Posts
3368Following
712Followers
1580buherator
buheratorConfirmed exploit works on macOS 13.3.1, iOS 15.8.2."
https://github.com/wh1te4ever/WebKit-Bug-256172
Matt Keeter
mjk@hachyderm.iocurrent status: scrawling "FUN JIT COMPILER PROBLEM" in sharpie on a big cardboard box, then putting it on my front lawn and seeing who jumps into it
Slashdot 
slashdot@mastodon.cloud
DNA-Testing Firm 23andMe Files for Bankruptcy https://slashdot.org/story/25/03/24/0517231/dna-testing-firm-23andme-files-for-bankruptcy?utm_source=rss1.0mainlinkanon
Valerie Aurora 🇺🇦
vaurora@mstdn.socialIf you are trying to delete your 23andMe data and get an obnoxious reply asking for ID, tell them no, that's what your password is for, and they will do it. And if they then send you an obnoxious reply saying they will delete everything except the stuff they are required to keep by law, check out this article by actual lawyer @AugustB
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250321-00/?p=110984
buherator
buheratorShow content
https://imperialtriumphant.bandcamp.com/album/goldstar-24-bit-hd-audio
Yining Karl Li
yiningkarlli@mastodon.gamedev.placeTIL that because the FFmpeg project has gained so much experience in hand-writing assembly code to provide huge speedups, they now are putting together a series of lessons for learning assembly:
