Posts
2983Following
697Followers
1545Seriously, this HAS to be insider trading.
Come on! First you announce tariffs, every stock tanks, you play the hard to get dude and proclaim with a swollen chest that there will be no delays, everything tanks even more.
And now you delay everything by 90 days? In the mean time your buddies bought everything at a low and now the stock recovers.
Come the fuck on!
Lorenzo Franceschi-Bicchierai
lorenzofb@infosec.exchangeNEW: A recently published court document shows the locations of WhatsApp victims targeted with NSO Group's spyware.
The document lists 1,223 victims in 51 countries, including Mexico, India, Morocco, United Kingdom, United States, Spain, Hungary, Netherlands, etc.
This targeting was over a span of around two months in 2019, according to WhatsApp's lawsuit against NSO Group.
Brad Spengler
spendergrsec@bird.makeupJust saw it mentioned on LWN, handy site for checking which distros enable a certain config option: https://oracle.github.io/kconfigs/?config=UTS_RELEASE&... Just replace UTS_RELEASE with whatever config option name minus CONFIG_, for example: https://oracle.github.io/kconfigs/?config=CFI_CLANG&...
Margaret Harris
DrMLHarris@mastodon.socialSplitting water into hydrogen and oxygen takes more energy than it theoretically should, which is partly why it's not used on a large scale to generate hydrogen fuel.
Now scientists know why – and it's all down to a feat of nanoscale gymnastics.
rev.ng
revng@infosec.exchange🔴 Our @reconmtl talk of last year has been published!
"Path of rev.ng-ance: from raw bytes to CodeQL on decompiled code"
Check it out: https://www.youtube.com/watch?v=0lrhCV14nVE
buherator
buheratorDisconnect3d
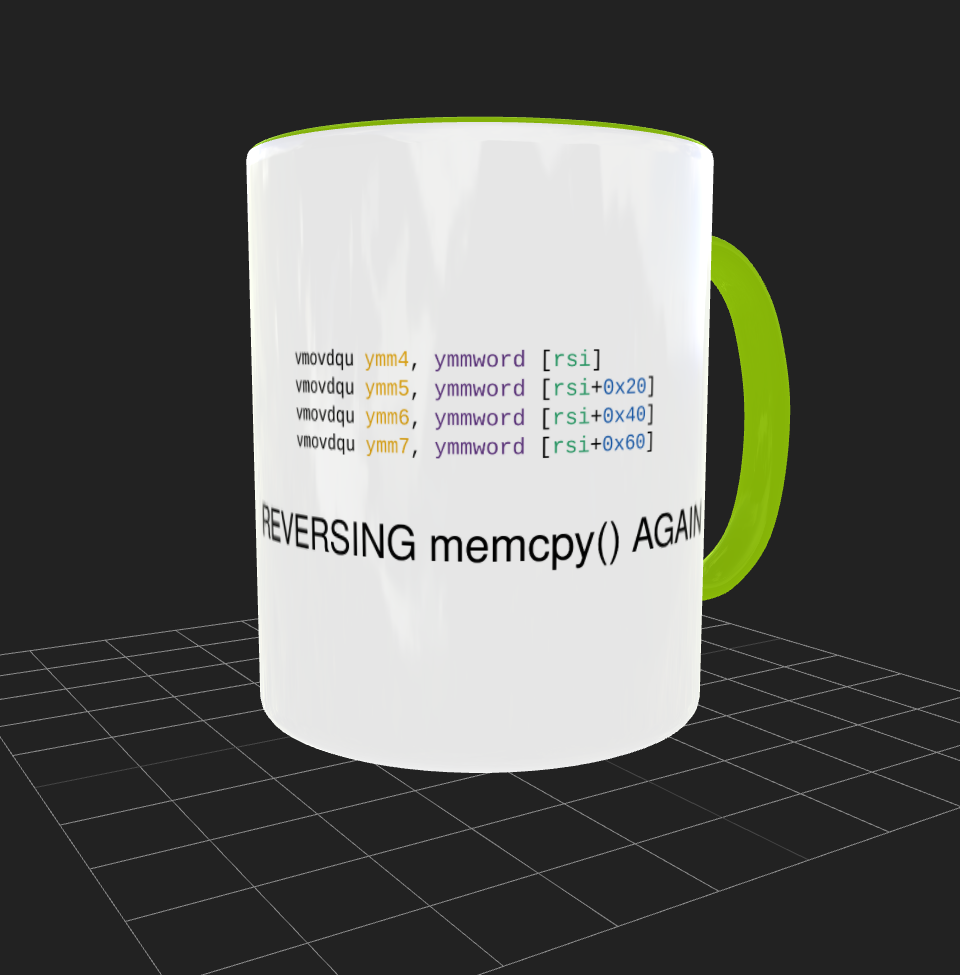
disconnect3d@infosec.exchangeA call to memcpy() in a single binary that uses glibc may behave in 12 different ways depending on the features of the specific x86-64 CPU you run it on.
Here is a list of those impls in glibc:
Fwiw this may matter a lot during binary exploitation. This was important in a challenge from PlaidCTF 2025. E.g. passing a negative (or: very huge) length allowed you to write past a buffer without a crash (the given implementation was not doing a wild copy).
Firefox Nightly
firefoxnightly@mastodon.socialHardening the Firefox Frontend with Content Security Policies
https://attackanddefense.dev/2025/04/09/hardening-the-firefox-frontend-with-content-security-policies.html
buherator
buheratorHere’s the #Ghidriff output for CLFS.sys 10.0.20348.3328 vs. 10.0.20348.3453, likely corresponding to the CVE-2025-29824 use-after-free LPE:
https://gist.github.com/v-p-b/8c43fb8e0d72814dcd03764d478622ce
buherator
buheratorhttps://posts.specterops.io/the-sql-server-crypto-detour-5ff9ac7033de?source=rss----f05f8696e3cc---4
buherator
buheratorhttps://www.thezdi.com/blog/2025/4/8/the-april-2025-security-update-review
buherator
buheratorhttp://blog.quarkslab.com/aosp_ota_signature_bug.html
buherator
buheratorhttps://www.talospace.com/2025/04/enter-ibm-z17-mainframe-with-telum-ii.html
Taggart
mttaggart@infosec.exchangeOh is it time for another Fortinet crit again? Unauthenticated admin password change in FortiSwitch.
CVE-2024-48887, CVSSv3 9.3
buherator
buheratorAmazingly, DOGE seems to be a meme: their power is that people assume they have power (note that the top article doesn't even mention DOGE).