Posts
2929Following
697Followers
1538Project Zero Bot
p0botlibxslt: use-after-free in xsltParseStylesheetProcess
https://project-zero.issues.chromium.org/issues/382015274
CVE-2024-55549
AttackerKB
attackerkbTopic description: "Path Equivalence: 'file.Name' (Internal Dot) leading to Remote Code Execution and/or Information disclosure and/or malicious content added to uploaded files via write enabled Default Servlet in Apache Tomcat. ..."
"On March 10, 2025, the Apache Software Foundation [published](https://lists.apache.org/thread/j5fkjv2k477os90nczf2v9l61fb0kkgq) an advisory for [CVE-2025-24813](https://nvd.nist.gov/vuln/detail/CVE-2025-24813), an unauthenticated remote code execution vulnerability in Apache Tomcat’s “partial PUT” feature ..."
Link: https://attackerkb.com/assessments/1a24556d-24fb-4017-be67-e4ab39c76566
David Smith
Catfish_Man@mastodon.socialSome really impressive work from my old team here: https://forums.swift.org/t/the-future-of-serialization-deserialization-apis/78585
If you care about Codable and/or serialization in Swift in general, definitely check it out
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250317-00/?p=110970
buherator
buheratorhttps://starlabs.sg/blog/2025/03-star-labs-windows-exploitation-challenge-2025-writeup/
Molly White
molly0xfff@hachyderm.ioExciting: The Ghost team has just released the beta version of its ActivityPub support for people using their hosted service
2600 Magazine
2600@mastodon.onlineGet your speaker submissions in TODAY for early consideration at this year's HOPE conference! @hopeconf https://www.2600.com/content/early-deadline-hope-talk-submissions-monday
buherator
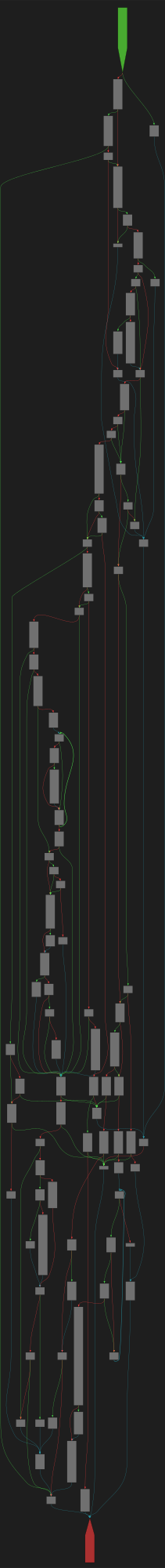
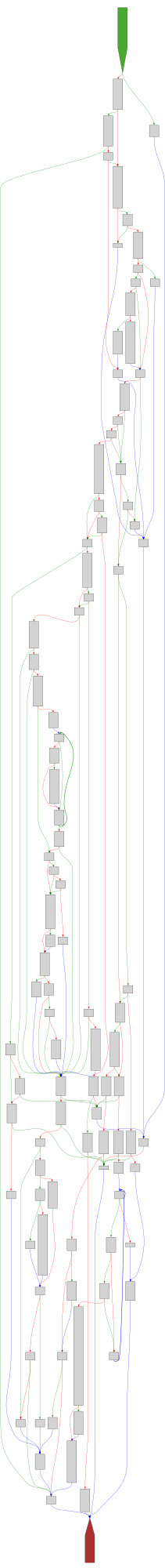
buheratorCFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a1eaec0
load_page
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a1eaec0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a1eaec0.json&colors=light
Aaron J. Waltke
GoodAaron@mastodon.socialOf all the #StarTrekProdigy memes I’ve seen, this one hits the hardest for me.
buherator
buheratorbuherator
buheratorhttps://blog.cloudflare.com/validating-leaked-passwords-with-k-anonymity/
buherator
buheratorhttps://blog.cloudflare.com/validating-leaked-passwords-with-k-anonymity/
buherator
buheratorAnd again, let's not forget that participating origins agreed to this type of data use (hell, they may even need to configure what fields to snoop on!) - I wonder if their end-user privacy policies include this detail...
buherator
buherator#HanlonsRazor