Vibe coding is fun and all, but this is probably a better use of time!
Elastic Security Labs
elasticseclabs@bird.makeupWe’re adding a new section to @elastic’s HackerOne Bounty Program! Today, we’re opening our SIEM and EDR rules for testing. We’re excited to have another way to thank our community for their efforts on our #detectionengineering. Get more details here: https://go.es.io/4hdKQCI
CFG Bot 🤖
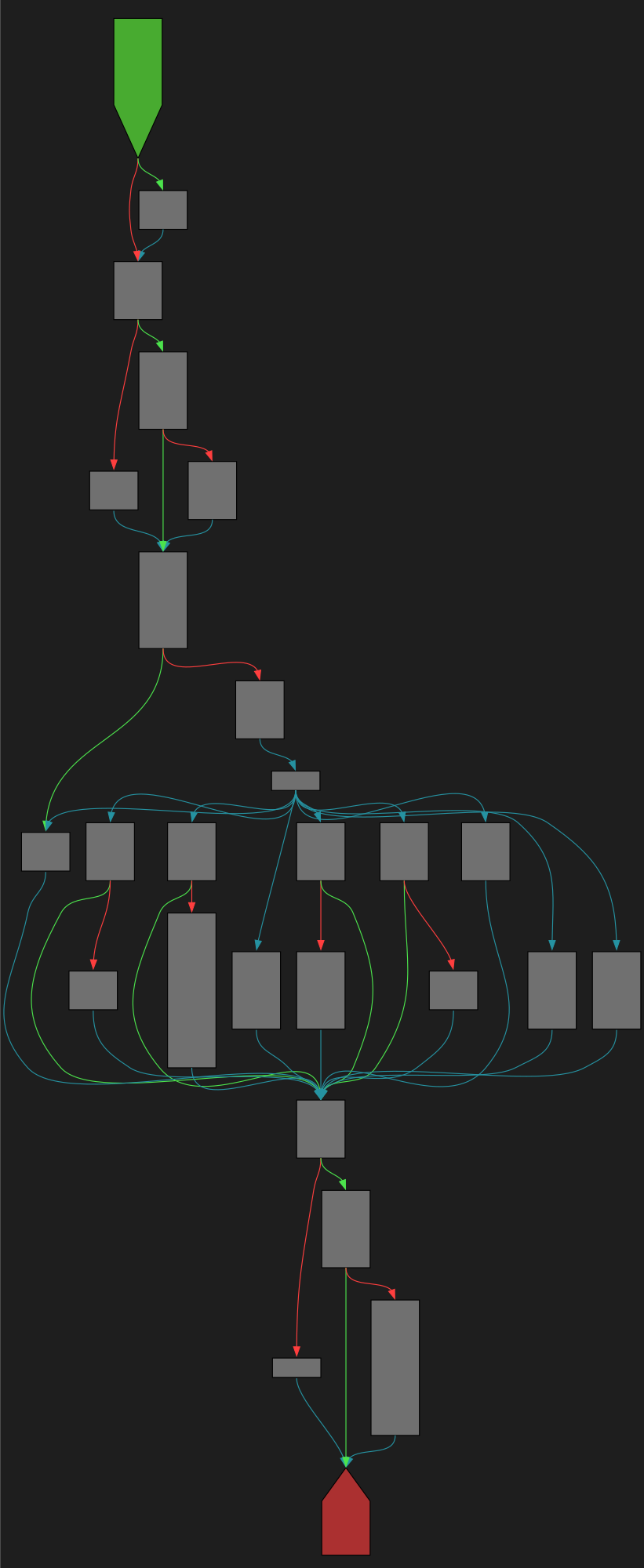
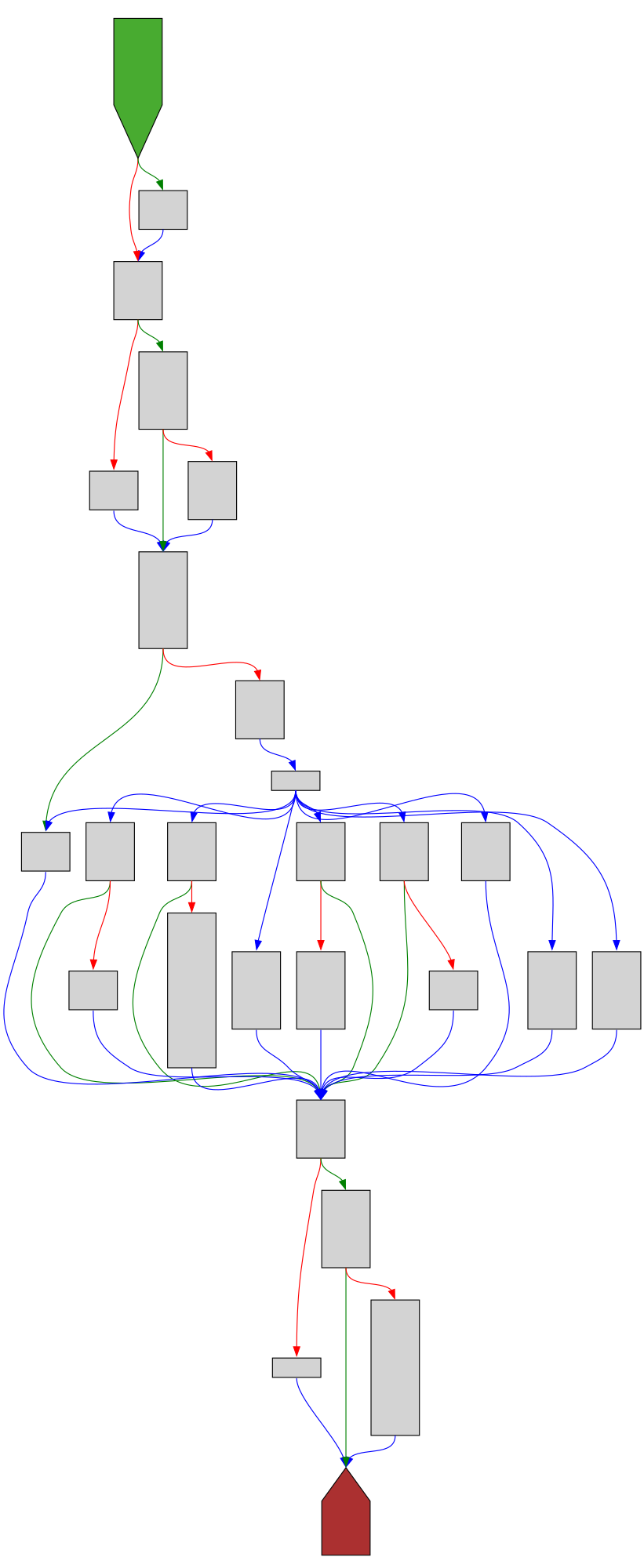
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 0088b2e0
mallopt
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0088b2e0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0088b2e0.json&colors=light
Dare Obasanjo
carnage4life@mas.toCloudflare is now offering a feature called “AI labyrinth” where it serves a series of AI generated pages to AI crawlers that ignore robots.txt directives.
They’re essentially serving AI slop to AI crawlers that are training off of a website’s content without permission.
Deliciously devious. 😈
jn (big endian energy)
jn@boopsnoot.dedoes anyone happen to know a processor with 28-bit instructions?
