Posts
3139Following
708Followers
1555buherator
buheratorhttps://betterweb.qwant.com/en/2024/11/08/ecosia-and-qwant-join-forces-to-develop-european-search-index/
#adtech
Michael Coppola
mncoppola@bird.makeupIMO the hallmark of a "senior" vuln researcher is not only their ability to discover/exploit vulnerabilities in difficult targets, but, critically, their ability to effectively *invest and allocate resources*. Knowing when to sink more time/effort into an attack surface or difficult bug, and when you need to stop and *move on* is one of the hardest questions as a researcher, and you only develop that instinct through experience and hard-learned lessons.
Rodrigo Branco
bsdaemon@bird.makeupThat is actually my main fear with learning thru CTFs. The sense of time and possibility is quite different. Almost like playing fast chess versus longer time chess games. It could be good practice but it very likely is detrimental if done too often.
X41 D-Sec GmbH
x41sec@infosec.exchangeX41 performed an audit of Hickory DNS which is an open source Rust based DNS client, server, and resolver. We were sponsored by the great folks at @ostifofficial and supported by @ProssimoISRG
Our full report can be downloaded here: https://x41-dsec.de/security/research/job/news/2025/03/10/hickory-review-2025/
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Simply smashing a device that you have physical access to is scored as CVSS 5.2 (Medium):
If anyone else ever needs this, here is a pin map of Renesas RL78/F13. Pads with ? are power supply, but there seems to be a bit too many of them, maybe for bonding options.
Jiska
naehrdine@bird.makeupBroadcom and Cypress chips have the same HCI "backdoor" allowing to write to the Bluetooth chip's RAM. This feature is used for firmware patches.
We didn't request CVEs for that 9 years ago. Instead, we built the InternalBlue Bluetooth research framework.
https://github.com/seemoo-lab/internalblue
Xeno Kovah
xenokovah@infosec.exchangeI’ve posted a detailed explanation of why the claimed ESP32 Bluetooth chip “backdoor” is not a backdoor. It’s just a poor security practice, which is found in other Bluetooth chips by vendors like Broadcom, Cypress, and Texas Instruments too. https://darkmentor.com/blog/esp32_non-backdoor/
buherator
buheratorhttps://tested-store.com/collections/demerit-badges
I need something like these for the next #failnight!
sha1lan
sha1lan@infosec.exchangeThe tension between vulnerability power and exploit technique flexibility
buherator
buheratorShow content
https://youtu.be/sZIWwCO7RWc?si=Jemru9y1SV5X1o4-&t=213
(If so, I wanna hang out with the mushrooms from Hollow Earth)
buherator
buheratorShow content
https://video.infosec.exchange/w/1GfaMyxuFnhWkxzsWDPXfS
Stop devaluing your writing by slapping an ugly as fuck error-ridden AI image on your article/blogpost/newsletter.
Rairii 

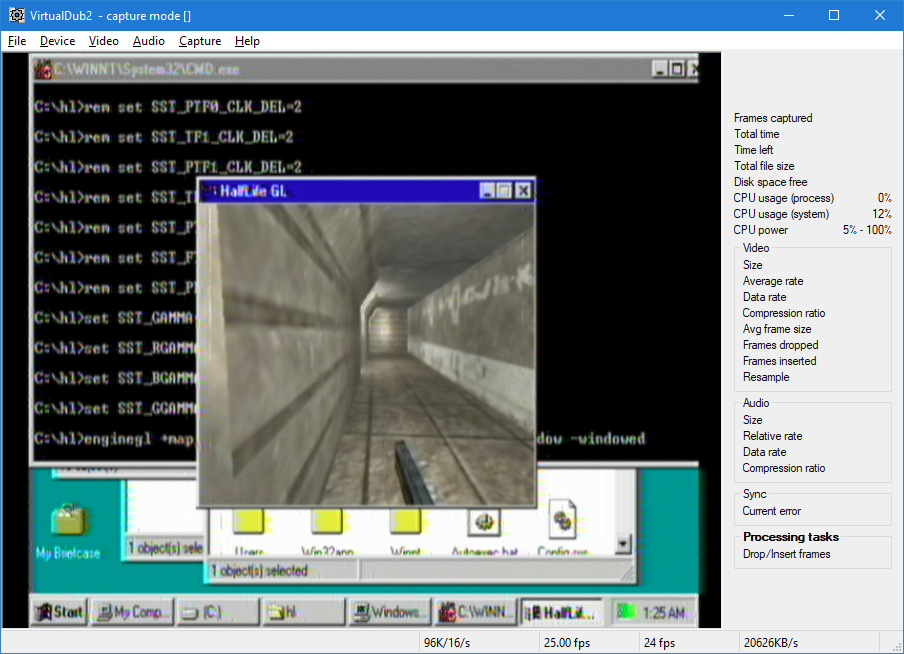
Rairii@labyrinth.zone
at 3fps at most - in a 320x240 window (it doesnt even reach 1fps in 640x480 fullscreen) - but it does run
the actual rtm doesn't show any valid display modes for some reason
Simon Zerafa (Status:  😊)
😊)
simonzerafa@infosec.exchange
The second oldest digital computer in the world is now working 🙂🤷♂️
Well done @usagielectric for getting it in a running state!
The oldest is the Harwell Dekatron at @tnmoc in Bletchley Park, which is also very cool and well worth visiting 😁🖖
Misinformation-Superhighwayman
DamienWise@aus.socialIt's easy to get scared when headlines combine terms like "backdoor", "Bluetooth", and "a billion devices".
Should you be worried? No.
The "attack" for ESP32 chips in some Internet of Things devices is some undocumented commands that are likely to be for testing by the manufacturer, Espressif, the in the factory. It cannot spread from one device to another like a virus/worm, and it takes a lot more than being within Bluetooth range -- it requires physical access to I/O pins on the chip itself or access to a USB port (if one is present). That's just the standard way to flash the firmware. It should go without saying that if a malicious person has physical access to the inside of your device then you may have more security concerns.
It's been fascinating to watch the propagation of fear and misinformation in a niche where I have dabbled enough to develop a bit of technical proficiency.
My interpretation of events is that Tarlogic Security is spreading panic to gain attention or notoriety.
Undocumented "backdoor" found in Bluetooth chip used by a billion devices:
https://www.bleepingcomputer.com/news/security/undocumented-backdoor-found-in-bluetooth-chip-used-by-a-billion-devices/
NIST (National Institute of Standards and Technology) has a CVE:
https://nvd.nist.gov/vuln/detail/CVE-2025-27840
Edit to update:
Espressif’s Response to Claimed Backdoor and Undocumented Commands in ESP32 Bluetooth Stack
https://www.espressif.com/en/news/Response_ESP32_Bluetooth