Posts
3142Following
708Followers
1555offensivecon
offensive_con@bird.makeupTicket shop is live.
https://www.offensivecon.org/register.html
Jonathan Metzman
metzman@infosec.exchangeThe OSS-Fuzz team is hiring a PhD intern for this summer. Come join us and build something interesting that will have immediate impact on 1000+ open source projects. https://www.google.com/about/careers/applications/jobs/results/92969243305222854-research-intern-phd-summer-2025
tante
tante@tldr.nettime.orgCool project: "Nepenthes" is a tarpit to catch (AI) web crawlers.
"It works by generating an endless sequences of pages, each of which with dozens of links, that simply go back into a the tarpit. Pages are randomly generated, but in a deterministic way, causing them to appear to be flat files that never change. Intentional delay is added to prevent crawlers from bogging down your server, in addition to wasting their time. Lastly, optional Markov-babble can be added to the pages, to give the crawlers something to scrape up and train their LLMs on, hopefully accelerating model collapse."
Trammell Hudson
th@v.stThe original artist describes their Fortran code that rendered the Nostromo's vector landing display in "Alien": https://archive.org/details/creativecomputing-1981-06/page/n51/mode/2up?ui=embed&view=theater
buherator
buheratorhttps://bsky.app/profile/rgblights.bsky.social/post/3lfsapwhlec2c
nasko
nasko@infosec.exchangeWe are looking for an Android security expert to join our team and work on securing Chrome on Andoird. Job posting is available at https://google.com/about/careers/applications/jobs/results/104891950447895238, but also feel free to reach out to me directly.
Alex Gough
quidity@infosec.exchangeMy team in Chrome Platform Security is hiring for a senior Android security expert - if you're into syscalls, binder, processes and other low level stuff you'd be perfect - I do this but for Windows and didn't know Chrome or much C++ when I started.
