Posts
3368Following
712Followers
1580buherator
buheratorhttp://blog.quarkslab.com/finding-bugs-in-implementations-of-hqc-the-fifth-post-quantum-standard.html
buherator
buheratorhttps://u1f383.github.io/linux/2025/03/23/a-quick-note-on-CVE-2024-53104.html
buherator
buheratorhttps://u1f383.github.io/linux/2025/03/23/understanding-socket-internals-through-a-series-of-cve-fixes.html
buherator
buheratorhttps://www.horizon3.ai/attack-research/attack-blogs/critical-or-clickbait-github-actions-and-apache-tomcat-rce-vulnerabilities-2025/
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Interesting links of the week:
Strategy:
* https://rusi.org/explore-our-research/publications/commentary/typhoons-cyberspace - @ciaranmartin talks .cn
* https://www.mitre.org/sites/default/files/2022-04/11-strategies-of-a-world-class-cybersecurity-operations-center.pdf - building a world class SOC with MITRE
* https://www.ncsc.gov.uk/whitepaper/security-architecture-anti-patterns - architectural booboos
Threats:
* https://www.mdsec.co.uk/2025/03/red-teaming-with-servicenow/ - red teaming SNow
* https://posts.specterops.io/mapping-snowflakes-access-landscape-3bf232251945 - mapping Snowflake
* https://www.dragos.com/wp-content/uploads/2025/03/Dragos_Littleton_Electric_Water_CaseStudy.pdf - a small case study on how .cn got into your water
* https://supportportal.juniper.net/s/article/2025-03-Reference-Advisory-The-RedPenguin-Malware-Incident?language=en_US - and a larger case study on how they got into Juniper devices
* https://cloud.google.com/blog/topics/threat-intelligence/china-nexus-espionage-targets-juniper-routers - more on Juniper from Mandiant
* https://blog.talosintelligence.com/active-exploitation-of-cisco-ios-xe-software/ - @TalosSecurity gives us the run down on how .cn got into Cisco devices too
Detection:
* https://mr-r3b00t.github.io/crime-mapper/ - reimagining graphs with @UK_Daniel_Card
* https://tinyhack.com/2025/03/13/decrypting-encrypted-files-from-akira-ransomware-linux-esxi-variant-2024-using-a-bunch-of-gpus/ - decrypting Akira
* https://www.stepsecurity.io/blog/harden-runner-detection-tj-actions-changed-files-action-is-compromised - another bugdoor in the supply chain
Bugs:
* https://blog.includesecurity.com/2025/03/memory-corruption-in-delphi/ - memory corruption in memory safe languages
* https://scrapco.de/blog/analysis-of-cve-2025-24813-apache-tomcat-path-equivalence-rce.html - shedding light on the the recent TomCat bug
* https://portswigger.net/research/saml-roulette-the-hacker-always-wins - a SAML guide to lock picking from @gaz
* https://labs.watchtowr.com/by-executive-order-we-are-banning-blacklists-domain-level-rce-in-veeam-backup-replication-cve-2025-23120/ - backdooring your backups
Exploitation:
* https://tmpout.sh/4 - new @tmpout
* https://research.swtch.com/nih - rethinking trust
* https://blog.quarkslab.com/bluetooth-low-energy-gatt-fuzzing.html - fuzzing BTLE
* https://sgued.fr/blog/der-pem-cert/ - certs are hard
* https://i.blackhat.com/us-18/Thu-August-9/us-18-Bulazel-Windows-Offender-Reverse-Engineering-Windows-Defenders-Antivirus-Emulator.pdf - reverse engineering Defender
* https://www.slideshare.net/slideshow/remotemethodguesser-bhusa2021-arsenal/249983357 - fuzzing RMI
* http://gibsonnet.net/blog/dwarchive/NIMSH,%20SSL%20and%20LPM.%20(Chris%27s%20AIX%20Blog).html - with a 10.0 in IBM AIX's NIM install solution, I decided to do some digging... everybody relax, it's fine
Nerd:
* https://latex.vercel.app/ - LaTeX as HTML
* https://artsandculture.google.com/asset/english-electric-kdf9-lyons-electronic-office-computer-installation-bracknell-met-office/sAHERiMe475-Eg?hl=en - old time photos of the UK met office super computers
Solar Designer
solardiz@bird.makeupA few LM hash collisions e.g. for robustness testing of password crackers:
db82323cb0693862: 2275490 or 0/*LUZ@
44b3b60db75c15c1: 2716388 or 1}DC<XT
585e239d32df1998: 8351762 or $;)5D|X
Append empty string hash aad3b435b51404ee to these halves for full LM hashes or mix the halves
Daniel Lockyer
daniellockyer@bird.makeupMeta recently made a 1 character change to their codebase which saves the equivalent of ~15,000 servers in capacity per year 🤯
Mark Wyner Won’t Comply 
markwyner@mas.to
Back in 2020, Reporters without Borders teamed up with Minecraft to build an in-game library of censored books. They call it The Uncensored Library.
