Posts
2586Following
623Followers
13800patch
0patch@infosec.exchangeMicropatches Released for Windows "LDAPNightmare" Denial of Service Vulnerability (CVE-2024-49113)
https://blog.0patch.com/2025/01/micropatches-released-for-windows.html
0patch
0patch@infosec.exchangeMicropatches were issued for fully updated:
- Windows 11 v21H2
- Windows 10 v21H2, v21H1, v20H2, v2004, v1909, v1809, v1803
- Windows 7 - without ESU, or with ESU 1-3
- Windows Server 2012, Server 2012 R2 - without ESU
- Windows Server 2008 R2 - without ESU, or with ESU 1-4
We would like to thank Or Yair (@oryair1999) and Shahak Morag of @safebreach for sharing their analysis and proof-of-concept, which made it possible for us to create a micropatch for this issue. We'd also like to thank the original finder Yuki Chen (@guhe120).
daniel:// stenberg://
bagder@mastodon.socialTurns out snprintf() in old Windows C runtimes is documented to have the buffer overflow that no other implementations do. 🤔
/r/netsec
_r_netsec@infosec.exchangeThreat actors exploit a probable 0-day in exposed management consoles of Fortinet FortiGate firewalls https://www.orangecyberdefense.com/global/blog/cert-news/0-day-in-exposed-management-consoles-of-fortinet-fortigate-firewalls
Kat Marchán 🐈
zkat@toot.catTIL \ exists in ASCII literally so that ALGOL could write its Boolean operators in ASCII
Talos Vulnerability Reports
talosvulnsOFFIS DCMTK nowindow improper array index validation vulnerability
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2122
CVE-2024-47796
Talos Vulnerability Reports
talosvulnsOFFIS DCMTK determineMinMax improper array index validation vulnerability
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2121
CVE-2024-52333
/r/netsec
_r_netsec@infosec.exchangeExploitation Walkthrough and Techniques - Ivanti Connect Secure RCE (CVE-2025-0282) - watchTowr Labs https://labs.watchtowr.com/exploitation-walkthrough-and-techniques-ivanti-connect-secure-rce-cve-2025-0282/