The ad is generic but feel free to ask questions - https://www.google.com/about/careers/applications/jobs/results/104891950447895238 - you'll be a part of a wider security team that works on lots of cool stuff and protects billions of people - https://www.chromium.org/Home/chromium-security/quarterly-updates/
buherator
buheratorFilled with hex strings
These are a few of my
Favorite things🤗
Neodyme
neodyme@infosec.exchangeFollowing our #38c3 talk about exploiting security software for privilege escalation, we're excited to kick off a new blog series! 🎊
Check out our first blog post on our journey to 💥 exploit five reputable security products to gain privileges via COM hijacking: https://neodyme.io/blog/com_hijacking_1/
CFG Bot 🤖
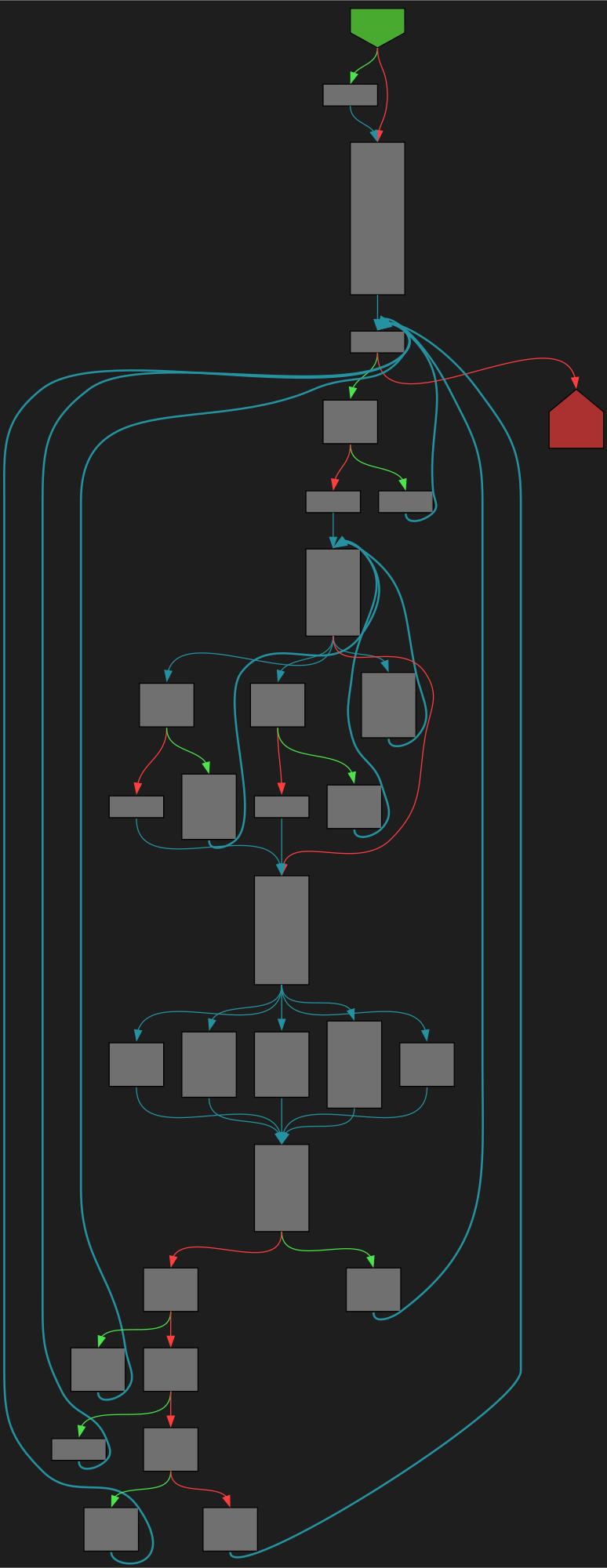
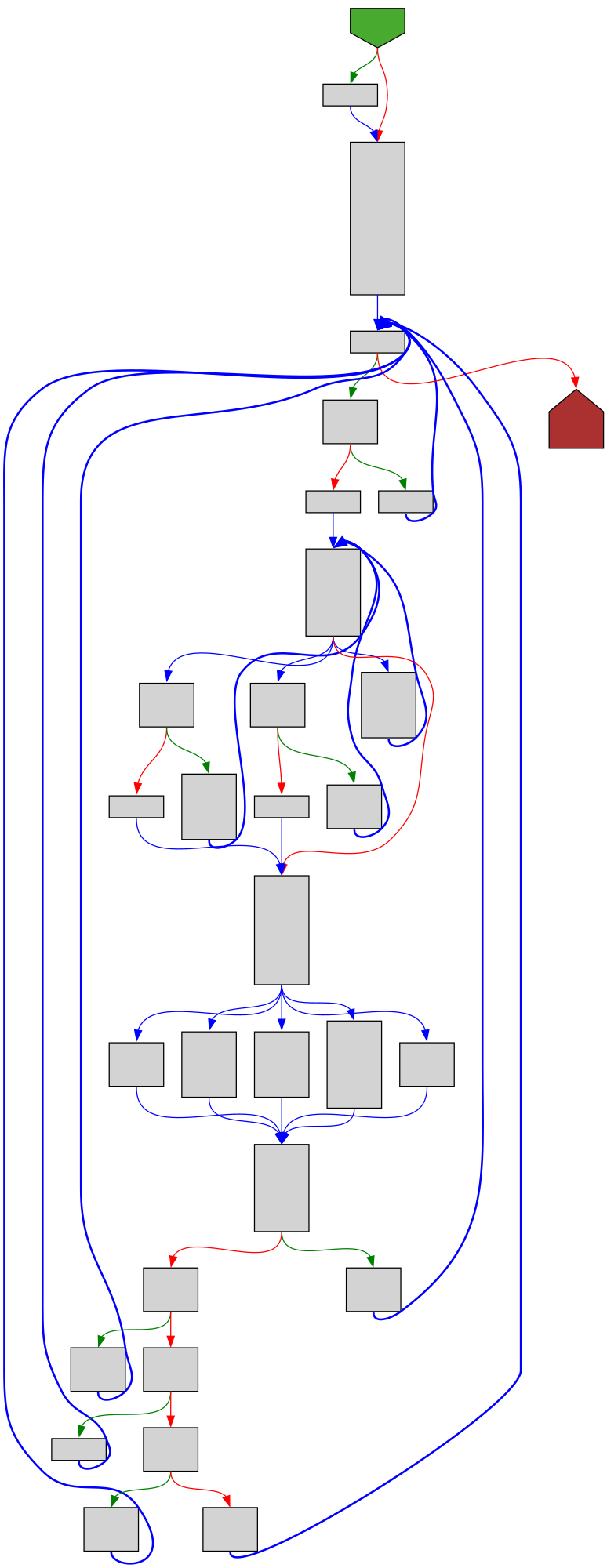
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
File: src/cmd/compile/internal/walk/assign.go:281 https://github.com/golang/go/blob/refs/tags/go1.23.4/src/cmd/compile/internal/walk/assign.go#L281
func ascompatee(op ir.Op, nl, nr []ir.Node) []ir.Node
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Fcompile%2Finternal%2Fwalk%2Fassign.go%23L281&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Fcompile%2Finternal%2Fwalk%2Fassign.go%23L281&colors=light
buherator
buheratornSinus-R (@nsr@infosec.exchange)
nsinusr@bird.makeupResults of the RP2350 Hacking Challenge are now public - I'm happy that my entry qualified as one of the winning breaks!
Also huge shout out to the other winners: @aedancullen, Kévin Courdesses, @ioactive & @hextreeio - awesome work!
Thanks for the challenge @raspberry_pi!
Alex Plaskett
alexjplaskett@bird.makeupHarnessing Libraries for Effective Fuzzing by @2ourc3
https://github.com/20urc3/Publications/blob/main/Articles/LIB_HARNESS_GUIDE/README.md
Alex Plaskett
alexjplaskett@bird.makeupToo Subtle to Notice: Investigating Executable Stack Issues in Linux Systems