Posts
3373Following
712Followers
1579exploits.club
exploitsclub@bird.makeupIt's EXPLOIT CLUB DAY 📰
Linux kernel goodies from @h0mbre_
@patch1t spends another week showing you no patch is safe
@vv474172261 makes Microsoft re-think their bounty program
USB Restricted Mode Bypass RCA from @quarkslab
+ Jobs and MORE 👇
Disconnect3d
disconnect3d_pl@bird.makeupReleased Pwndbg 2025.02.19 with new commands for dumping Linux kernel nftables, initial LoongArch64 support and more!
See changelog on https://github.com/pwndbg/pwndbg/releases/tag/2025.02.19 !
h0mbre
h0mbre_@bird.makeupI tried my hand at exploiting an nday on the Google Container Optimized OS instance in kCTF but sadly was very late to the party. Here is my exploit write-up for it. I learned a lot during the process, let me know what you think. I'll post TL;DR in thread
https://h0mbre.github.io/Patch_Gapping_Google_COS/
Project Zero Bot
p0botLinux: io_uring: UAF of io_ev_fd; io_eventfd_do_signal() frees on refcount drop without RCU delay
https://project-zero.issues.chromium.org/issues/388499293
CVE-2025-21655
buherator
buheratorhttps://www.postgresql.org/about/news/postgresql-174-168-1512-1417-and-1320-released-3018/
This fixes a regression introduced by the latest vulnerability fix:
"The fix for CVE-2025-1094 caused the quoting functions to not honor their string length parameters and, in some cases, cause crashes."
