Posts
3368Following
712Followers
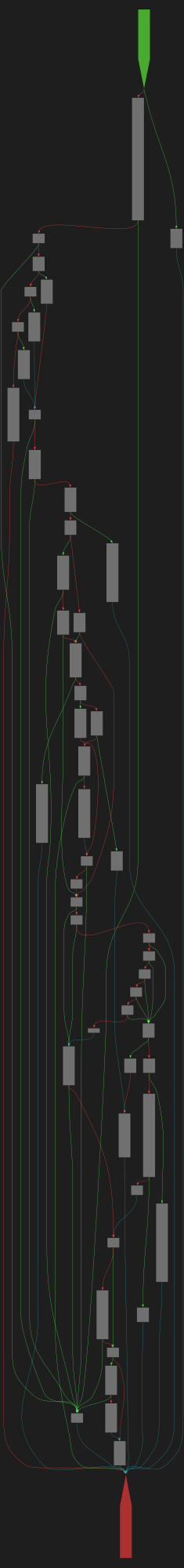
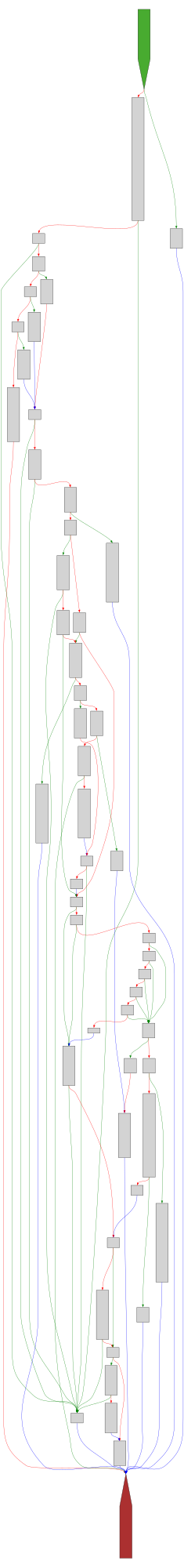
1580CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 0063a0a0
rsa_ossl_private_encrypt
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0063a0a0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0063a0a0.json&colors=light
Mr. Bitterness
wdormann@infosec.exchangeGiven that the web server on an ICS runs as the limited nr user, both the Ivanti and the Mandiant advisory are missing any indication whatsoever how the threat actors are gaining root privileges. And the CVSS score for CVE-2025-22457 is definitely wrong, as it has S:C (scope changed). The LPE is what will change the scope, but the April Ivanti advisory lacks any mention at all about any LPE. But I suppose it's common practice to assign CVSS scores to a single CVE that's used in a multiple-vulnerability attack chain. 😕
I've reported 4 different ICS LPEs to Ivanti recently, but none of them have been fixed yet.
Back in the CVE-2025-0282 days, Ivanti made up a CVE-2025-0283 CVE to capture the LPE aspect of attacks happening in the wild. I say "made up" because I've seen no evidence whatsoever that any LPE was fixed between 22.7R2.5 and 22.7R2.6.
Knowing what's going on in an ICS device is a huge blind spot, but apparently seeing how attackers are LPE'ing is even blind-er.
Mr. Bitterness
wdormann@infosec.exchangeIvanti CVE-2025-22457 is being exploited ITW.
https://forums.ivanti.com/s/article/April-Security-Advisory-Ivanti-Connect-Secure-Policy-Secure-ZTA-Gateways-CVE-2025-22457
Per Mandiant:
We assess it is likely the threat actor studied the patch for the vulnerability in ICS 22.7R2.6 and uncovered through a complicated process, it was possible to exploit 22.7R2.5 and earlier to achieve remote code execution.
Gee, who could have imagined that attackers are looking at patches? 🤔
1) This apparently was silently fixed for ICS in 22.7R2.6, as the fix for this was released in February. Per Ivanti, the buffer overflow was considered a "product bug" at that time, as opposed to a vulnerability. Ivanti Policy Secure and ZTA gateways are expected to receive a patch in late April.
