Posts
2528Following
649Followers
1466buherator
buheratorhttps://h0mbre.github.io/Patch_Gapping_Google_COS/
buherator
buherator404 Media
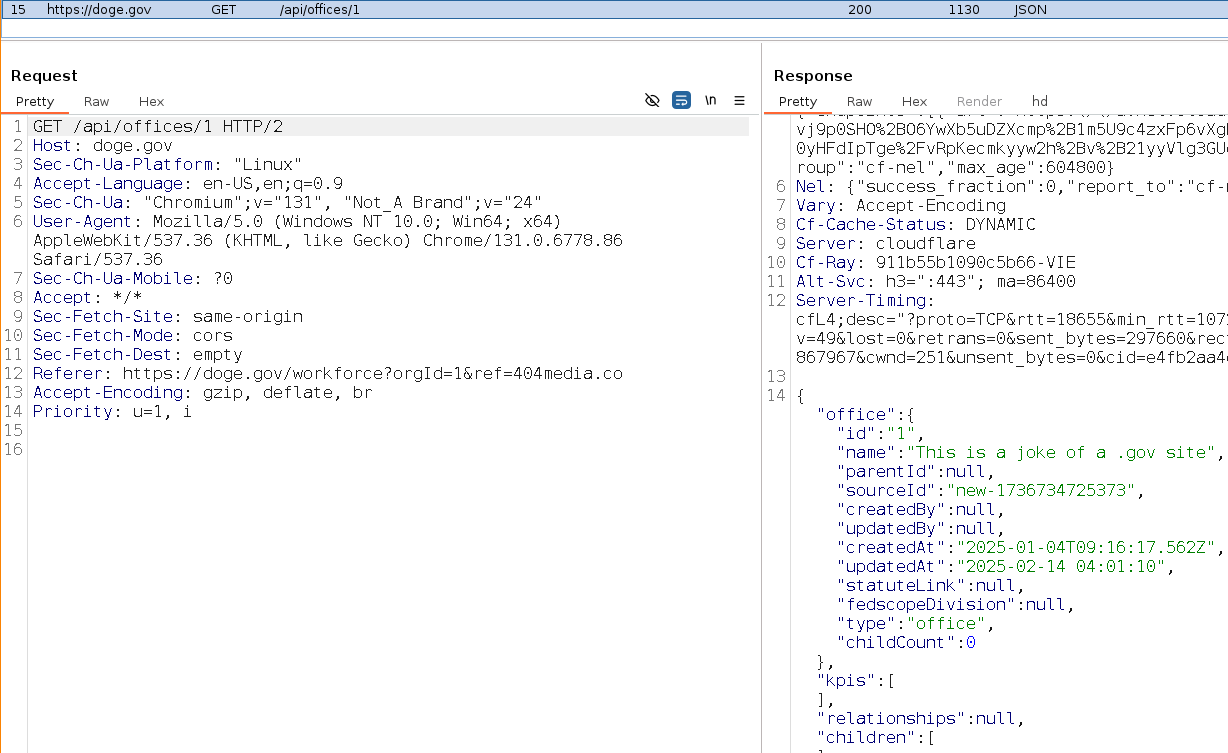
404mediaco@mastodon.socialScoop: The databases powering doge. gov are insecure, and people outside the government have already pushed their own updates to the site to prove it:
https://www.404media.co/anyone-can-push-updates-to-the-doge-gov-website-2/
buherator
buheratorBrad Spengler
spendergrsec@bird.makeupNot sure why Google's kCTF isn't more widely known (other than by all the researchers making money from it). 44 unique successful exploits in a year against Linux kernels even running Google's out-of-tree "hardening" is a big story I'd say...
GoodNewsGreyShoes🔞
GoodNewsGreyShoes@mastodon.art@aparrish Every single time I hear the sentiment "like it or not, ______ is here to stay", I like to take a moment to reflect on the overwhelming majority of "things we were told would be permanent" that now, *shockingly*, no longer exist.😮🫢🤗🙄
buherator
buheratorBut again: this would be in all likelihood a **BAD SOLUTION** because authn decision still would be made by a component that has incomplete information about exactly what should be authn'd and how! If you think about previous examples the rev proxy would generate a valid JWT just as it generated a True value because it interpreted the URL's differently than the app server.
Anderson Nascimento
andersonc0d3@infosec.exchangeCVE-2025-26519: musl libc: input-controlled out-of-bounds write primitive in iconv()
Paragon Initiative Enterprises
paragon@phpc.socialAccelerating The Adoption of Post-Quantum Cryptography with PHP
https://paragonie.com/blog/2025/02/accelerating-adoption-post-quantum-cryptography
#PHP #crypto #cryptography #HPKE #KEMs #MLKEM #MLDSA #SLHDSA #postquantum #programming #webdev #MLS #rfc9180 #rfc9420
Kim Zetter
kimzetter@infosec.exchangeNew court documents shed light on what a 25-year-old DOGE worker named Marko Elez did inside Treasury payment systems, including which systems he accessed, security measures Treasury IT staff took to limit his access and activity, and whether he really did have the ability to change source code on production systems as previously reported. The new documents, signed affidavits filed in court by career executives at the Treasury department not political appointees, suggest that the situation inside the Treasury department is more nuanced than previously reported. Here's my story. If you find the piece valuable, please consider becoming a paid subscriber to my Zero Day publication, which is reader supported. https://www.zetter-zeroday.com/court-documents-shed-new-light-on-doge-access-and-activity-at-treasury-department/
Caitlin Condon
catc0n@infosec.exchangeCVE-2024-12356 was patched in December 2024, and the patch successfully neutralized what we believe to be the original exploit chain (including CVE-2025-1094). So neither CVE-2024-12356 nor CVE-2025-1094 was exploitable in BeyondTrust RS post-patch.
The BeyondTrust patch for CVE-2024-12356 did not address the root cause of CVE-2025-1094 in PostgreSQL psql, however — so CVE-2025-1094 remained a zero-day vulnerability until it was reported to the PostgreSQL dev group and remediated in today's release. https://www.postgresql.org/support/security/CVE-2025-1094/
Caitlin Condon
catc0n@infosec.exchangeNew #Rapid7 vuln disclosure c/o
@stephenfewer: CVE-2025-1094 is a SQL injection flaw in PostgreSQL's psql interactive tool that was discovered while analyzing BeyondTrust RS CVE-2024-12356. The bug is interesting — 🧵on its relation to BeyondTrust exploitation https://www.rapid7.com/blog/post/2025/02/13/cve-2025-1094-postgresql-psql-sql-injection-fixed/
buherator
buheratorrev.ng
revng@infosec.exchangeWe just opened our YouTube channel! 📹
First video is out: An introduction to LLVM IR 🐲
Check it out: https://www.youtube.com/watch?v=CDKuH7SIgdM
Let us know what you think 🙃
buherator
buheratorNonetheless, this is an illustrative example that unless we point to some robust solution ppl *will* come up with complex but insecure solutions (see also Schneier's Law).