Posts
3398Following
713Followers
1581SinSinology
sinsinology@bird.makeupit took me so much time to finish this exploit but I finally did it! my first guest-to-host virtualbox escape is finally ready, using a combination of 2 bugs I can target the latest version :)
Eternal thank you to my dear friend Corentin @onlytheduck for constantly encouraging me and guiding me how to approach, research and exploit hypervisors ✊⭐️
buherator
buheratorhttps://www.ibm.com/support/pages/node/7183835?myns=swgother&mynp=OCSWG60&mynp=OCSSB23CE&mynp=OCSSTS2D&mynp=OCSSC5L9&mynp=OCSS9QQS&mync=A&cm_sp=swgother-_-OCSWG60-OCSSB23CE-OCSSTS2D-OCSSC5L9-OCSS9QQS-_-A
Disconnect3d
disconnect3d@infosec.exchangeReleased Pwndbg 2025.02.19 with new commands for dumping Linux kernel nftables, initial LoongArch64 support and more!
See changelog on https://github.com/pwndbg/pwndbg/releases/tag/2025.02.19 !
#pwndbg #gdb #pwning #reverseengineering #binaryexploitation #kernel #debugging
buherator
buheratorhttps://pluralistic.net/2025/02/20/privacy-first-second-third/
Programming Quotes
programming_quotes@mastodon.socialComputers make it easier to do a lot of things, but most of the things they make it easier to do don't need to be done.
— Andy Rooney
buherator
buheratorHalvarFlake
HalvarFlake@mastodon.socialI gave a day 1 closing keynote at DistrictCon yesterday. Surprisingly, it was a security talk about memory safety.
Slides are here:
https://docs.google.com/presentation/d/1-CgBbVuFE1pJnB84wfeq_RadXQs13dCvHTFFVLPYTeg/edit?usp=drivesdk
buherator
buheratorhttps://irisc-research-syndicate.github.io/2025/02/14/writing-a-ghidra-processor-module/?ref=blog.exploits.club
"In this article we will create a Ghidra processor module for the iRISC processors, these processors are embedded in the ConnectX series of NICs from NVIDIA/Mellanox."
Not a beginners tutorial, as it skims over many important steps and details, but still good to have more of these as there's always a trick or two to learn.
Hexacorn 

hexacorn@infosec.exchange
Optimizing the regexes, or not
https://www.hexacorn.com/blog/2025/02/22/optimizing-the-regexes-or-not/
exploits.club
exploitsclub@bird.makeupIt's EXPLOIT CLUB DAY 📰
Linux kernel goodies from @h0mbre_
@patch1t spends another week showing you no patch is safe
@vv474172261 makes Microsoft re-think their bounty program
USB Restricted Mode Bypass RCA from @quarkslab
+ Jobs and MORE 👇
Disconnect3d
disconnect3d_pl@bird.makeupReleased Pwndbg 2025.02.19 with new commands for dumping Linux kernel nftables, initial LoongArch64 support and more!
See changelog on https://github.com/pwndbg/pwndbg/releases/tag/2025.02.19 !
h0mbre
h0mbre_@bird.makeupI tried my hand at exploiting an nday on the Google Container Optimized OS instance in kCTF but sadly was very late to the party. Here is my exploit write-up for it. I learned a lot during the process, let me know what you think. I'll post TL;DR in thread
https://h0mbre.github.io/Patch_Gapping_Google_COS/
Project Zero Bot
p0botLinux: io_uring: UAF of io_ev_fd; io_eventfd_do_signal() frees on refcount drop without RCU delay
https://project-zero.issues.chromium.org/issues/388499293
CVE-2025-21655
buherator
buheratorhttps://www.postgresql.org/about/news/postgresql-174-168-1512-1417-and-1320-released-3018/
This fixes a regression introduced by the latest vulnerability fix:
"The fix for CVE-2025-1094 caused the quoting functions to not honor their string length parameters and, in some cases, cause crashes."
buherator
buheratorhttps://exim.org/static/doc/security/CVE-2025-26794.txt
Configs using SQLite may be vulnerable.