buherator
buheratorhttps://exim.org/static/doc/security/CVE-2025-26794.txt
Configs using SQLite may be vulnerable.
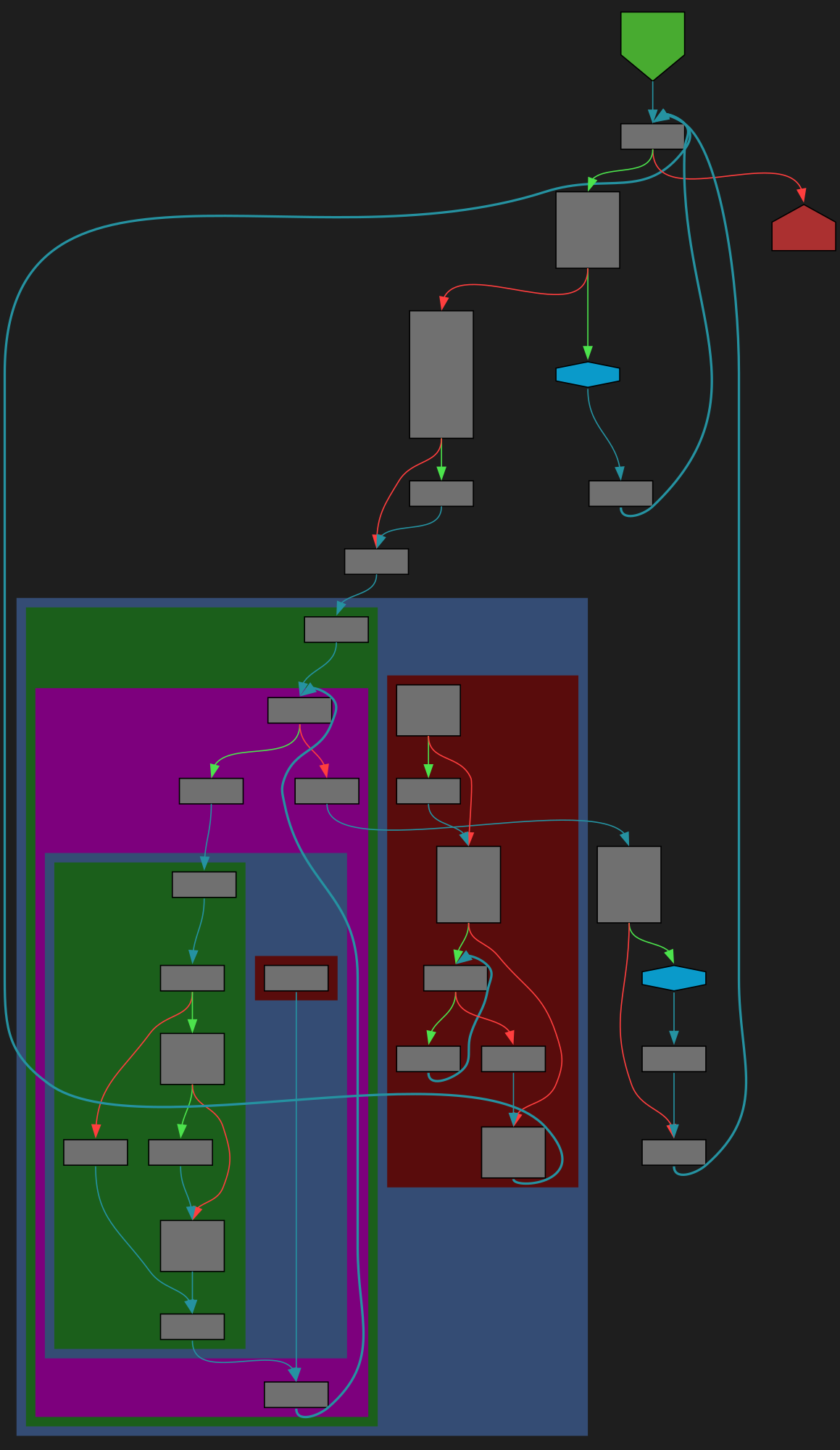
CFG Bot 🤖
cfgbot@mastodon.socialProject: python/cpython https://github.com/python/cpython
File: Lib/pathlib/_abc.py:504 https://github.com/python/cpython/blob/2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd/Lib/pathlib/_abc.py#L504
def walk(self, top_down=True, on_error=None, follow_symlinks=False):
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fpython%2Fcpython%2Fblob%2F2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd%2FLib%2Fpathlib%2F_abc.py%23L504&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fpython%2Fcpython%2Fblob%2F2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd%2FLib%2Fpathlib%2F_abc.py%23L504&colors=light
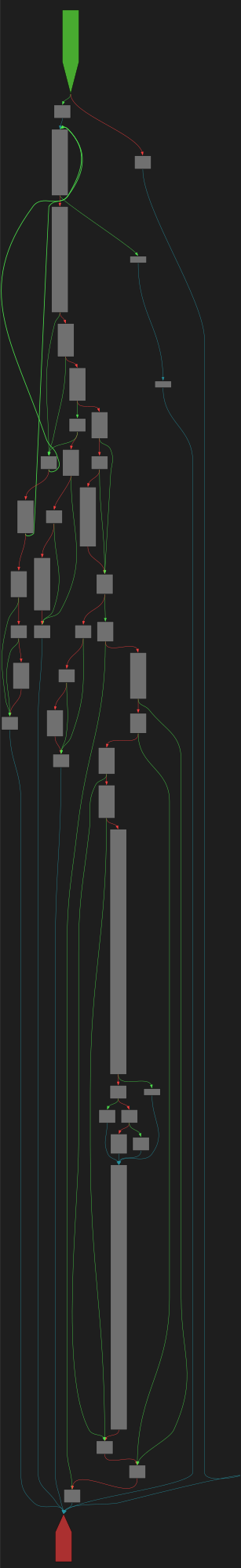
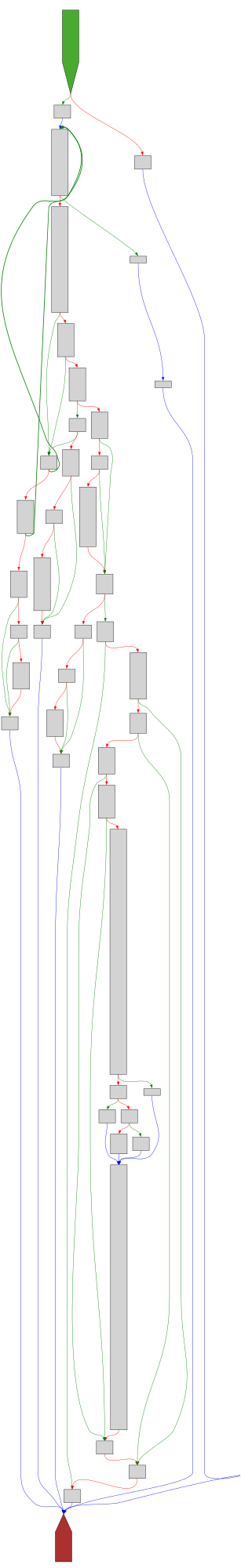
CFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75ab2fe6c
VerifyCertChain
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75ab2fe6c.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75ab2fe6c.json&colors=light
Royce Williams
tychotithonus@infosec.exchangeThe hashcat.net site is down -- side effect of maintenance by hosting provider. Being worked.
