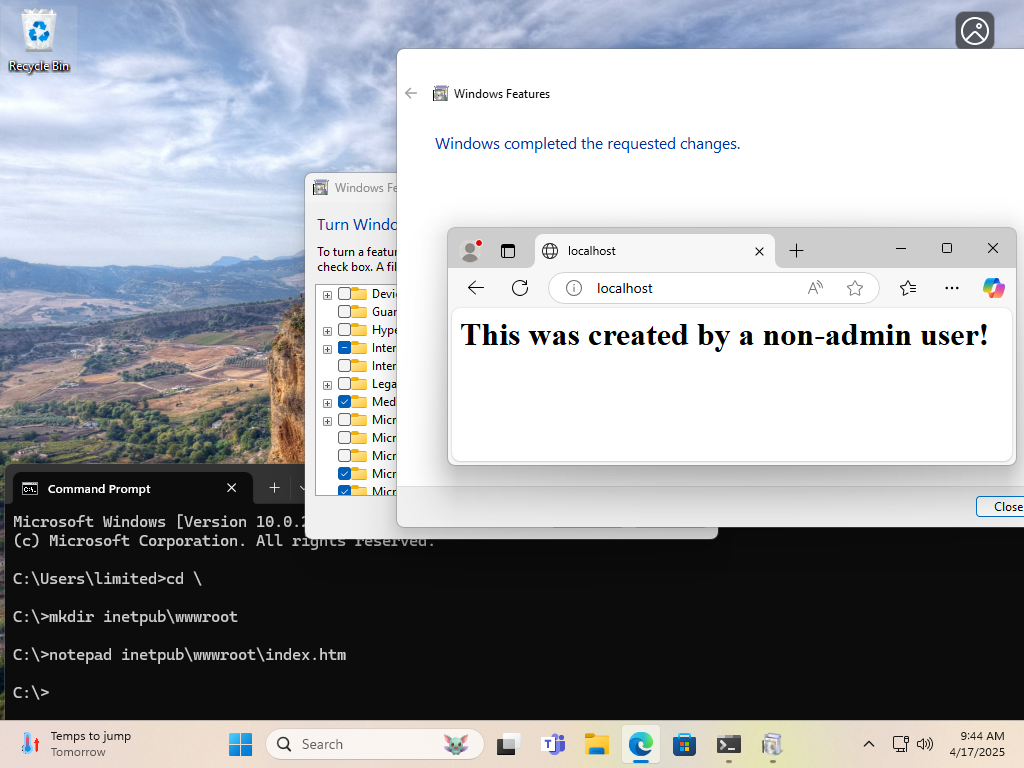
wdormann@infosec.exchangeFrom over at the Bad Site ™
Both the vulnerability and the "fix" for CVE-2025-21204 are quite silly.
The scenario is:
- Non-admin user creates
C:\inetpub\wwwrootdirectory and puts web content there - Admin user at some point in the future enables IIS on the system.
The outcome is:
The web content provided by the non-admin user (be it a web shell or whatnot) is served up by IIS.
Maybe non-admin users shouldn't be able to make directories or junctions (to directories or files) in C:\?
NAH.
Maybe installing IIS should provide a clean webroot when it's installed?
NAH.
