Posts
2495Following
664Followers
1490buherator
buheratorhttps://www.zetter-zeroday.com/u-s-government-disclosed-39-zero-day-vulnerabilities-in-2023-per-first-ever-report/
The original "report" is here:
https://www.wyden.senate.gov/imo/media/doc/fy23_unclassified_vep_annual_reportpdf.pdf
buherator
buheratorWhat's New:
https://github.com/NationalSecurityAgency/ghidra/blob/Ghidra_11.3_build/Ghidra/Configurations/Public_Release/src/global/docs/WhatsNew.md
Change History:
https://github.com/NationalSecurityAgency/ghidra/blob/Ghidra_11.3_build/Ghidra/Configurations/Public_Release/src/global/docs/ChangeHistory.md
CFG Bot 🤖
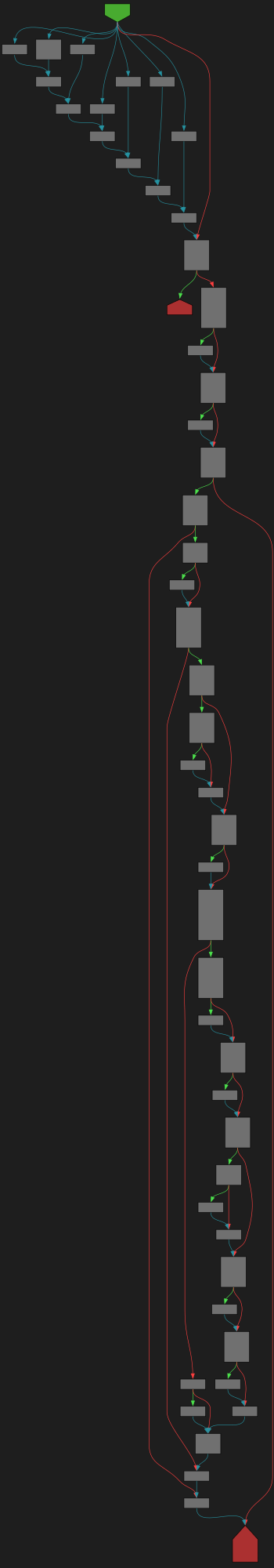
cfgbot@mastodon.socialProject: microsoft/TypeScript https://github.com/microsoft/TypeScript
File: src/services/classifier2020.ts:127 https://github.com/microsoft/TypeScript/blob/cbac1ddfc73ca3b9d8741c1b51b74663a0f24695/src/services/classifier2020.ts#L127
function visit(node: Node)
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FTypeScript%2Fblob%2Fcbac1ddfc73ca3b9d8741c1b51b74663a0f24695%2Fsrc%2Fservices%2Fclassifier2020.ts%23L127&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FTypeScript%2Fblob%2Fcbac1ddfc73ca3b9d8741c1b51b74663a0f24695%2Fsrc%2Fservices%2Fclassifier2020.ts%23L127&colors=light
CFG Bot 🤖
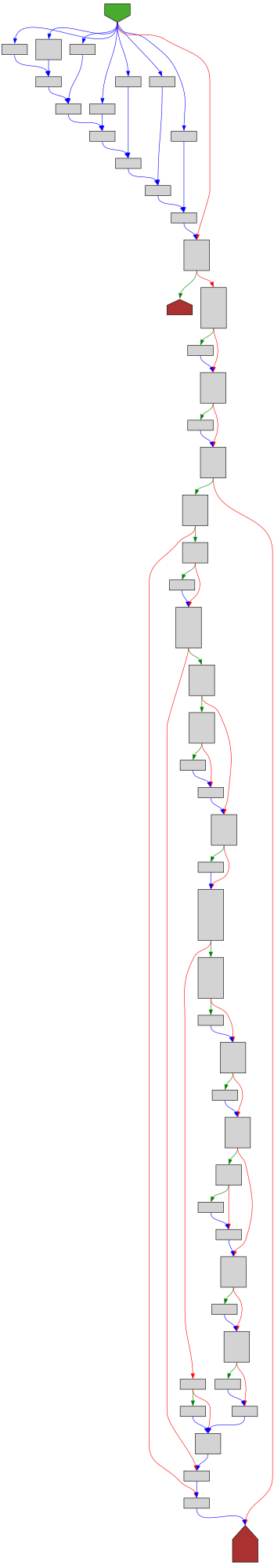
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
File: src/cmd/internal/obj/ppc64/asm9.go:5134 https://github.com/golang/go/blob/refs/tags/go1.23.4/src/cmd/internal/obj/ppc64/asm9.go#L5134
func (c *ctxt9) oploadx(a obj.As) uint32
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Finternal%2Fobj%2Fppc64%2Fasm9.go%23L5134&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Finternal%2Fobj%2Fppc64%2Fasm9.go%23L5134&colors=light
Esther #antifa
src_esther@mastodon.onlineA message to my fellow Europeans.
Don't be paralysed by overseas fascism.
It is time for Europe and its citizens to focus less on the USA.
Stop obsessively following the news in a country where you cannot change anything.
Focus your attention on where you can make an impact.
All attention is needed here to fight growing fascism.
Jeff Atwood
codinghorror@infosec.exchangeDiscover the little computer people https://en.wikipedia.org/wiki/Little_Computer_People
Advanced Fuzzing League
aflplusplus@infosec.exchangeWe've just released #LibAFL 0.15.0 - A big step toward 1.0 stable!