CFG Bot 🤖
cfgbot@mastodon.socialProject: python/cpython https://github.com/python/cpython
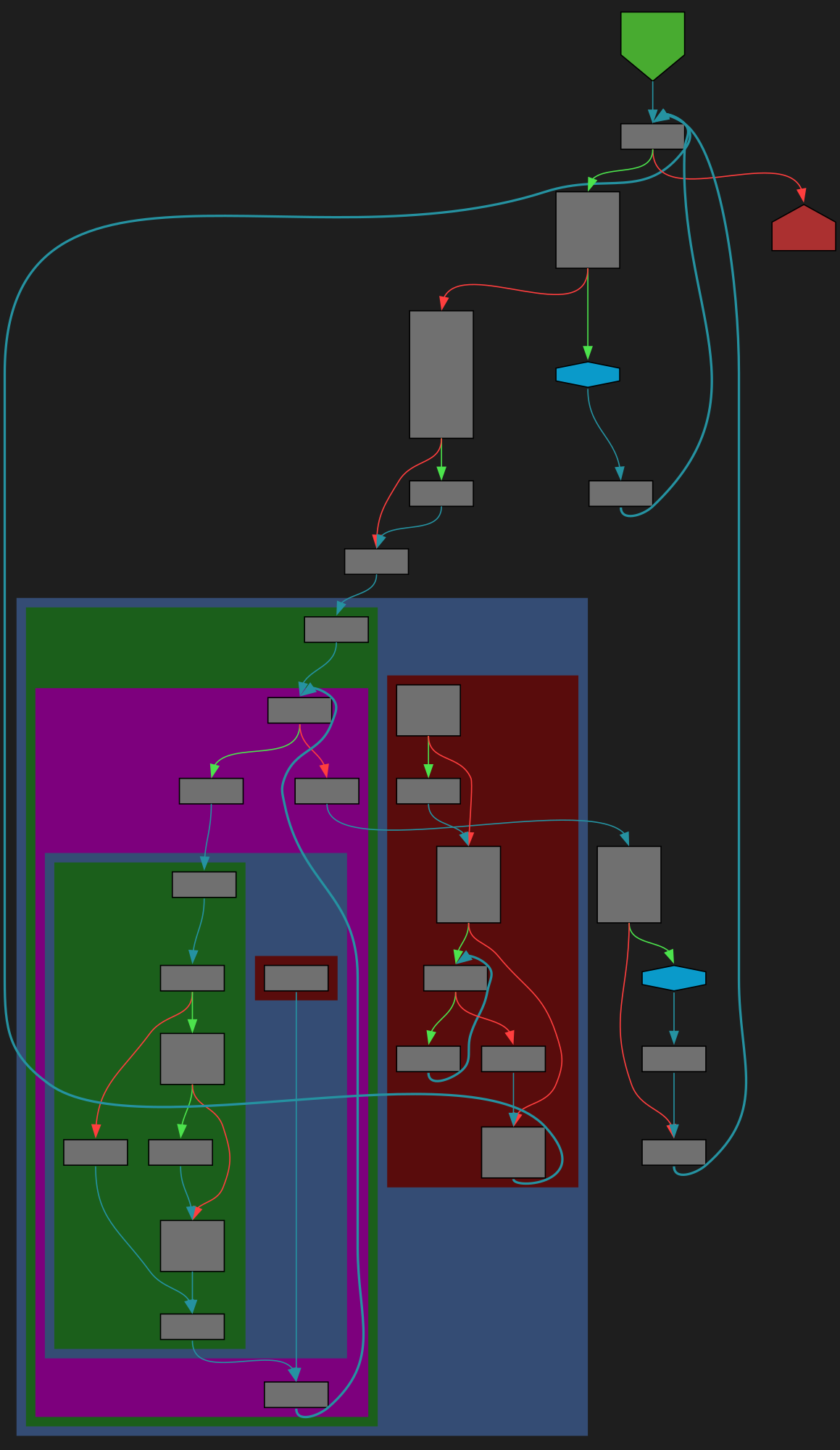
File: Lib/pathlib/_abc.py:504 https://github.com/python/cpython/blob/2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd/Lib/pathlib/_abc.py#L504
def walk(self, top_down=True, on_error=None, follow_symlinks=False):
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fpython%2Fcpython%2Fblob%2F2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd%2FLib%2Fpathlib%2F_abc.py%23L504&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fpython%2Fcpython%2Fblob%2F2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd%2FLib%2Fpathlib%2F_abc.py%23L504&colors=light
CFG Bot 🤖
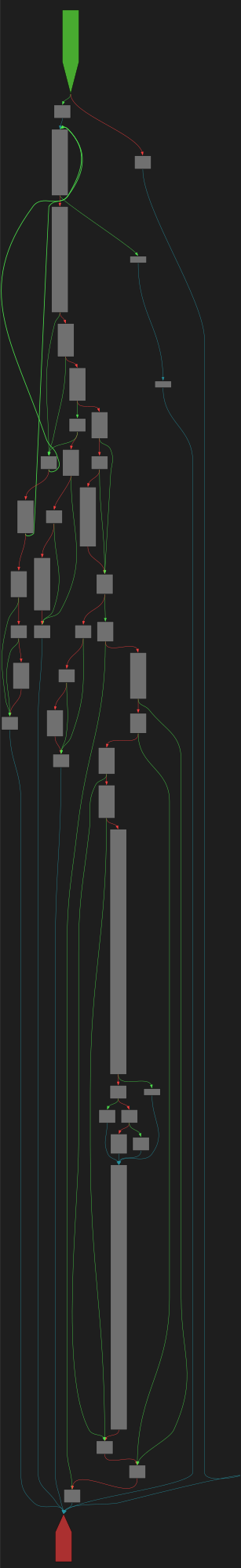
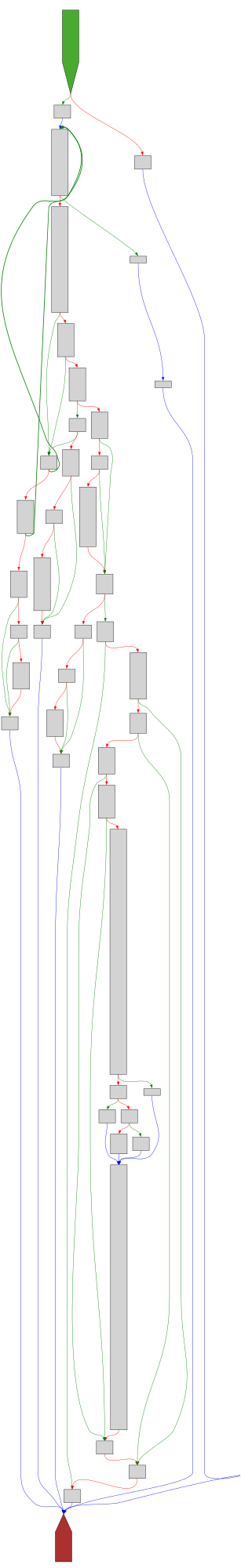
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75ab2fe6c
VerifyCertChain
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75ab2fe6c.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75ab2fe6c.json&colors=light
Royce Williams
tychotithonus@infosec.exchangeThe hashcat.net site is down -- side effect of maintenance by hosting provider. Being worked.
[Edit: back up a week later]
Current release (GitHub): https://github.com/hashcat/hashcat/releases/tag/v6.2.6
Convenience Wayback links:
Main page:
https://web.archive.org/web/20250211000850/hashcat.net/hashcat/
Rules:
https://web.archive.org/web/20250211234251/https://hashcat.net/wiki/doku.php?id=rule_based_attack
Example hashes :
https://web.archive.org/web/20250216060927/https://hashcat.net/wiki/doku.php?id=example_hashes
Recent beta:
https://web.archive.org/web/20250130114639/https://hashcat.net/beta/