Posts
3373Following
712Followers
1579buherator
buheratorhttps://talosintelligence.com/vulnerability_reports#disclosed
CVE-2024-0142, CVE-2024-0143, CVE-2024-0144, CVE-2024-0145
buherator
buheratorhttps://www.akamai.com/blog/security-research/2025-february-fortinet-critical-vulnerabilities
"We%27ll go through the processes of getting the firmware, decrypting, setting up a debugger, and finally looking for vulnerabilities." -> Mad respect!
Rust Weekly 🦀
rust_discussions@mastodon.socialA demonstration of writing a simple Windows driver in Rust
https://scorpiosoftware.net/2025/02/08/writing-a-simple-driver-in-rust/
Discussions: https://discu.eu/q/https://scorpiosoftware.net/2025/02/08/writing-a-simple-driver-in-rust/
quarkslab
quarkslab@infosec.exchangeGood tools are made of bugs: How to monitor your Steam Deck with one byte.
Finding and exploiting two vulnerabilities in AMD's UEFI firmware for fun and gaming.
A Christmas gift in February, brought to you by the incredible @pwissenlit 🫶
https://blog.quarkslab.com/being-overlord-on-the-steam-deck-with-1-byte.html
screaminggoat
screaminggoat@infosec.exchangeHappy #PatchTuesday from SolarWinds:
- Sensitive data disclosure vulnerability (CVE-2024-45718) 4.6 medium
- SolarWinds Platform Information Disclosure Vulnerability (CVE-2024-52611) 3.5 low
- SolarWinds Platform Server-Side Request Forgery Vulnerability (CVE-2024-52606) 3.5 low
No mention of exploitation.
screaminggoat
screaminggoat@infosec.exchangeElecticIQ: Sandworm APT Targets Ukrainian Users with Trojanized Microsoft KMS Activation Tools in Cyber Espionage Campaigns
EclecticIQ analysts assess with high confidence that Sandworm (APT44), a threat actor supporting Russia's Main Intelligence Directorate (GRU), is actively conducting a cyber espionage campaign against Ukrainian Windows users. Likely ongoing since late 2023, following Russia's invasion of Ukraine, Sandworm leverages pirated Microsoft Key Management Service (KMS) activators and fake Windows updates to deliver a new version of BACKORDER, a loader previously associated with the group. BACKORDER ultimately deploys Dark Crystal RAT (DcRAT), enabling attackers to exfiltrate sensitive data and conduct cyber espionage.
Multiple pieces of evidence strongly link this campaign to Sandworm, also tracked by CERT-UA as UAC-0145, based on recurring use of ProtonMail accounts in WHOIS records, overlapping infrastructure, and consistent Tactics, Techniques and Procedures (TTPs). Additionally, the reuse of BACKORDER, DcRAT, and TOR network mechanisms, along with debug symbols referencing a Russian-language build environment, further reinforce confidence in Sandworm's involvement. Yara and Sigma rules, and Indicators of Compromise are listed.
#russia #sandworm #apt44 #gru #threatintel #IOC #yara #sigma #malwareanalysis #infosec #cybersecurity #cti #cyberthreatintelligence
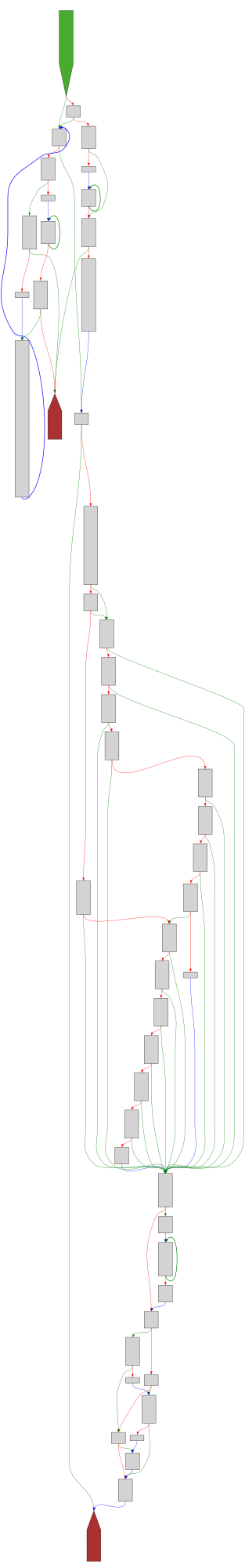
CFG Bot 🤖
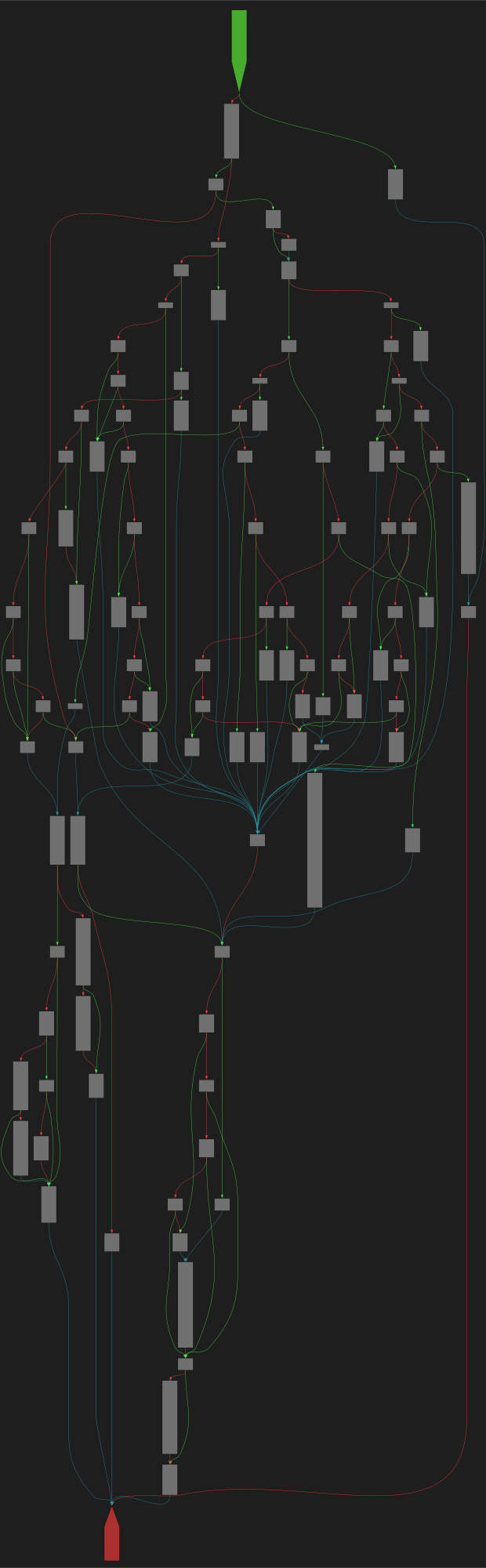
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a785720
getBasicDataType
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a785720.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a785720.json&colors=light
Mr. Bitterness
wdormann@infosec.exchangeApparently Google is just shitty.
