Posts
3368Following
712Followers
1580Andrew 🌻 Brandt 🐇
threatresearch@infosec.exchangeThis is *the most malicious, brutal* malicious compliance I've seen in quite some time, possibly ever, and I am HERE FOR IT. Thank you, @jwz
buherator
buheratorDirk-jan
_dirkjan@bird.makeupNormally you can't auth to Entra ID connected webapps with bearer tokens. But if Teams can open SharePoint/OneDrive with an access token, I guess so can we. roadtx now supports opening SharePoint with access tokens in the embedded browser 😀
Jeff Atwood
codinghorror@infosec.exchangeSo, coup by the evil venture capitalists. I kindly suggest the good venture capitalists should proceed to stand up and actively fight this, before everything goes full Palpatine.
buherator
buheratorAlex Plaskett
alexjplaskett@bird.makeupInside imessage-exporter: Reverse Engineering Apple's typedstream Format by @rxcs
https://chrissardegna.com/blog/reverse-engineering-apples-typedstream-format/
/r/netsec
_r_netsec@infosec.exchangeEveryday Ghidra: How Platform Choice Influences Ghidra’s Binary Analysis https://medium.com/@clearbluejar/everyday-ghidra-how-platform-choice-influences-ghidras-binary-analysis-76c40db0e407
Neiman
neiman@social.hastily.ccI should just share all of Trails of Bits new posts, right? It's the best cryptography blog I know of.
This time they're discussing key derivatives (as in, how to get a private key? How to generate more keys out of it?).
https://blog.trailofbits.com/2025/01/28/best-practices-for-key-derivation/
Fellows
fellows@cyberplace.socialIf you haven’t noticed malicious emails abusing Microsoft Library Description files (.library-ms), watch out and block them.
From Microsoft “Library description files are XML files that define libraries. Libraries aggregate items from local and remote storage locations into a single view in Windows Explorer.”
Threat actors, in an effort to evade detection, use them as a way of connecting their target to a remote share directly via File Explorer.
https://learn.microsoft.com/en-us/windows/win32/shell/library-schema-entry
buherator
buheratorhttps://infosec.rm-it.de/2025/02/17/microsoft-edge-developer-vm-remote-code-execution/
This is fun: take DNS name, pwn researchers :)
Hex-Rays SA
HexRaysSA@infosec.exchangeWe are thrilled to announce the winners of the 2024 Hex-Rays Plugin Contest!
🥇1st Place: hrtng
🥈2nd Place: aiDAPal
🥉3rd Place: idalib Rust bindings
Check out our reviews of the winners and other notable submissions here: https://hex-rays.com/blog/2024-plugin-contest-winners
Huge thank you to all participants for their innovative contributions. Your creativity continues to enhance the IDA community.
Satoshi
satoshi_tanda@infosec.exchangeAdded AMD support to hvext, the windbg extension for reversing Hyper-V!
https://github.com/tandasat/hvext
You can check what SVM features are enabled, which MSRs and IO ports are accessible, and how nested page table looks like, for NT, SK and regular VMs.
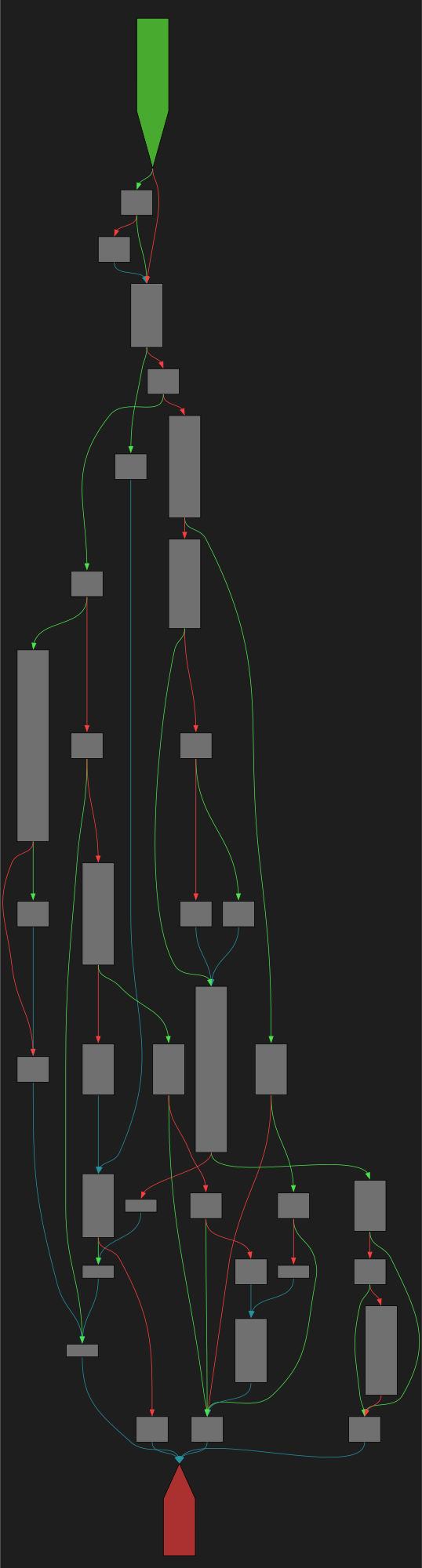
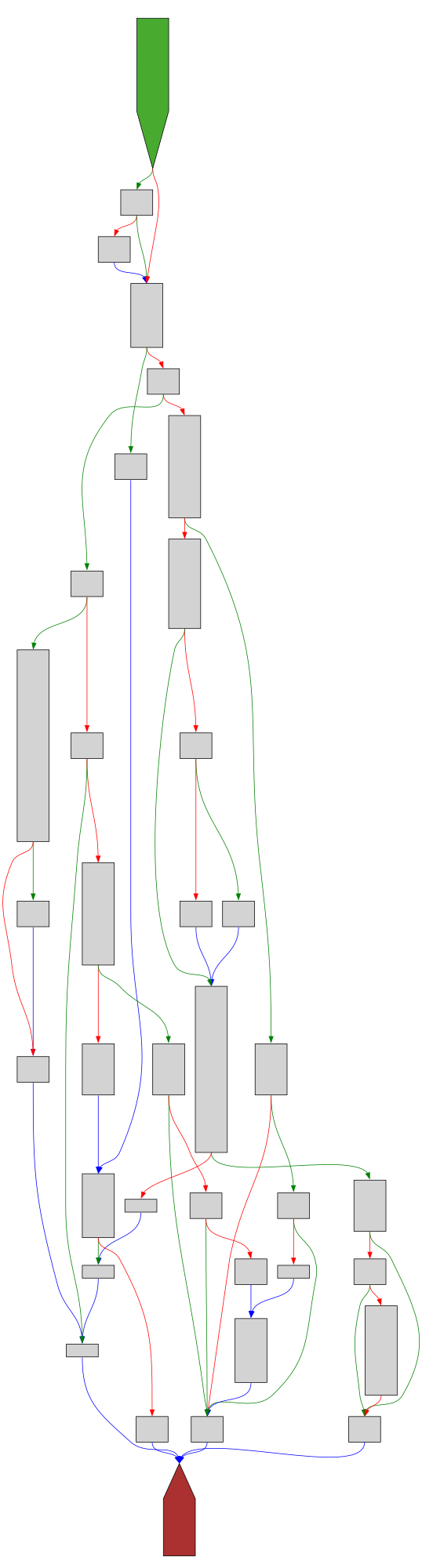
CFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a190110
Read
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a190110.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a190110.json&colors=light