Posts
2987Following
697Followers
1545Ross Mounce
rmounce@mastodon.social"The economic value of the outgoing traffic... based on the cost-per-click estimated via the Google Ads platform showed that the owners of external websites linked from Wikipedia infoboxes would need to collectively
pay a total of around $7-13 million per month (or $84-156 million per year) to obtain the same volume of traffic as they receive from Wikipedia for free."
!!
Doyensec
doyensec@infosec.exchangeTaking his previous research to the next level, our Maxence Schmitt explores how to bypass various upload restrictions to exploit client-side path traversal. Read about it in our latest blog post today!
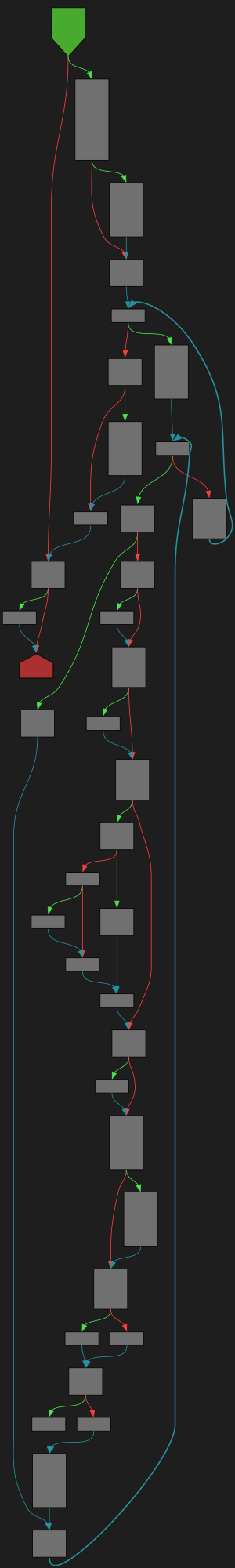
CFG Bot 🤖
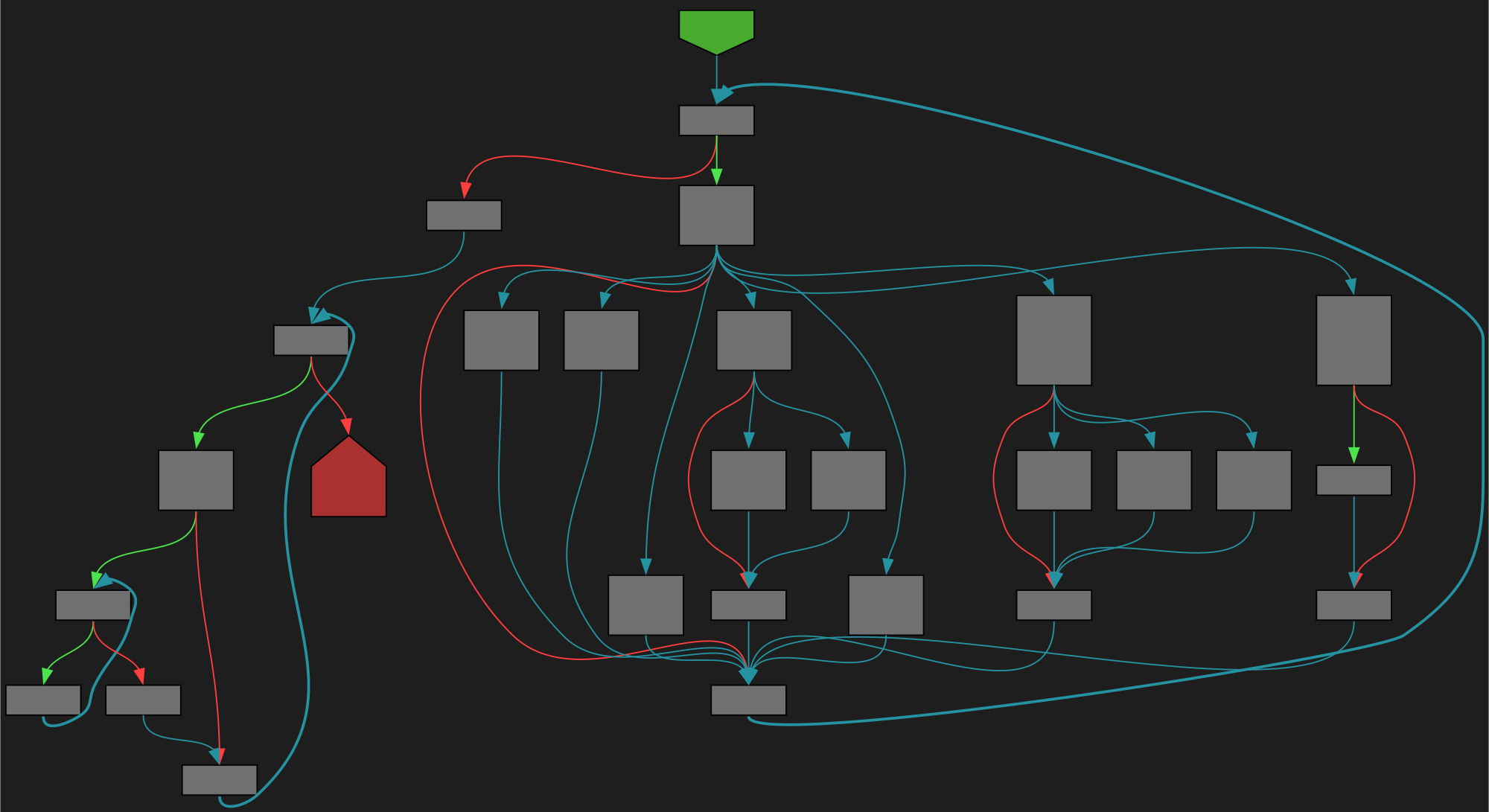
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a7fb8c4
RenameFile
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a7fb8c4.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a7fb8c4.json&colors=light
nullagent
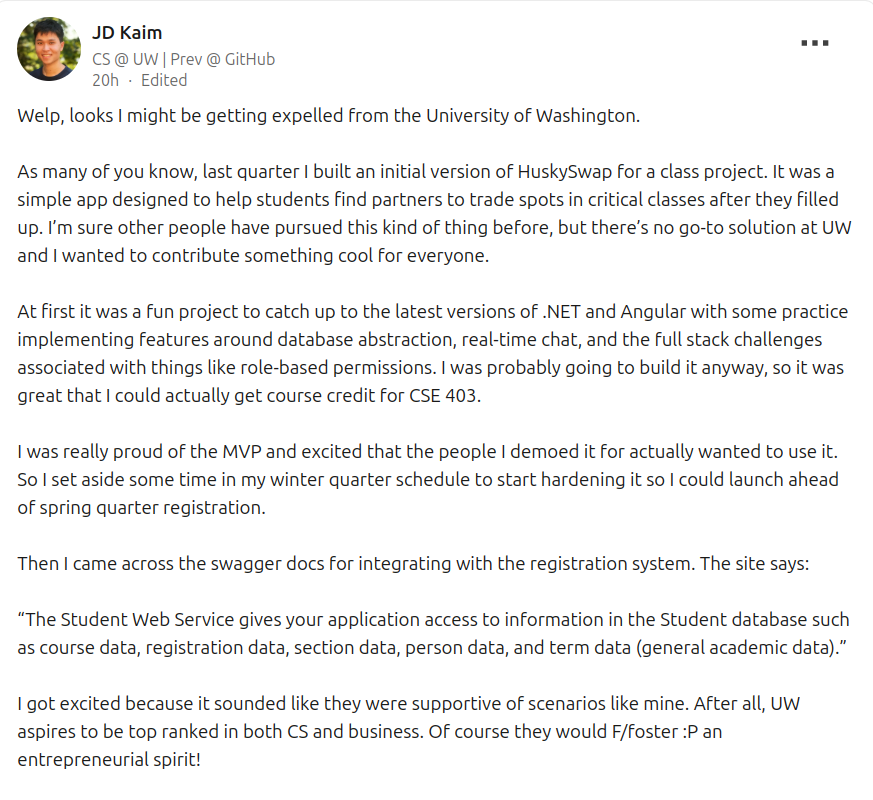
nullagent@partyon.xyzHearing about a young hacker whose being extorted by the University of Washington, not cool UW.
