Posts
3373Following
712Followers
1579quarkslab
quarkslab@infosec.exchangeUnrestrict the restricted mode for USB on iPhone. A first analysis @citizenlab #CVE-2025-24200 👉 https://blog.quarkslab.com/first-analysis-of-apples-usb-restricted-mode-bypass-cve-2025-24200.html
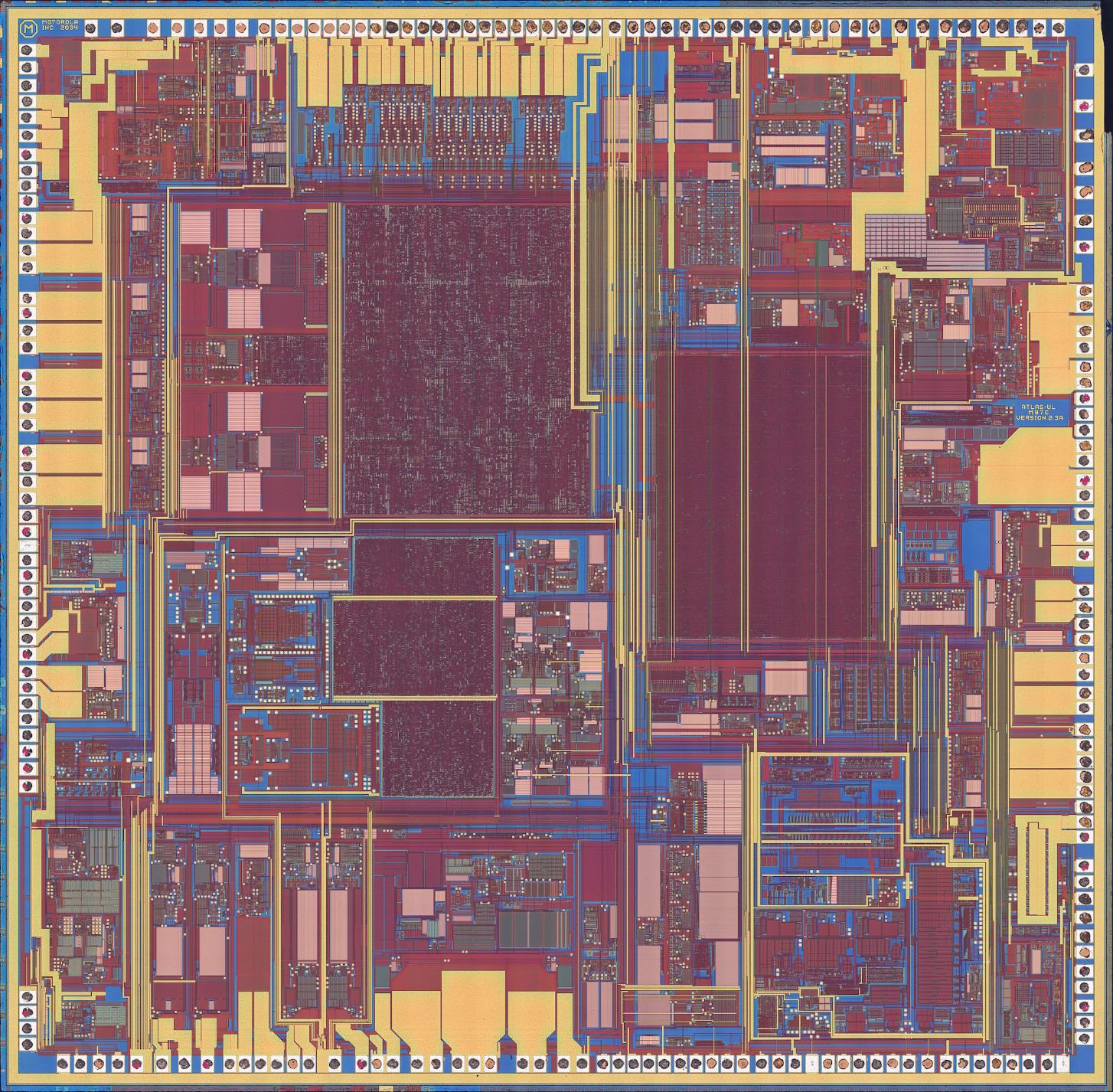
Happy #nakeddiefriday folks!
Today's specimen is p/n SC13890P23A by Motorola/Freescale. This came from an embedded cellular modem I tore out of [redacted]. The die is marked ATLAS-UL.
It is the most colourful die I have ever imaged. 
SiPron page: https://siliconpr0n.org/archive/doku.php?id=infosecdj:motorola:sc13890p23a
Preparing a talk on #programming an #AnalogComputer - using the wonderful #THAT from anabrid and my #Vectrex that has been modified to provide an additional #oscilloscope mode.
