Posts
2584Following
627Followers
1397Jonty Wareing
jonty@chaos.socialPlease remember that what you see on social media is what people choose to present, not an accurate representation of their life. Few people post about the horror.
Don't put off seeing friends because "they're having fun" or "they're busy" and "you'll see them later". You do not know that any of these things are true.
CFG Bot 🤖
cfgbot@mastodon.socialProject: microsoft/TypeScript https://github.com/microsoft/TypeScript
File: src/compiler/scanner.ts:1890 https://github.com/microsoft/TypeScript/blob/cbac1ddfc73ca3b9d8741c1b51b74663a0f24695/src/compiler/scanner.ts#L1890
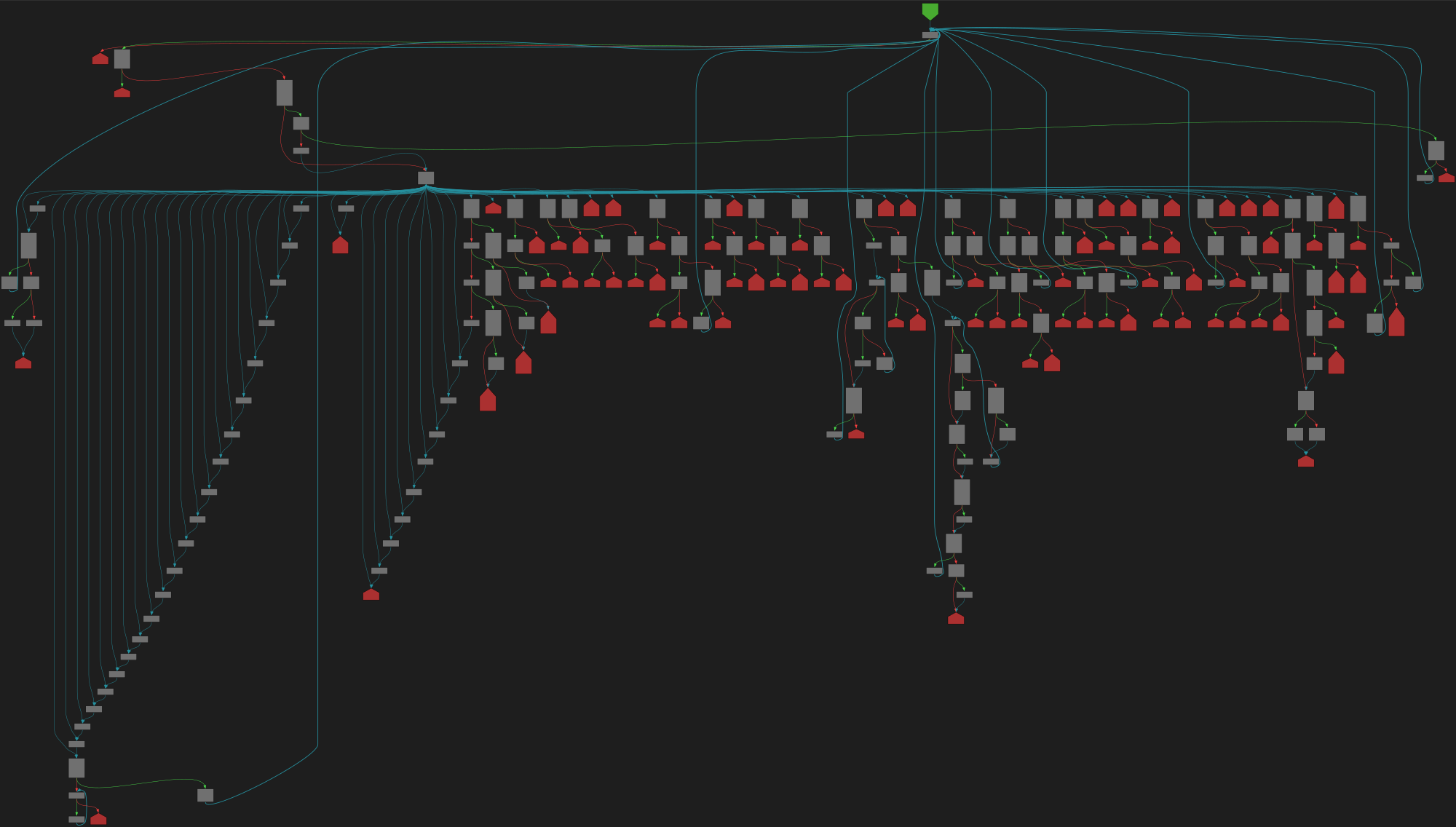
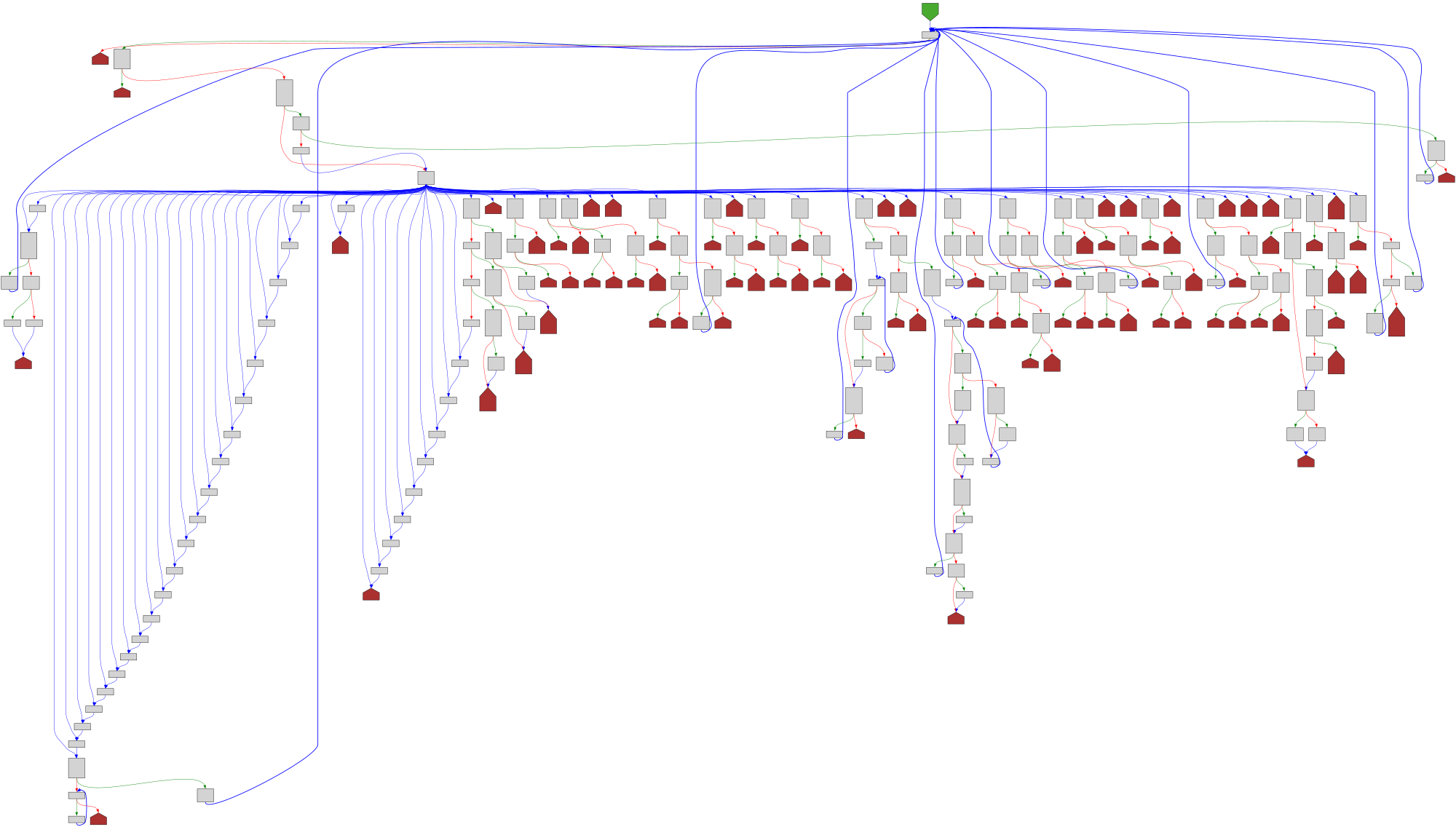
function scan(): SyntaxKind
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FTypeScript%2Fblob%2Fcbac1ddfc73ca3b9d8741c1b51b74663a0f24695%2Fsrc%2Fcompiler%2Fscanner.ts%23L1890&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FTypeScript%2Fblob%2Fcbac1ddfc73ca3b9d8741c1b51b74663a0f24695%2Fsrc%2Fcompiler%2Fscanner.ts%23L1890&colors=light
Sonar Research
SonarResearch@infosec.exchange🦘🛜 Our second part of the “Diving Into JumpServer” series is live:
Read more on how an attacker who bypassed authentication can execute code and fully compromise the JumpServer instance and internal hosts:
Caitlin Condon
catc0n@infosec.exchangeI probably sound like a broken record at this point, but we're not sold yet on the world-ending nature of Next.js CVE-2025-29927.