buherator
buheratorhttps://www.hoyahaxa.com/2025/01/an-ssrf-to-lfi-payload-for-pdf.html
Joxean Koret (@matalaz)
joxean@mastodon.socialDoes anybody know how to prevent #clang from issuing calls to libc functions like `memset` in this case when compiling C programs? I have tried I don't know how many command line arguments to try to disable it but none worked at all.
Here you have an example program in #godbolt: https://godbolt.org/z/jheYoPWzj
These are the command line arguments I've tried to disable it:
-ffreestanding -disable-simplify-libcalls -fno-builtin -nostdinc -nostdlib -fno-builtin-memset -nostdlib++ -nostdinc++
Any idea?
decryption
decryption@aus.socialmight have to give up the apple watch so I can wear this replicate of the apollo guidance computer instead
https://gizmodo.com/apollo-landing-keypad-shrunken-into-worlds-coolest-calculator-watch-2000541103
Tamir Bahar
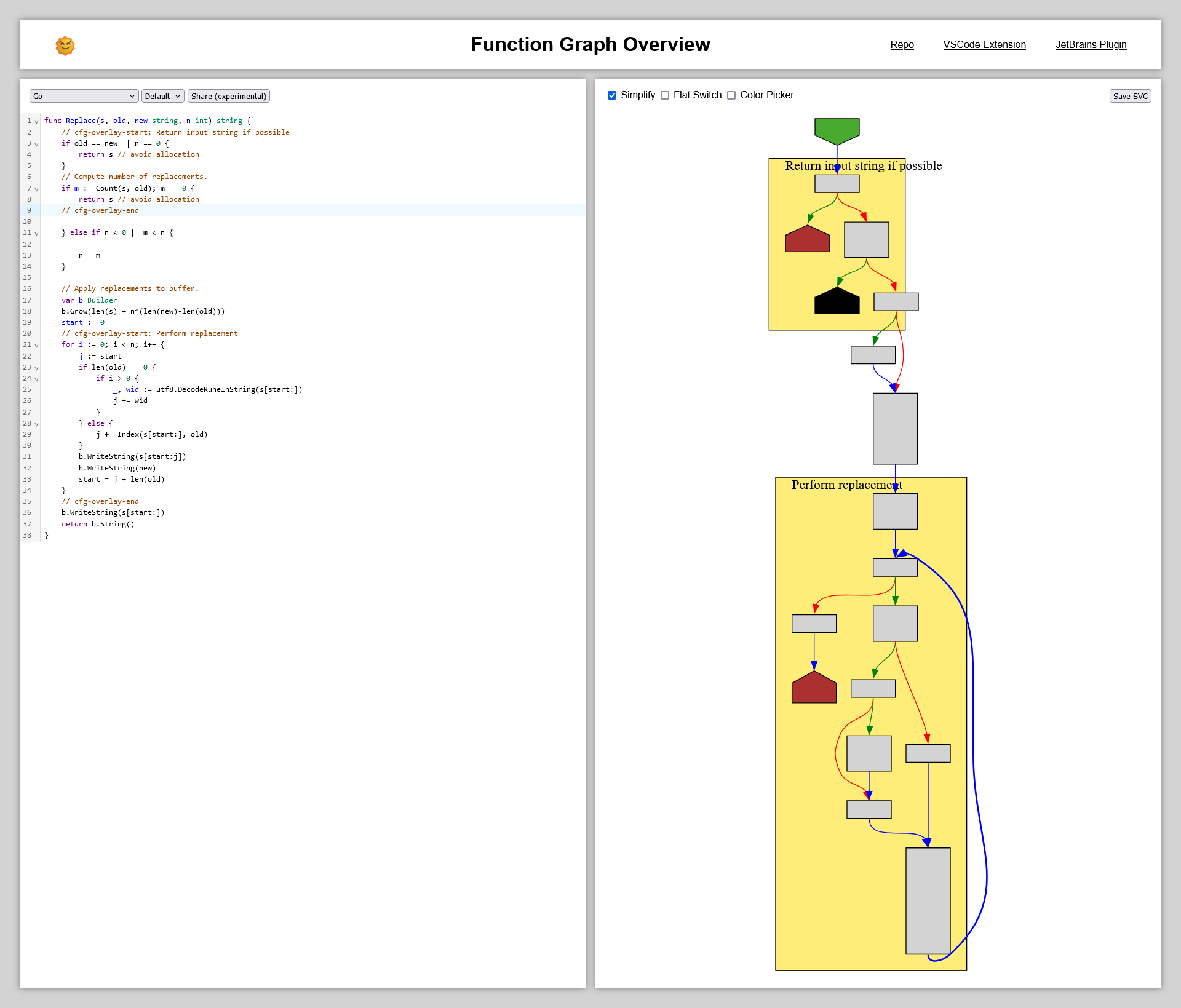
tmr232@mastodon.socialAdded the overlay-note-region-name-pending feature to the demo behind a feature-flag.
You can play with them at https://tmr232.github.io/function-graph-overview/?showRegions
Use `cfg-overlay-start: message` and `cfg-overlay-end` comments to denote the start and end of a region.
Danny Palmer
dannyjpalmer@infosec.exchangeIn one of the most "on brand" things I could write, here's an interview with Dan Keyworth, Director of Business Technology at McLaren Racing on how how the 2024 F1 World Constructor's Champions keep vast amounts of data and tech secured against cyber threats.
“We’ve got 200 people travelling around the world at any one time to 24 different races who, when they try to do something genuine, may look like they’re a threat to our organization,” says Keyworth.
“We’ve got to learn the different network behaviors they’re using when they’re on the road, for our business to recognize it as normal behavior when typically for other businesses, that’s abnormal behavior."