Featuring
- Mutators for Numeric Types
- Bloomfilter-based deduplication for to-be-executed inputs
- Nyx hypercall API support for LibAFL QEMU and new utilities for binary-only fuzzing
- ...https://github.com/AFLplusplus/LibAFL/releases/tag/0.15.0
K. Reid Wightman  🌻
🌻 

reverseics@infosec.exchange
We take your vulnerability report very seriously. Internally, we will pass the issue around between developers similar to the childhood game 'hot potato'. After a year of this, we will play a round of musical chairs where the last developer left standing will be assigned the ticket, and then they will also be let go from the company.
We will proceed to a hot potato round when you make your next inquiry. Due to our email retention policy, you will need to re-submit your original report and proof of concept exploit code at that time.
^ honest vulnerability coordination policies
buherator
buheratorCalDAV is a still a dumpster of dumpster fires.
rrmutt
rrmutt@mastodon.socialTimeline cleanse: pleased to report that Greg is still blowing stuff up with electricity https://www.youtube.com/watch?v=Cse3pUxvecY
internetarchive
internetarchive@mastodon.archive.org🚧 What do dancing babies, "under construction" signs, and bubble-gum-blowing Furbys tell us about digital preservation? In the latest essay for the Internet Archive's Vanishing Culture series, writer JD Shadel explores the rise, fall, and cultural legacy of early Internet GIFs—and why they matter today.
🔗 https://blog.archive.org/2025/02/05/vanishing-culture-what-early-internet-era-gifs-show-us-about-preserving-digital-culture/
🕳️ #VanishingCulture
Stefan Bohacek
stefan@stefanbohacek.online"Thinkers like Jean-Paul Sartre and Hannah Arendt warned us that the point of this deluge is not to persuade, but to overwhelm and paralyze our capacity to act. More recently, researchers have found that the viral outrage disseminated on social media in response to these ridiculous claims actually reduces the effectiveness of collective action.
The result is a media environment that keeps us in a state of debilitating fear and anger, endlessly reacting to our oppressors instead of organizing against them."
https://www.404media.co/you-cant-post-your-way-out-of-fascism/
buherator
buheratorNeodyme
neodyme@infosec.exchange🪝Introducing HyperHook! 🪝
A harnessing framework for snapshot-based #fuzzing using Nyx. ⚒️
HyperHook simplifies guest-to-host communication & automates repetitive tasks, making snapshot-fuzzing easier & more efficient!
🔗 Read more: https://neodyme.io/en/blog/hyperhook/
screaminggoat
screaminggoat@infosec.exchangeCisco security advisories (PatchTuesday-ishing @shellsharks):
- Cisco Secure Email and Web Manager, Secure Email Gateway, and Secure Web Appliance Vulnerabilities
- CVE-2024-20184 (6.5 medium) Cisco Secure Email Gateway and Cisco Secure Web Appliance Command Injection Vulnerability
- CVE-2024-20185 (3.1 low) Cisco Secure Email and Web Manager, Cisco Secure Email Gateway, and Cisco Secure Web Appliance Privilege Escalation Vulnerability
- Cisco Secure Web Appliance Range Request Bypass Vulnerability CVE-2025-20183 (5.8 medium)
- Cisco IOS, IOS XE, and IOS XR Software SNMP Denial of Service Vulnerabilities
- CVE-2025-20169, CVE-2025-20170, CVE-2025-20171, CVE-2025-20173, CVE-2025-20174, CVE-2025-20175, CVE-2025-20176 (7.7 high) Cisco IOS and IOS XE Software SNMP Software Denial of Service Vulnerabilities
- CVE-2025-20172 Cisco IOS and IOS XE (7.7 high), and IOS XR (4.3 medium) Software SNMP Denial of Service Vulnerabilities
- Cisco Identity Services Engine Stored Cross-Site Scripting Vulnerabilities CVE-2025-20204 and CVE-2025-20205 (4.8 medium)
- Cisco Identity Services Engine Insecure Java Deserialization and Authorization Bypass Vulnerabilities
- CVE-2025-20124 (9.9 critical) Cisco ISE Insecure Java Deserialization Vulnerability
- CVE-2025-20125 (9.1 critical) Cisco ISE Authorization Bypass Vulnerability
- Cisco Expressway Series Cross-Site Scripting Vulnerability CVE-2025-20179 (6.1 medium)
- Cisco Secure Email and Web Manager and Secure Email Gateway Cross-Site Scripting Vulnerability CVE-2025-20180 (4.8 medium)
- Cisco Secure Email and Web Manager, Secure Email Gateway, and Secure Web Appliance SNMP Polling Information Disclosure Vulnerability CVE-2025-20207 (4.3 medium)
"The Cisco PSIRT is not aware of any public announcements or malicious use of the vulnerability that is described in this advisory."
In response to a popular demand, here is DOOM running on Apple Lightning to HDMI dongle
screaminggoat
screaminggoat@infosec.exchangeVeeam: CVE-2025-23114
CVE-2025-23114 (9.0 critical) A vulnerability within the Veeam Updater component that allows an attacker to utilize a Man-in-the-Middle attack to execute arbitrary code on the affected appliance server with root-level permissions. This CVE impacts multiple versions of Veeam Backup. No mention of exploitation. h/t: @cR0w
#veeam #cve #CVE_2025_23114 #infosec #vulnerability #cybersecurity