No duress signal or anything here. Just trying to fit in by being shitty. 🤦♂️
buherator
buheratorMax-Planck-Gesellschaft
maxplanckgesellschaft@wisskomm.social‘We must...fiercely protect the progress women in science have made!’ 🔬On #womeninscienceday don't miss this insightful interview w/ Suropriya Saha, Max Planck Research Group Leader, on the legacy of #Physics Nobel laureate Maria Goeppert Mayer!🌟 ▶️ https://www.mpg.de/23712159/suropriya-saha-about-maria-goeppert-mayer #GirlsinStem
Squiblydoo
squiblydoo@infosec.exchangeCertCentral.org is live!
We track and report abused code-signing certs.
By submitting to the website, you contribute to the DB of >800 certs—a DB you can access and view.
Want to get more involved? Check out the Training and Research pages to learn more.
We can handle submitting your reports too. See the website for more details. :)
CFG Bot 🤖
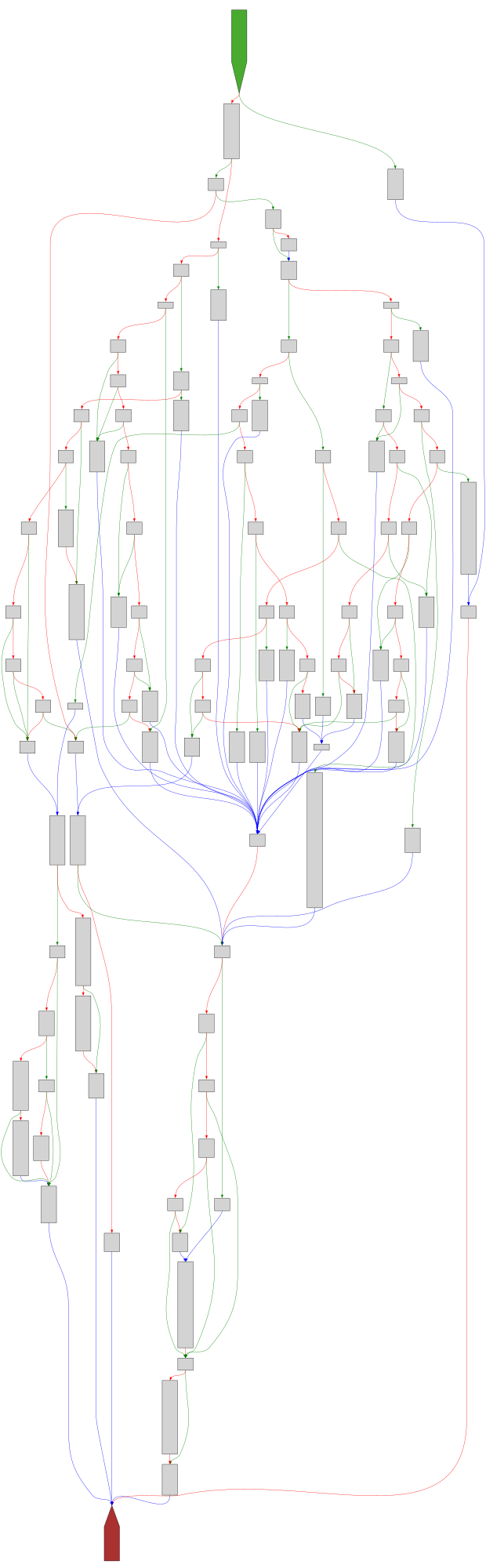
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 0060aec0
CRYPTO_ocb128_decrypt
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0060aec0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0060aec0.json&colors=light
Ivan Ožić Bebek
obivan@infosec.exchangeAnydesk LPE Vulnerability https://github.com/CICADA8-Research/Penetration/tree/main/POCs/CVE-2024-12754
buherator
buheratorbuherator
buheratorhttps://www.youtube.com/watch?v=SUUUZKYApoc (taxidermia #nsfw #gross)