The student claims they built an app to help kids get the course schedules they want, a hack as old as time, and the university decided to expel him until he ports his app to the university's internal systems.
This would be unpaid labor.
Until then his class registration is on hold and he can't register or attend his last few classes. 🥴
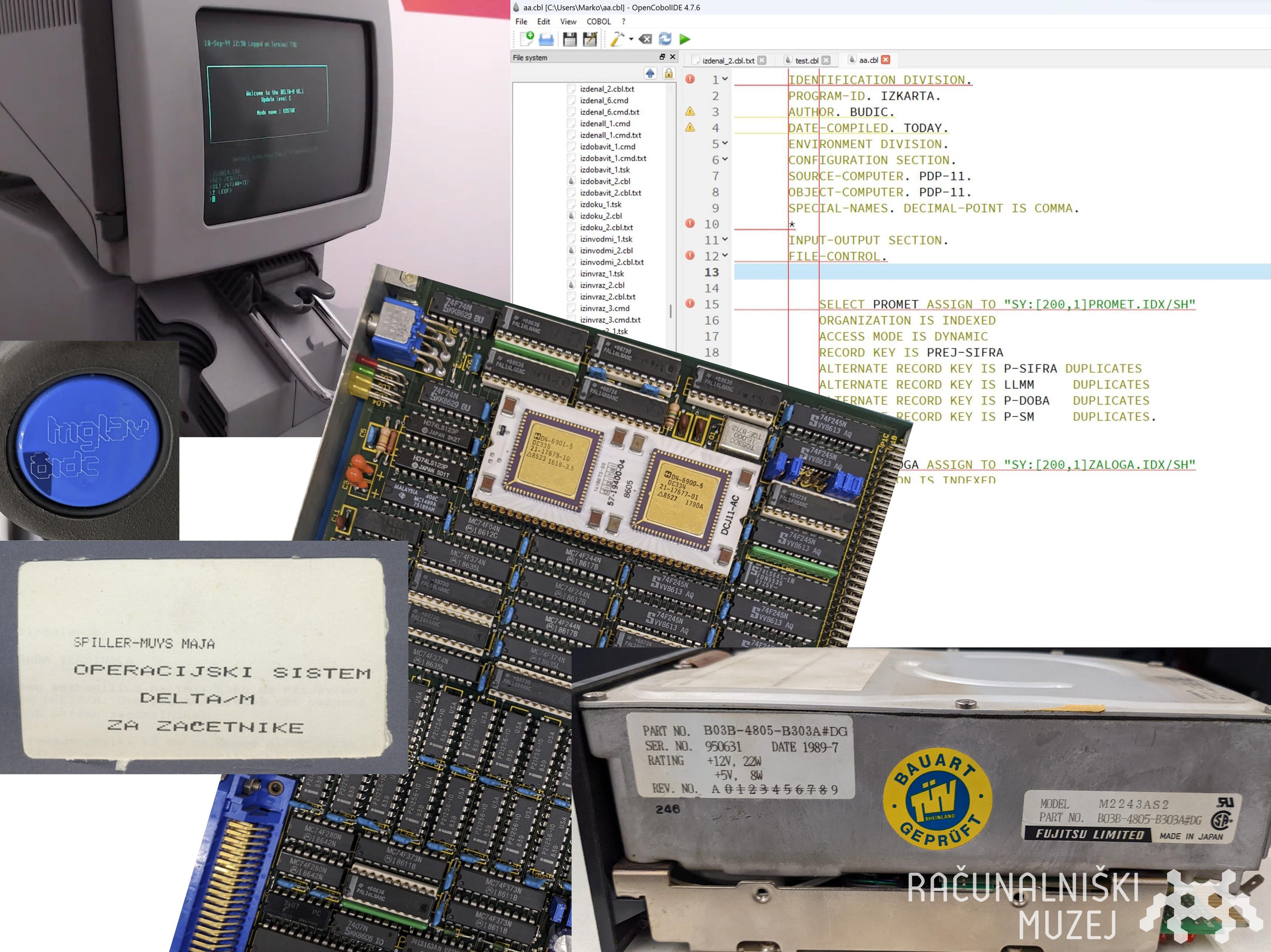
Computer History Museum 🇸🇮
muzej@mastodon.social🎂🗻 Looking for simh/DEC J-11 experts to volunteer for our project of developing a libre emulator of the Slovenian Iskra Delta Triglav computer which is celebrating 40 years! We have ROM and disk images (RSX11-M/DELTA-M OS) and lots of documentation. Interested? 👉 marko@muzej.si
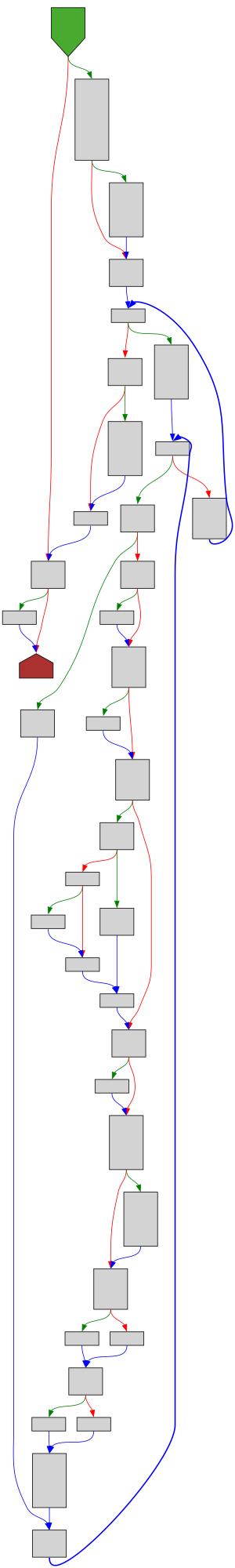
CFG Bot 🤖
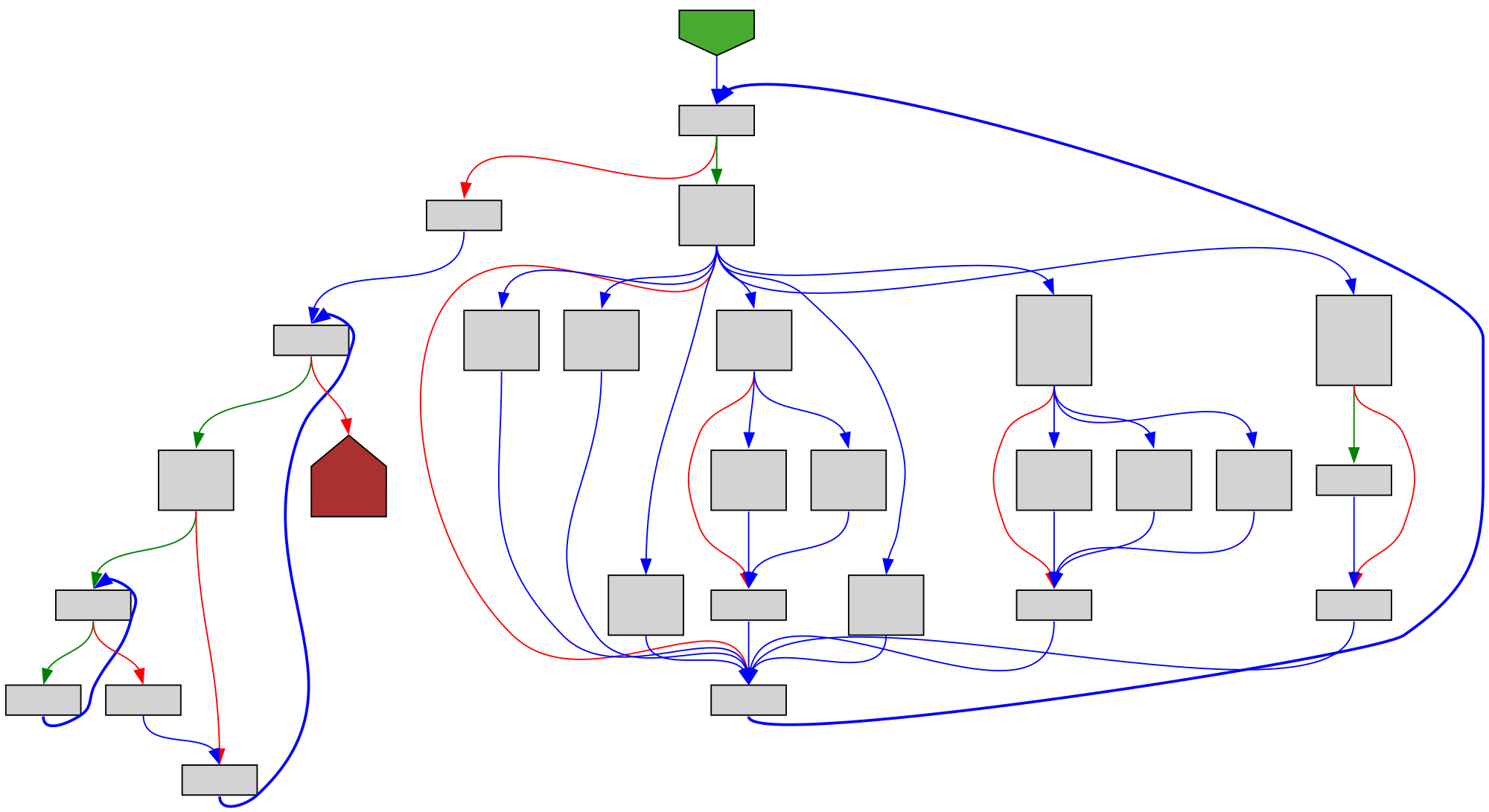
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