My friend @SrRochardBunson just reminded me about it. I forgot all about it, and didn’t even know it was still rolling.
https://uncensoredlibrary.com/en
#Censorship #Library #Libraries #Minecraft #Journalism #Guerrilla
Eniko (moved ➡ gamedev.place)
eniko@peoplemaking.gamesIf a company has genetic data
And it's going bankrupt
And that causes one of the biggest economies in the world, California, to warn people to delete their data before that happens
Because they're very concerned about who the genetic data will be sold to in bankruptcy court
Idk man maybe it should just be illegal to sell genetic data in bankruptcy court? Or it should require stringent oversight and regulation?
tmp.0ut
tmpout@bird.makeupWould you look at that, it's tmp.0ut Volume 4! Happy Friday, hope you enjoy this latest issue!
Juhis
hamatti@mastodon.world"How do you deal with code snippets in blog posts getting outdated?"
Every time I give a talk about blogging for developers, I'm asked this. Now I started to take action with the first iteration of the solution.
I added version metadata to my blog posts and display them at the start of the post.
https://hamatti.org/posts/track-software-versions-for-technical-blog-posts/
Programming Quotes
programming_quotes@mastodon.socialWe're programmers. Programmers are, in their hearts, architects, and the first thing they want to do when they get to a site is to bulldoze the place flat and build something grand. We're not excited by incremental renovation: tinkering, improving, planting flower beds.
— Joel Spolsky
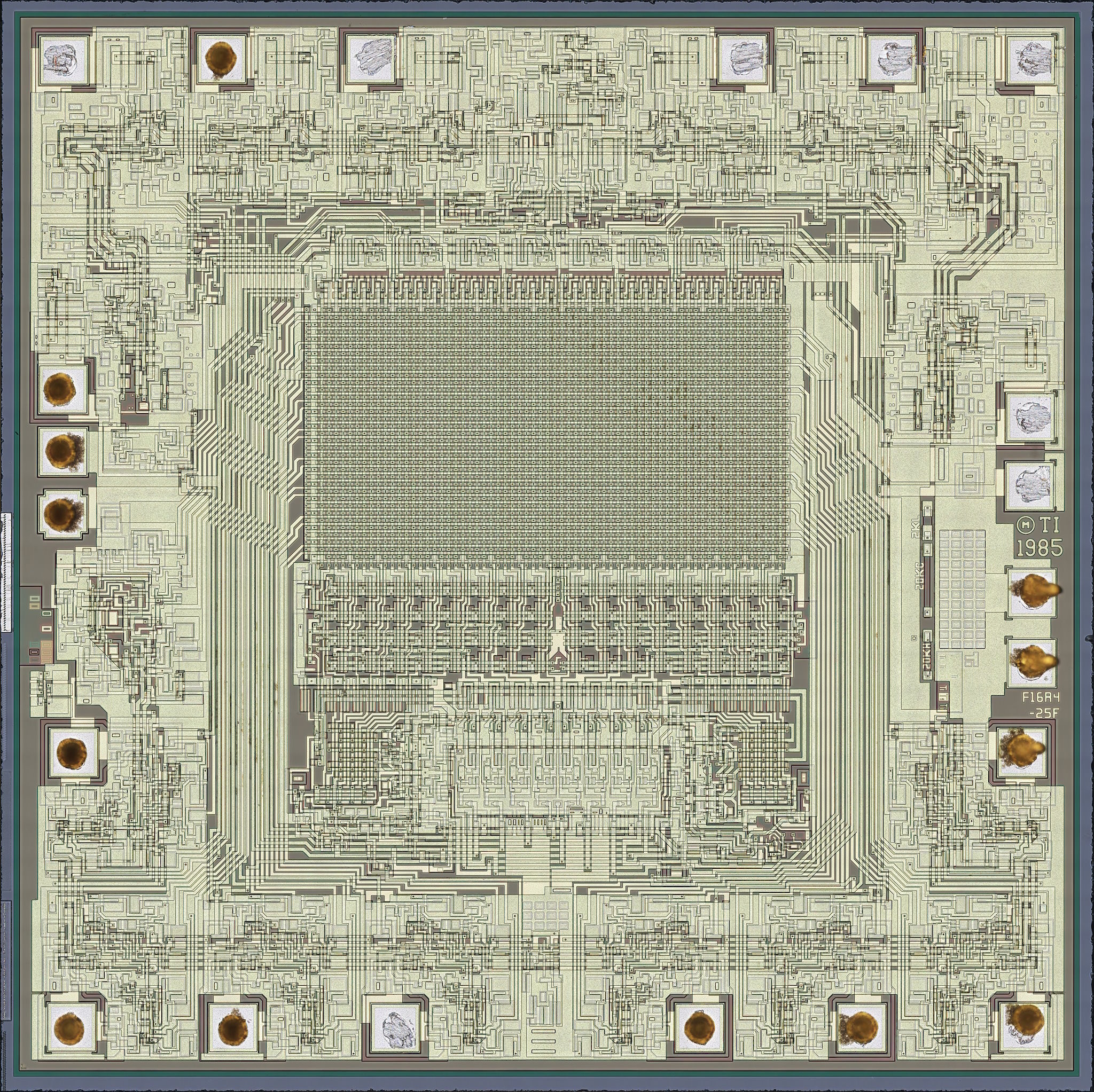
Hello and welcome to this week's installment of #nakeddiefriday !
The guest of today is the TIBPAL16R4 by TI, a programmable array logic chip made with bipolar logic. The die has 2 metal layers, its maskwork produced in 1985. A short thread follows.
More info and hi-res pano at: https://siliconpr0n.org/archive/doku.php?id=infosecdj:ti:tibpal16r4
#electronics #reverseengineering #microscopy #icreverseengineering
Filippo Valsorda
filippo@abyssdomain.expertIt’s disheartening to see AI reactionism lead my community to a 180° on copyright.
Everyone is merrily attacking LibGen now. If it didn’t exist, big tech companies would still find training data, it just wouldn’t be accessible to regular people.
