Posts
2991Following
698Followers
1545buherator
buheratorhttps://starlabs.sg/blog/2025/03-star-labs-windows-exploitation-challenge-2025-writeup/
Molly White
molly0xfff@hachyderm.ioExciting: The Ghost team has just released the beta version of its ActivityPub support for people using their hosted service
2600 Magazine
2600@mastodon.onlineGet your speaker submissions in TODAY for early consideration at this year's HOPE conference! @hopeconf https://www.2600.com/content/early-deadline-hope-talk-submissions-monday
buherator
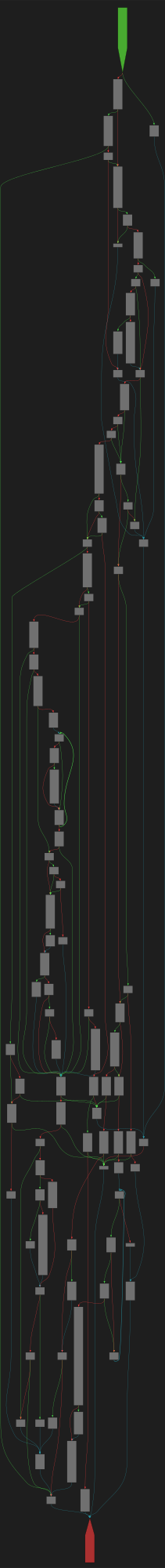
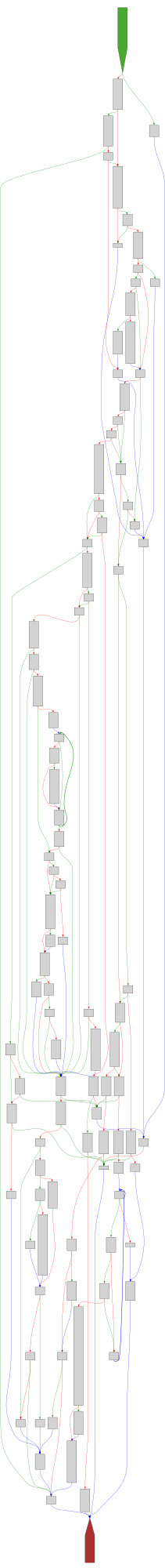
buheratorCFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a1eaec0
load_page
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a1eaec0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a1eaec0.json&colors=light
Aaron J. Waltke
GoodAaron@mastodon.socialOf all the #StarTrekProdigy memes I’ve seen, this one hits the hardest for me.
buherator
buheratorbuherator
buheratorhttps://blog.cloudflare.com/validating-leaked-passwords-with-k-anonymity/
buherator
buheratorhttps://blog.cloudflare.com/validating-leaked-passwords-with-k-anonymity/
buherator
buheratorAnd again, let's not forget that participating origins agreed to this type of data use (hell, they may even need to configure what fields to snoop on!) - I wonder if their end-user privacy policies include this detail...
buherator
buherator#HanlonsRazor
buherator
buheratorHIBP API is anonymized in the first place. They must already have an "even more" anonymized yes/no signal from their detection service (whether it's using the anon API or a full HIBP copy), and at CF's scale I don't think anyone wants to receive all the non-anonymized request fragments for perf/bandwidth reasons alone.
Sure there may be an evil team at CF who secretly look at creds, but this stat is not an evidence of that.
hanno
hanno@mastodon.socialThis was one of the instances of insecure openid connect keys I blogged about recently https://blog.hboeck.de/archives/909-Mixing-up-Public-and-Private-Keys-in-OpenID-Connect-deployments.html the host auth.univie.ac.at has an openid connect configuration file. It points to https[://]auth.univie.ac.at/jwk for its jwks_uri that contains the public keys. Apparently, one of those keys is an example key used in the software "OpenID-Connect-Java-Spring-Server". Therefore, the private key is what I like to call a "Public Private Key".
buherator
buherator"Our data analysis focuses on traffic from Internet properties on Cloudflare’s free plan, which *includes leaked credentials detection as a built-in feature.*"
Allele Security Intelligence
alleleintel@infosec.exchangeWe have released the files for the research that led to CVE-2024-36904. It contains the codes, the original kernel source, the patch and the modified kernel source that help to trigger the KASAN splat. If you want to play with the vulnerability, you can use the files.
https://github.com/alleleintel/research/tree/master/CVE-2024-36904/