Simon Willison
simon@simonwillison.netWrote up a note on how the recent Next.js middleware vulnerability works https://simonwillison.net/2025/Mar/23/
buherator
buheratorhttp://blog.quarkslab.com/finding-bugs-in-implementations-of-hqc-the-fifth-post-quantum-standard.html
buherator
buheratorhttps://u1f383.github.io/linux/2025/03/23/a-quick-note-on-CVE-2024-53104.html
buherator
buheratorhttps://u1f383.github.io/linux/2025/03/23/understanding-socket-internals-through-a-series-of-cve-fixes.html
buherator
buheratorhttps://www.horizon3.ai/attack-research/attack-blogs/critical-or-clickbait-github-actions-and-apache-tomcat-rce-vulnerabilities-2025/
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Interesting links of the week:
Strategy:
* https://rusi.org/explore-our-research/publications/commentary/typhoons-cyberspace - @ciaranmartin talks .cn
* https://www.mitre.org/sites/default/files/2022-04/11-strategies-of-a-world-class-cybersecurity-operations-center.pdf - building a world class SOC with MITRE
* https://www.ncsc.gov.uk/whitepaper/security-architecture-anti-patterns - architectural booboos
Threats:
* https://www.mdsec.co.uk/2025/03/red-teaming-with-servicenow/ - red teaming SNow
* https://posts.specterops.io/mapping-snowflakes-access-landscape-3bf232251945 - mapping Snowflake
* https://www.dragos.com/wp-content/uploads/2025/03/Dragos_Littleton_Electric_Water_CaseStudy.pdf - a small case study on how .cn got into your water
* https://supportportal.juniper.net/s/article/2025-03-Reference-Advisory-The-RedPenguin-Malware-Incident?language=en_US - and a larger case study on how they got into Juniper devices
* https://cloud.google.com/blog/topics/threat-intelligence/china-nexus-espionage-targets-juniper-routers - more on Juniper from Mandiant
* https://blog.talosintelligence.com/active-exploitation-of-cisco-ios-xe-software/ - @TalosSecurity gives us the run down on how .cn got into Cisco devices too
Detection:
* https://mr-r3b00t.github.io/crime-mapper/ - reimagining graphs with @UK_Daniel_Card
* https://tinyhack.com/2025/03/13/decrypting-encrypted-files-from-akira-ransomware-linux-esxi-variant-2024-using-a-bunch-of-gpus/ - decrypting Akira
* https://www.stepsecurity.io/blog/harden-runner-detection-tj-actions-changed-files-action-is-compromised - another bugdoor in the supply chain
Bugs:
* https://blog.includesecurity.com/2025/03/memory-corruption-in-delphi/ - memory corruption in memory safe languages
* https://scrapco.de/blog/analysis-of-cve-2025-24813-apache-tomcat-path-equivalence-rce.html - shedding light on the the recent TomCat bug
* https://portswigger.net/research/saml-roulette-the-hacker-always-wins - a SAML guide to lock picking from @gaz
* https://labs.watchtowr.com/by-executive-order-we-are-banning-blacklists-domain-level-rce-in-veeam-backup-replication-cve-2025-23120/ - backdooring your backups
Exploitation:
* https://tmpout.sh/4 - new @tmpout
* https://research.swtch.com/nih - rethinking trust
* https://blog.quarkslab.com/bluetooth-low-energy-gatt-fuzzing.html - fuzzing BTLE
* https://sgued.fr/blog/der-pem-cert/ - certs are hard
* https://i.blackhat.com/us-18/Thu-August-9/us-18-Bulazel-Windows-Offender-Reverse-Engineering-Windows-Defenders-Antivirus-Emulator.pdf - reverse engineering Defender
* https://www.slideshare.net/slideshow/remotemethodguesser-bhusa2021-arsenal/249983357 - fuzzing RMI
* http://gibsonnet.net/blog/dwarchive/NIMSH,%20SSL%20and%20LPM.%20(Chris%27s%20AIX%20Blog).html - with a 10.0 in IBM AIX's NIM install solution, I decided to do some digging... everybody relax, it's fine
Nerd:
* https://latex.vercel.app/ - LaTeX as HTML
* https://artsandculture.google.com/asset/english-electric-kdf9-lyons-electronic-office-computer-installation-bracknell-met-office/sAHERiMe475-Eg?hl=en - old time photos of the UK met office super computers
Solar Designer
solardiz@bird.makeupA few LM hash collisions e.g. for robustness testing of password crackers:
db82323cb0693862: 2275490 or 0/*LUZ@
44b3b60db75c15c1: 2716388 or 1}DC<XT
585e239d32df1998: 8351762 or $;)5D|X
Append empty string hash aad3b435b51404ee to these halves for full LM hashes or mix the halves