[Edit: back up a week later]
Current release (GitHub): https://github.com/hashcat/hashcat/releases/tag/v6.2.6
Convenience Wayback links:
Main page:
https://web.archive.org/web/20250211000850/hashcat.net/hashcat/
Rules:
https://web.archive.org/web/20250211234251/https://hashcat.net/wiki/doku.php?id=rule_based_attack
Example hashes :
https://web.archive.org/web/20250216060927/https://hashcat.net/wiki/doku.php?id=example_hashes
Recent beta:
https://web.archive.org/web/20250130114639/https://hashcat.net/beta/
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Interesting links of the week:
Strategy:
* https://dl.acm.org/doi/10.1145/3594553 - refining TI with automated labelling
Threats:
* https://blog.talosintelligence.com/salt-typhoon-analysis/ - Salt Typhoon analysis from @TalosSecurity
* https://www.inversecos.com/2025/02/an-inside-look-at-nsa-equation-group.html - a Chinese view on Equation Group
Detection:
* https://blog.thinkst.com/2025/02/almost-famous-behind-the-scenes-of-a-feature-that-didnt-make-the-cut.html - building canary tokens with unconstrained delegation
Hard hacks:
* https://kindlemodding.org/ - modding the Kindle
* https://www.die-welt.net/2025/02/unauthenticated-rce-in-grandstream-ht802v2-and-probably-others-using-gs_test_server-dhcp-vendor-option/ - hacking hardware via DHCP vendor options
Hardening:
* https://neapay.com/viewposts.html?category=BASE24 - variable quality but details on Base24
blacktop
blacktop@mastodon.socialHigh level diff of iOS 18.3.1 vs. iOS 18.4beta1 🎉
https://github.com/blacktop/ipsw-diffs/blob/main/18_3_1_22D72__vs_18_4_22E5200s/README.md
yossarian (1.3.6.1.4.1.55738)
yossarian@infosec.exchangemy colleagues Alexis and Brad at @trailofbits put together a great post on a basic security mistake that we keep making: attacker-controlled recursion. my favorite thing about these is that they're (1) trivial to find and (2) *way* more impactful than normal DoS spam.
the post contains some great examples of these, including real vulnerabilities in Protobuf and ElasticSearch:
https://blog.trailofbits.com/2025/02/21/dont-recurse-on-untrusted-input/
they'll also be presenting their findings at @DistrictCon tomorrow!
https://www.districtcon.org/bios-and-talks-2025/low-effort-dos-with-recursion
Rust Language
rust@social.rust-lang.orgRust 1.85.0 has been released! 🌈🦀✨
Not only does this release add *async closures*, it also includes a whole *new Rust Edition*, Rust 2024! 🎆🚀
Check out the blog post for an overview of all the changes and additions: https://blog.rust-lang.org/2025/02/20/Rust-1.85.0.html
Andrew Zonenberg
azonenberg@ioc.exchangePeriodic reminder to the fedi EE / embedded systems community: I have a lot of lab capabilities and resources that the average hobbyist can't afford, and am willing to offer them up on reasonable terms (i.e. FREE in many cases) to help people out.