The fact that the bug isn't known to have been successfully exploited in the wild despite the huge amount of media and industry attention it’s received sure feels like a reasonable early indicator that it's unlikely to be broadly exploitable (classic framework vuln), and may not have any easily identifiable remote attack vectors at all.
https://www.rapid7.com/blog/post/2025/03/25/etr-notable-vulnerabilities-in-next-js-cve-2025-29927/
Joxean Koret (@matalaz)
joxean@mastodon.socialNapalm Death, Throes Of Joy In The Jaws Of Defeatism (2020).
https://www.youtube.com/playlist?list=OLAK5uy_kWcUQiY1m-s4mdg2Tbu1ZFykF20UkVbG4
gergelykalman
gergelykalman@infosec.exchangeI published a correction to my slides/blogposts regarding rename(). I have incorrectly stated that rename("./a", "./b") was racy. It is not.
For most situations this is not a huge deal, but I still feel bad that I misled you all, so beers are on me.
0patch
0patch@infosec.exchangeMicropatches Released for SCF File NTLM Hash Disclosure Vulnerability (No CVE) https://blog.0patch.com/2025/03/micropatches-released-for-scf-file-ntlm.html
Matthew Green
matthew_d_green@ioc.exchangeI have too many reasons to worry about this but that’s not really the point. The thing I’m worried about is that, as the only encrypted messenger people seem to *really* trust, Signal is going to end up being a target for too many people.
Signal was designed to be a consumer-grade messaging app. It’s really, really good for that purpose. And obviously “excellent consumer grade” has a lot of intersection with military-grade cryptography just because that’s how the world works. But it is being asked to do a lot!
Right now a single technical organization is being asked to defend (at least) one side in a major regional war, the political communications of the entire US administration, the comms of anyone opposed to them globally, big piles of NGOs, and millions of “ordinary” folks to boot.
(There is no such thing as “ordinary user” cryptography BTW. Those ordinary users include CEOs, military folks, people doing many-million-dollar crypto trades through the app, etc. It’s a lot to put on one app and one non-profit.)
On top of this, it’s only a matter of time until governments (maybe in the US or Europe) start putting pressure on the infrastructure that Signal uses — which is mostly operated by US companies. I’m not sure how this will go down but it’s inevitable.
Jeff Hicks 🐶🎼🍷🖥️
JeffHicks@techhub.socialIf you are at the Microsoft MVP Summit this week, and in the Windows Server space, please add your voice for the release of eval ISOs of Windows Server on ARM. We need these for *local* testing, training, and development.
Alex Plaskett
alexjplaskett@bird.makeupTrigon: developing a deterministic kernel exploit for iOS by @alfiecg_dev
The Hacker‘s Choice
thc@infosec.exchangePRE-RELEASE: I wrote a Linux Binary Runtime Crypter - in BASH 😅. Would love you fine people to TEST it _BEFORE_ release: https://github.com/hackerschoice/bincrypter
REcon
reconmtl@bird.makeupThe first round of the CFP for Recon Montreal will end this Friday March 28, during that phase we preselect a few talk. The CFP end on April 25. #reverseengineering #cybersecurity #offensivesecurity https://recon.cx/2025/cfp.html
buherator
buheratorI'm not even making this up :D
https://www.reddit.com/r/ReverseEngineering/comments/24ar8w/ida_importing_map/
Alec Muffett
alecmuffett@mastodon.social“The real problem with sharing Top Secret data over Signal is not the security of the app, it’s the security of the phone. And mobile phones are not secure against state level threat actor” | @thegrugq is correct, BUT…
https://alecmuffett.com/article/113007
#EndToEndEncryption #signal #trump
/r/netsec
_r_netsec@infosec.exchangeFrida 16.7.0 is out w/ brand new APIs for observing the lifecycles of threads and modules, a profiler, multiple samplers for measuring cycles/time/etc., MemoryAccessMonitor providing access to thread ID and registers, and more 🎉 https://frida.re/news/2025/03/13/frida-16-7-0-released/
Jason Gorman
jasongorman@mastodon.cloudA code generation tool that gets you 80-90% of the way there is like a boat that gets you 80-90% of the way.
You'll need to be a strong swimmer.
Soatok Dreamseeker
soatok@furry.engineerThe Practical Limitations of End-to-End Encryption
Internet discussions about end-to-end encryption are plagued by misunderstandings, misinformation, and some people totally missing the point. Of course, people being wrong on the Internet isn't exactly news. XKCD: Duty Calls "What do you want me to do? LEAVE? Then they'll keep being wrong!" Yesterday, a story in The Atlantic alleged that the Trump Administration accidentally added their editor, Jeffrey Goldberg, to a…
http://soatok.blog/2025/03/25/the-practical-limitations-of-end-to-end-encryption/
Frederic Jacobs
fj@mastodon.socialWhen Signal was designed, our threat model was protecting the communications of civil society, journalists, just regular citizens ...
The threat model of military operations & sharing your hate of Europeans was not what Signal was designed for. Ephemeral messages and cryptographic deniability are not fit for communications that require accountability.
But I appreciate their effort to make government more efficient by adding journalists to the chat instead of requiring to go through FOIA.