https://darktrace.com/the-inference/in-conversation-with-dan-keyworth-mclaren-racing
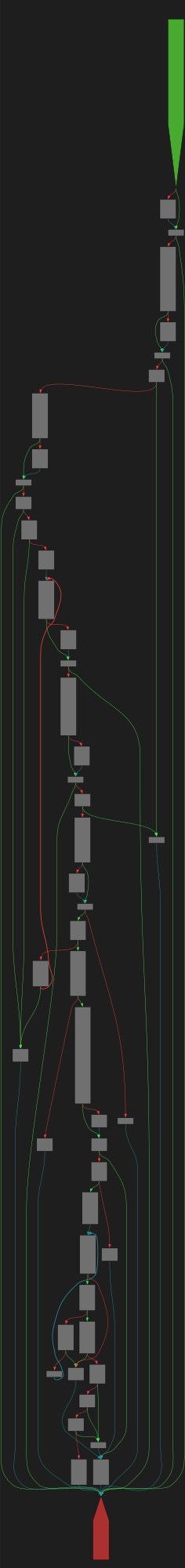
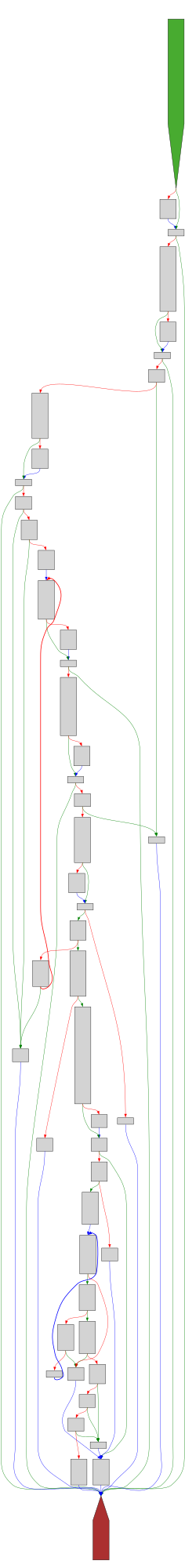
CFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75ab34cc8
GetVbaInfoAtom
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75ab34cc8.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75ab34cc8.json&colors=light
Maximilian Hils
max@fedi.hi.ls mitmproxy 11.1 is out! 🥳
mitmproxy 11.1 is out! 🥳
We now support *Local Capture Mode* on Windows, macOS, and - new - Linux! This allows users to intercept local applications even if they don't have proxy settings.
On Linux, this is done using eBPF and https://aya-rs.dev/, more details are at https://mitmproxy.org/posts/local-capture/linux/. Super proud of this team effort. 😃
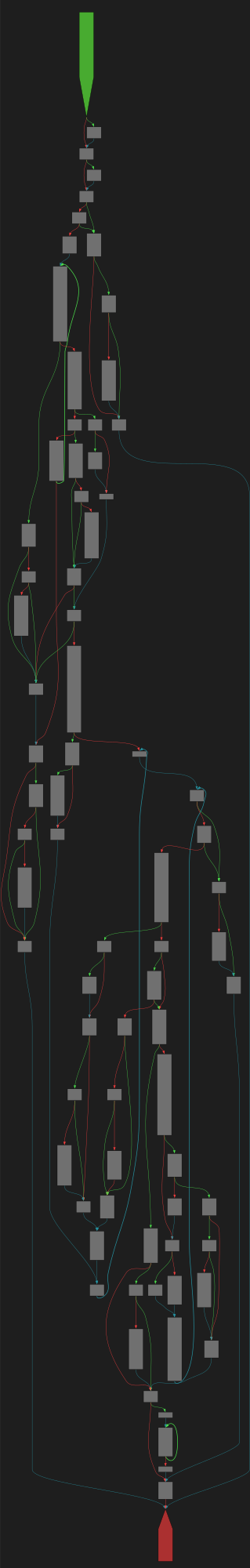
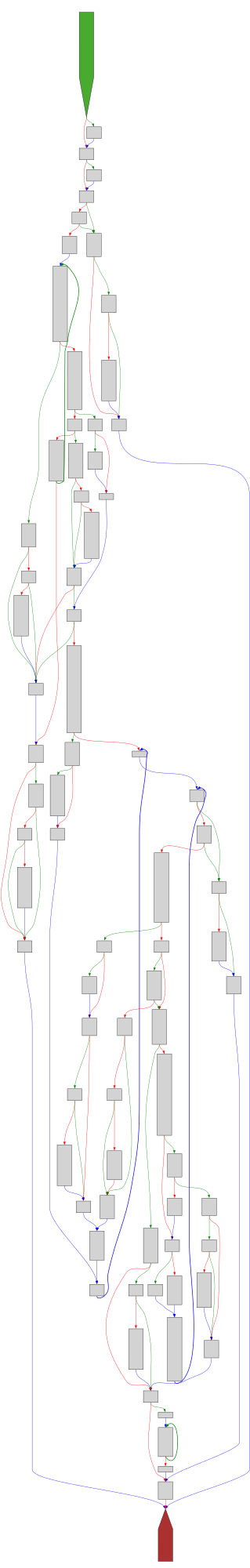
CFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a38b270
MemScanEnumProcesses
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a38b270.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a38b270.json&colors=light
buherator
buheratorhttps://seclists.org/dailydave/2025/q1/3
#fuzzing #llm