As a general rule if you're not making money on it (i.e. hobbyist/noncommercial/academic project) and it's not a major time commitment or consumable cost for me, all I ask is that you pay return shipping if you want the hardware sent back to you afterwards. For anything large or commercial in nature, I'm still potentially interested but we'd have to discuss compensation first.
Capabilities and equipment available:
* 3D planar EM simulation (Sonnet Pro)
* 5 3/4 digit multimeters (R&S HMC8012)
* Various oscilloscopes to 16 GHz BW (PicoScope 6424E, LeCroy WaveRunner 8404M-MS, LeCroy SDA 816Zi-A) plus power rail, current, and differential probes
* VNA measurements to 8.5 GHz (PicoVNA 106 / 108)
* BERT BER/eye pattern/bathtub curve measurements to 28 Gbps (MultiLane ML4039-BTP)
* Vector signal generation to 6 GHz (Siglent SSG5060X-V)
* Fine pitch soldering and PCB rework, BGA assembly, inner layer circuit edits, etc
* Low magnification stereo microscopy
* High magnification reflected light optical microscopy to ~300nm resolution, including large area automated step-and-repeat scanning and stitching of multi-gigapixel datasets
* Coming soon: Embedding and cross section polishing for failure analysis etc
Pass the SALT Conference
passthesaltcon@infosec.exchangeCALL FOR PAPERS PERIODIC REMINDER
You have an offensive, defensive, audit research or dev mixing Security and FLOSS or open protocol/format?
Go ahead and submit your proposal!
👉 https://cfp.pass-the-salt.org/pts2025/cfp
A question, doubt? Our support team is listening to you: speaker-support@pass-the-salt.org
📅 The deadline is March, 30 2025!
D-40
Boost REALLY appreciated 🙏
Jerry 🦙💝🦙
jerry@infosec.exchangeReminder for those using the iOS Patreon app to support their creators: Apple is now taking a 30% cut for new donations through the app, plus whatever Patreon takes. Consider alternate donation methods (including direct to the Patreon website rather than the Apple mobile app).
I’ve found, btw, that ko-fi has the best deal for creators - for a $72 annual fee, they do not take any cut of donations.
Open Source Security mailing list
oss_security@bird.makeuplibxml2 vulnerabilities https://www.openwall.com/lists/oss-security/2025/02/18/2
Fixed in 2.12.10, 2.13.6 and upcoming 2.14.0.
CVE-2024-56171: Use-after-free in xmlSchemaIDCFillNodeTables
CVE-2025-24928: Stack-buffer-overflow in xmlSnprintfElements
Null-deref in xmlPatMatch
JosephMenn
JosephMenn@infosec.exchangeBreaking: Apple pulls end-to-end encrypted storage option from UK after secret order for a back door. https://www.washingtonpost.com/technology/2025/02/21/apple-yanks-encrypted-storage-uk-instead-allowing-backdoor-access/
Michał Kowalczyk
redford@infosec.exchange@Toasterson Seems someone has never seen German C-PASCAL?
So, the story goes back to @q3k and my old reverse engineering project, where we created a keygen for Toshiba Portégé BIOS password backdoor [1]. At one point, q3k was tasked with dumping the Embedded Controller firmware, but he fucked up and mistakenly desoldered a wrong chip, which we then started analyzing thinking it was the EC. It was TLCS-870/C1 (??) and we weren't able to find a disassembler for it, but... there was an open-source assembler! [2]
Written in German C-PASCAL 😬
All thanks to a totally normal #include "pascstyle.h" at the beginning.
[1] https://youtu.be/JyuVFa2X7AU
[2] http://john.ccac.rwth-aachen.de:8000/as/
OSNews
osnews@mstdn.socialMicrosoft is paywalling features in Notepad and Paint
There’s some bad news for Windows users who want to use all of the built-in features of the operating system and its integrated apps. Going forward, Microsoft is restricting features in two iconic apps, which you’ll need to unlock with a paid subscription.
The two apps in question? Notepad and Paint. [...]
Windows Insiders
https://www.osnews.com/story/141773/microsoft-is-paywalling-features-in-notepad-and-paint/