2) The advisory still conveys the magical thinking if if your device shows signs of compromise, then you should perform a "factory reset." This is magical in that the ICT won't catch a compromise nor will the "factory reset" reset to factory condition if the attacker is bothering to try.
While Mandiant also parrots the magical thinking of running the ICT tool, which I guess is the best advice if you're not going to throw the device in the trash since there isn't an official integrity checking tool that is sound, they do throw out a tidbit of:
... and conduct anomaly detection of client TLS certificates presented to the appliance.
Bets on whether CVE-2025-22457 is an overflow in the handling of a field in a client-provided certificate? 😂
/r/netsec
_r_netsec@infosec.exchangeSuspected China-Nexus Threat Actor Actively Exploiting Critical Ivanti Connect Secure Vulnerability (CVE-2025-22457) https://cloud.google.com/blog/topics/threat-intelligence/china-nexus-exploiting-critical-ivanti-vulnerability/
exploits.club
exploitsclub@bird.makeup66 weeks in a row...whatchu know about it 📰 THE vuln research newsletter out NOW
MCPGhidra from @lauriewired
@u1f383 talks DirtyCOW
Mitigations galore with @standa_t and @slowerzs
XSS -> RCE with @chudypb and @watchtowrcyber
+ Jobs and MORE 👇
buherator
buheratorhttps://www.openwall.com/lists/oss-security/2025/04/03/1
"Our belief is that it's highly impractical to exploit on 64-bit systems
where xz was built with PIE (=> ASLR), but that on 32-bit systems,
especially without PIE, it may be doable."
buherator
buheratorhttps://googleprojectzero.blogspot.com/2016/06/how-to-compromise-enterprise-endpoint.html
Edit: it seems they needed a (rather trivial) privesc in case of FE, so give credit where it's due ;)
https://project-zero.issues.chromium.org/issues/42452189
buherator
buheratorhttps://ernw.de/download/ERNW_44CON_PlayingWithFire_signed.pdf
buherator
buheratorbuherator
buheratorhttps://www.youtube.com/watch?v=ce0bXORSMX4
/r/netsec
_r_netsec@infosec.exchangeFrida 16.7.0 is out w/ brand new APIs for observing the lifecycles of threads and modules, a profiler, multiple samplers for measuring cycles/time/etc., MemoryAccessMonitor providing access to thread ID and registers, and more 🎉 https://frida.re/news/2025/03/13/frida-16-7-0-released/
The Peter Pan of Nerdery™ 🇦🇺
dhry@mastodon.social#NotepadPlusPlus v8.7.9 released.
The author is totally my spirit animal.
#arm64 #windows #freeware
https://notepad-plus-plus.org/news/v879-we-are-with-ukraine/ https://notepad-plus-plus.org/news/v879-we-are-with-ukraine/
Edit: we is fedi-trending, guyzz! 🤗
buherator
buheratorhttps://projectblack.io/blog/zendto-nday-vulnerabilities/
#NoCVE
David Chisnall (*Now with 50% more sarcasm!*)
david_chisnall@infosec.exchange@grumpygamer There’s an idea in advertising that this doesn’t matter because it raises brand awareness. This is backed by some studies that suggest that people will remember brands long after they forget why they remember the brand and, when presented with a choice, will favour things they recognise.
I did an experiment on myself to try to explain why I’d picked particular brands (particularly for new product classes) and found that it looked like this effect had worked on me. I started actively avoiding brands where I felt they had a good reputation but couldn’t explain why.
That was a bit exhausting so I came up with a new strategy: whenever I see an ad like this, I repeat ‘fuck {brand name}’ in my head until it goes away. Then, when I encounter that brand later, the collocation is automatically in my head and I just avoid any brands where that’s my subconscious response.
K. Ryabitsev-Prime 🍁
monsieuricon@social.kernel.orgWe'll be rolling it out on lore.kernel.org and git.kernel.org in the next week or so.