File: src/runtime/map.go:1255 https://github.com/golang/go/blob/refs/tags/go1.23.4/src/runtime/map.go#L1255
func evacuate(t *maptype, h *hmap, oldbucket uintptr)
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fruntime%2Fmap.go%23L1255&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fruntime%2Fmap.go%23L1255&colors=light
screaminggoat
screaminggoat@infosec.exchange@jerry Ivanti zero-day mega-toot:
- Ivanti blog post: Security Update: Ivanti Connect Secure, Policy Secure and Neurons for ZTA Gateways
- Ivanti security advisory: Security Advisory Ivanti Connect Secure, Policy Secure & ZTA Gateways (CVE-2025-0282, CVE-2025-0283)
- U.S. CISA mitigation guidance: CISA Mitigation Instructions for CVE-2025-0282
- Mandiant observed post-exploitation activity and forensics (includes IOC, Yara): Ivanti Connect Secure VPN Targeted in New Zero-Day Exploitation
Government security advisories:
- U.S.: CISA Adds One Vulnerability to the KEV Catalog
- Canada: Ivanti security advisory (AV25-008)
- UK: Active exploitation of vulnerability affecting Ivanti Connect Secure
Regular infosec news reporting:
- Security Week: Ivanti Warns of New Zero-Day Attacks Hitting Connect Secure Product
- The Record: Ivanti warns hackers are exploiting new vulnerability
- Bleeping Computer: Ivanti warns of new Connect Secure flaw used in zero-day attacks
Marcus Hutchins 
malwaretech@infosec.exchange
Why You Probably Don't Need A VPN To Stay Secure On Public Wi-Fi
You've probably heard advice about how hackers can steal all your sensitive information if you don't use a VPN on public Wi-Fi, but is that actually true? In this video I'll walk through some of the major risks of public Wi-Fi such as Man-In-The-Middle Attacks, Rogue Access Points, SSL Stripping, and TLS Downgrades, as well as discuss how modern security measures prevent them.