Just preemptively make a C:\inetpub directory that non-admin users can't write to. That fixes the problem. 🤦♂️
hrbrmstr 🇺🇦 🇬🇱 🇨🇦
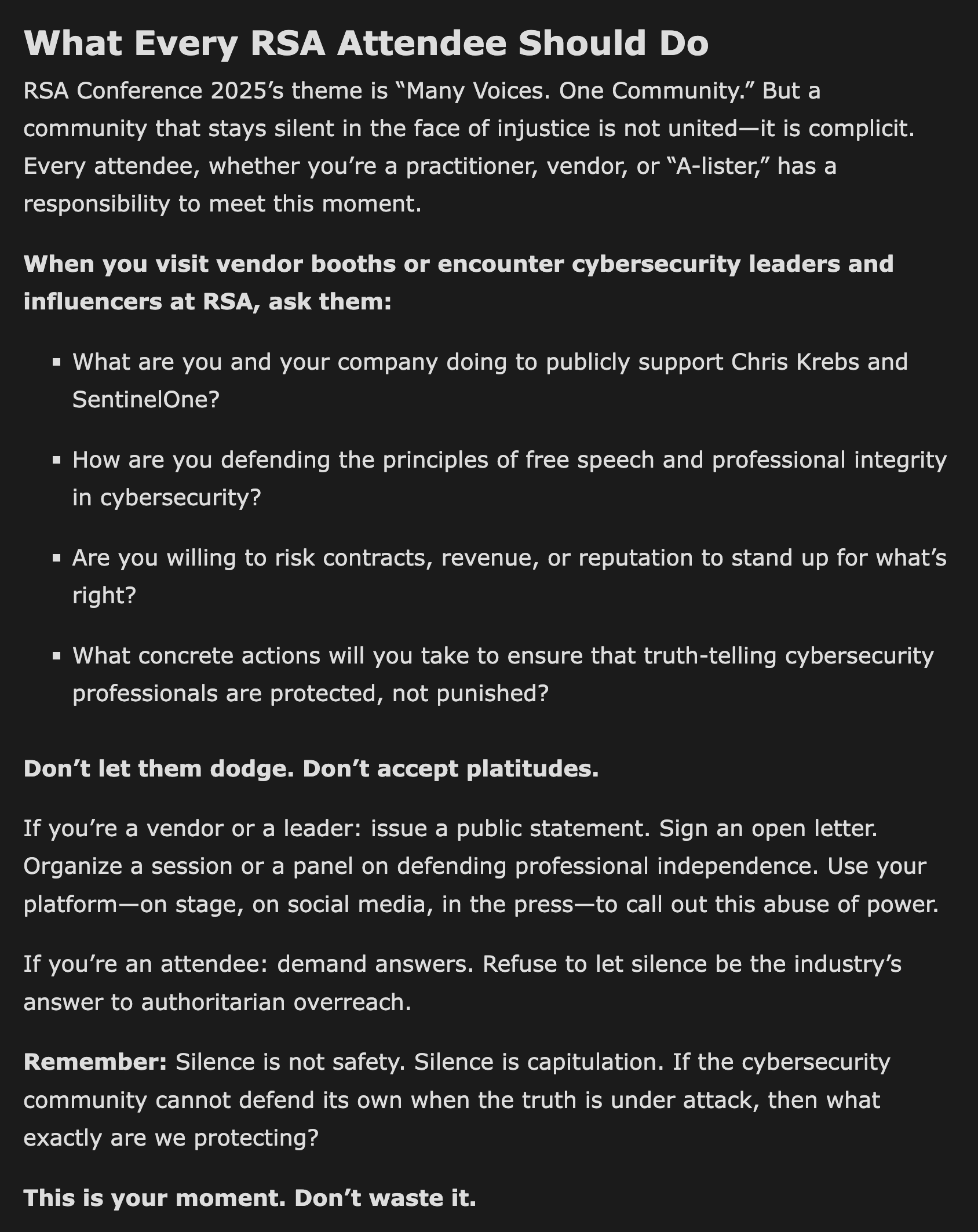
hrbrmstr@mastodon.socialDid a post on the personal blog (i.e., “the views expressed by me do not…blah blah”) — “Trump’s Retaliation Against Chris Krebs — and the Cybersecurity Industry’s Deafening Silence”.
Unlike most years, everyone attending RSA next week has a tangible, meaningful opportunity to make a difference.
Be better than the complicit cowards (humans & vendors) in our industry, speak up, & hold folks accountable.
Otherwise, “Many Voices. One Community” is just BS RSA marketing.
Prof. Emily M. Bender(she/her)
emilymbender@dair-community.social"Providers are pushed to spend less time caring for each patient as health systems move to reduce costs and increase revenue under the technological principle of maximal efficiency and output. But medicine was never intended to be another industrial complex."
This essay is beautiful and powerful.