buherator
buheratorhttps://projectdiscovery.io/blog/discourse-backup-disclosure-rails-send_file-quirk
This is CVE-2024-53991
buherator
buheratorhttps://swarm.ptsecurity.com/last-barrier-destroyed-or-compromise-of-fuse-encryption-key-for-intel-security-fuses/
raptor 
raptor@infosec.exchange
Rejoice! 🎉
My idalib-based vulnerability research tools are now fully compatible with Windows 🪟
Please test them and report any bugs 🪲
https://security.humanativaspa.it/streamlining-vulnerability-research-with-ida-pro-and-rust/
(PS. Ya like my GPT writing style? 🚀)
CFG Bot 🤖
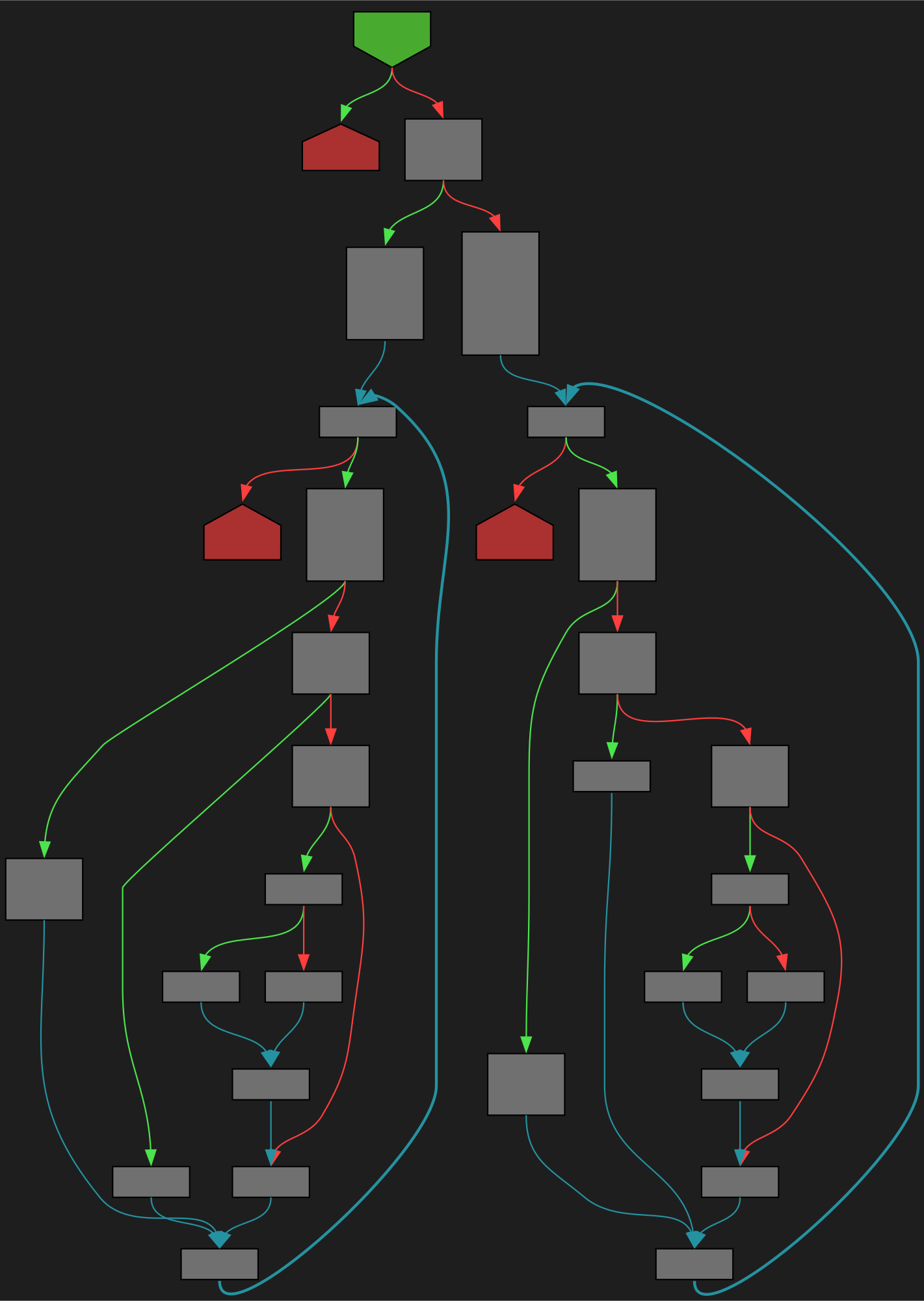
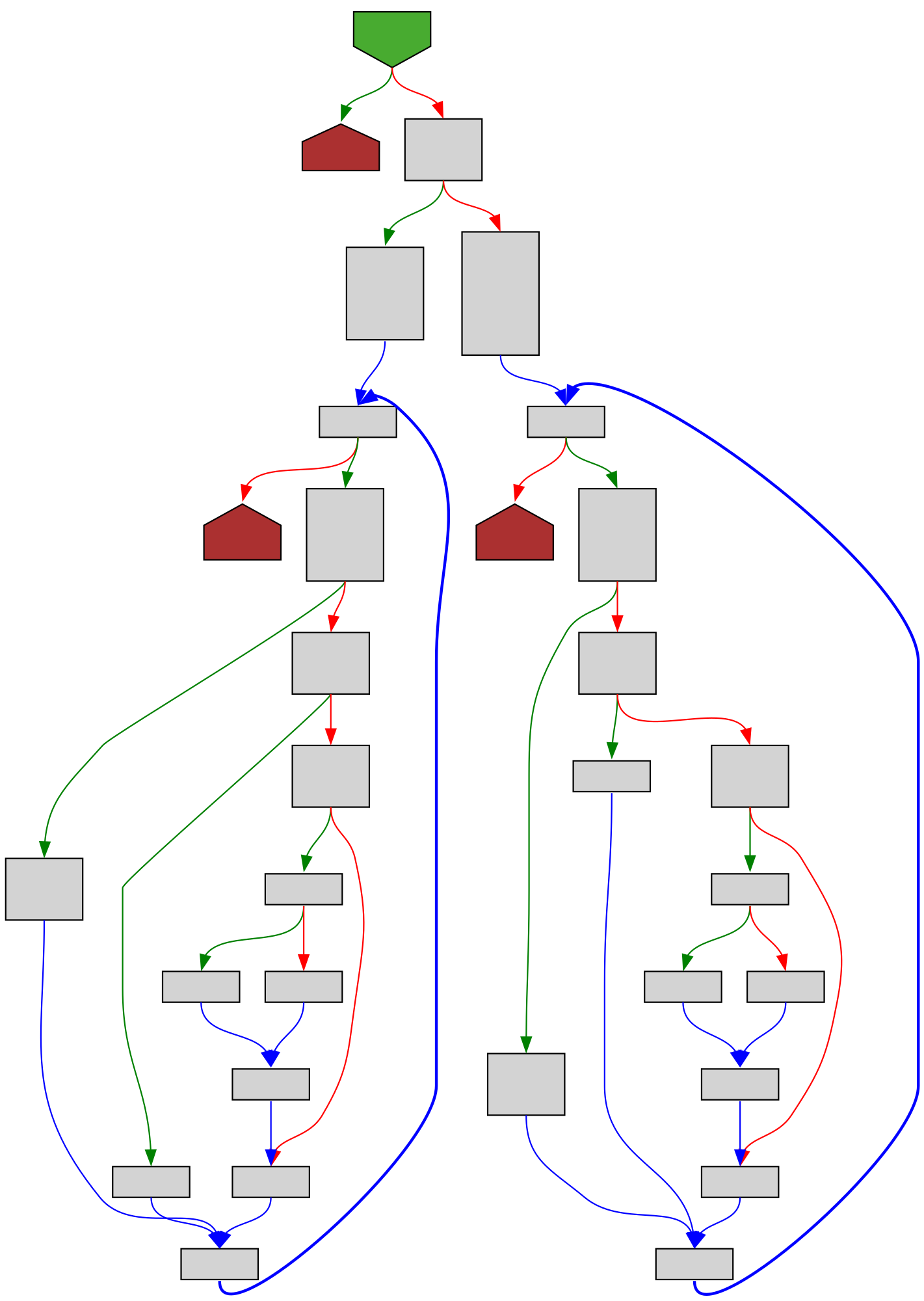
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
File: src/cmd/compile/internal/abt/avlint32.go:175 https://github.com/golang/go/blob/refs/tags/go1.23.4/src/cmd/compile/internal/abt/avlint32.go#L175
func (t *T) Intersection(u *T, f func(x, y interface{}) interface{}) *T
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Fcompile%2Finternal%2Fabt%2Favlint32.go%23L175&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Fcompile%2Finternal%2Fabt%2Favlint32.go%23L175&colors=light