https://www.youtube.com/watch?v=i7GwjGGwxzg
CFG Bot 🤖
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
File: src/cmd/trace/gen.go:41 https://github.com/golang/go/blob/refs/tags/go1.23.4/src/cmd/trace/gen.go#L41
func runGenerator(ctx *traceContext, g generator, parsed *parsedTrace, opts *genOpts)
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Ftrace%2Fgen.go%23L41&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Ftrace%2Fgen.go%23L41&colors=light
Caitlin Condon
catc0n@infosec.exchangeNew #Ivanti Connect Secure #0day — I'm sure we'll see Mandiant and MSTIC write-ups shortly on whichever threat campaign/actor was hitting CVE-2025-0282. https://www.rapid7.com/blog/post/2025/01/08/etr-cve-2025-0282-ivanti-connect-secure-zero-day-exploited-in-the-wild/
Blort™ 🐀Ⓥ🥋☣️
Blort@social.tchncs.deI'm very happy to see @kagihq joining Peertube with their inaugural video below about what makes Kagi independent search special!
https://tilvids.com/w/twGQeYV9c1TGwMmbdXtY2q
Remember to follow their Peertube account at @kagi and boost to encourage and show them the effort is appreciated! Also do check out their excellent lenses feature, shown in the video.
buherator
buheratorhttps://u1f383.github.io/linux/2025/01/08/two-network-related-vulnerabilities-analysis.html
#Linux kernel - CVE-2023-6932 CVE-2023-0461
buherator
buheratorhttps://www.netspi.com/blog/technical-blog/cloud-pentesting/hijacking-azure-machine-learning-notebooks/
screaminggoat
screaminggoat@infosec.exchangeGitLab security advisory 08 January 2025: GitLab Patch Release: 17.7.1, 17.6.3, 17.5.5
- CVE-2025-0194 (6.5 medium) Possible access token exposure in GitLab logs
- CVE-2024-6324 (4.3 medium) Cyclic reference of epics leads resource exhaustion
- CVE-2024-12431 (4.3 medium) Unauthorized user can manipulate status of issues in public projects
- CVE-2024-13041 (4.3 medium) Instance SAML does not respect external_provider configuration
❄️☃️Merry Jerry🎄🌲
jerry@infosec.exchangeHi all. Given the recent announcement from Meta about AI personas and allowed behavior, I am moving threads.net back to a limit, and will likely move them to a block in the future on infosec.exchange. I can’t ignore the reality that the changes they’re making are specifically intended to permit attacks on many of the people that call this place home. I won’t rule out that they walk the changes back, which is why I’m not jumping to sever the nearly 4000 mutual follow relationships between people on threads and here.
MADWeb Workshop
madwebwork@infosec.exchange🚨 Deadline Extended 🚨
By popular demand, the #MADWeb submission deadline is now January 14, 2025 (AoE)! 🗓️
You still have 1 week to send your papers and join us in San Diego!
📜 Submit here: https://madweb25.hotcrp.com
🔗 Details: https://madweb.work
Spread the word!