Frederik Braun �
freddy@security.plumbingReally cool blog post about permissions in browsers and how they work. https://albertofdr.github.io/web-security-class/browser/browser.permissions
buherator
buheratorhttps://blog.adafruit.com/2025/02/13/bent-broken-2025-worldwide-virtual-circuit-bending-festival/
Thibaultmol 🌈
thibaultmol@en.osm.townToday's @kagihq changelog is honestly kind of a massive deal for privacy stuff:
- Human readable privacy policy page
- Privacy pass (an open source, cryptographic verifiable way of doing searches through Kagi without them being able to see who you are)
- Official tor service
buherator
buheratorhttps://code-white.com/public-vulnerability-list/#unauthenticated-remote-code-execution-via-known-view-state-secret-in-fieldpie
This may be one of those leaked secrets MS warned about? No details unfortunately...
buherator
buheratorhttps://h0mbre.github.io/Patch_Gapping_Google_COS/
buherator
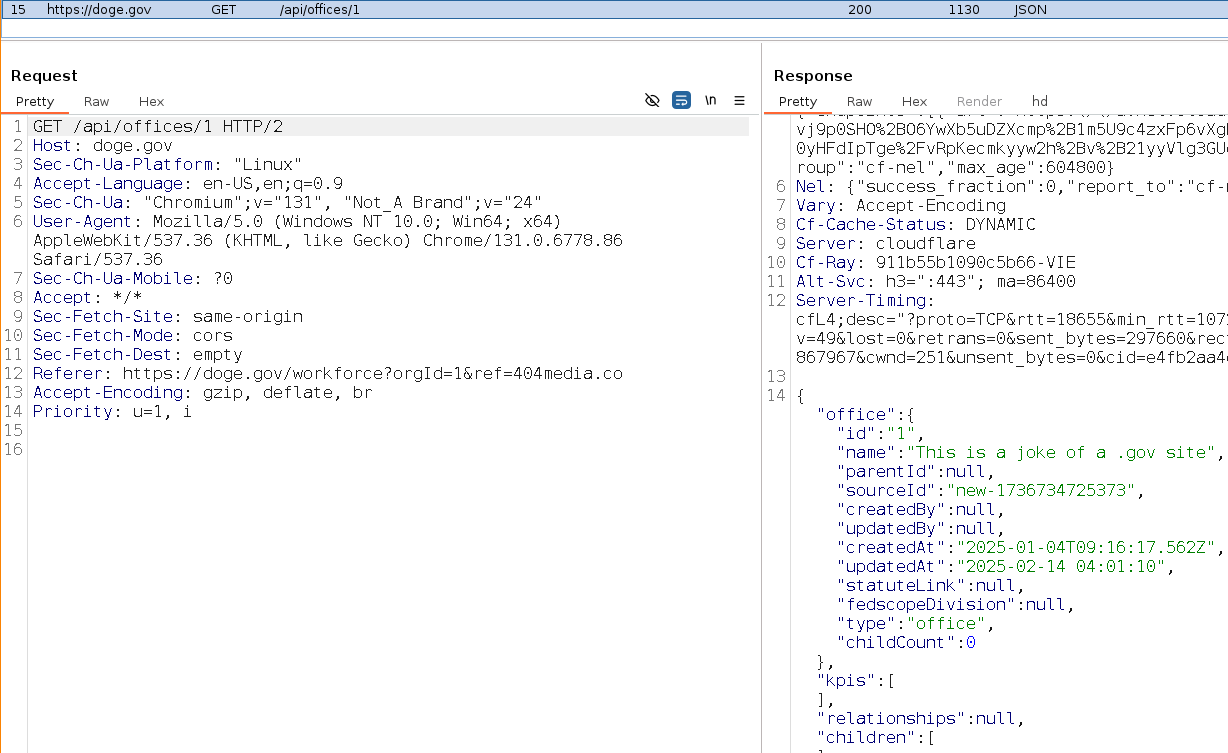
buherator404 Media
404mediaco@mastodon.socialScoop: The databases powering doge. gov are insecure, and people outside the government have already pushed their own updates to the site to prove it:
https://www.404media.co/anyone-can-push-updates-to-the-doge-gov-website-2/
buherator
buheratorBrad Spengler
spendergrsec@bird.makeupNot sure why Google's kCTF isn't more widely known (other than by all the researchers making money from it). 44 unique successful exploits in a year against Linux kernels even running Google's out-of-tree "hardening" is a big story I'd say...
GoodNewsGreyShoes🔞
GoodNewsGreyShoes@mastodon.art@aparrish Every single time I hear the sentiment "like it or not, ______ is here to stay", I like to take a moment to reflect on the overwhelming majority of "things we were told would be permanent" that now, *shockingly*, no longer exist.😮🫢🤗🙄
buherator
buheratorBut again: this would be in all likelihood a **BAD SOLUTION** because authn decision still would be made by a component that has incomplete information about exactly what should be authn'd and how! If you think about previous examples the rev proxy would generate a valid JWT just as it generated a True value because it interpreted the URL's differently than the app server.
Anderson Nascimento
andersonc0d3@infosec.exchangeCVE-2025-26519: musl libc: input-controlled out-of-bounds write primitive in iconv()