Posts
3397Following
713Followers
1581Micah Lee
micahflee@infosec.exchange"Apple has agreed to pay $95 million to settle a lawsuit alleging that its voice assistant Siri routinely recorded private conversations that were then sold to third parties for targeted ads." https://arstechnica.com/tech-policy/2025/01/apple-agrees-to-pay-95m-delete-private-conversations-siri-recorded/
buherator
buheratorhttps://arxiv.org/abs/2412.20324
#frombsky
Nahum Shalman
nahumshalman@hachyderm.ioI have tentatively done the work needed to get #Tailscale Taildrive sharing working on #illumos / #solaris.
It works for me. @papertigers please take a look!
https://github.com/nshalman/tailscale/releases/tag/v1.78.1-taildrive-sunos
Molly White
molly0xfff@hachyderm.ioThe world's richest man has joined a growing chorus of right-wing voices attacking Wikipedia as part of an intensifying campaign against free and open access information. Why do they hate it so much?
https://www.citationneeded.news/elon-musk-and-the-rights-war-on-wikipedia/
screaminggoat
screaminggoat@infosec.exchange@vulnerability_lookup @wdormann the vulnerability reporter Yuki Chen says CVE-2024-49113 and is incorrectly tagged as Denial of Service when it should be "information leak": https://twitter.com/guhe120/status/1874605842353594579
Viss
Viss@mastodon.socialheres a work related question for you, if you are in a position where you can hire consulting companies to help with security work (red/blue/eng/etc):
would it be handy to be able to buy a single day of effort, 7hrs of effort, 1hr reporting, and get a report worth sharing with either partners, customers, or leadership?
I'm thinking of building out a new offering. A one-day triage/best-effort assessment. internal, external, whatevs - dealers choice.
Mr. Bitterness
wdormann@infosec.exchangeSo this PoC for CVE-2024-49113 is indeed a thing.
https://www.safebreach.com/blog/ldapnightmare-safebreach-labs-publishes-first-proof-of-concept-exploit-for-cve-2024-49113/
Their writeup is confusingly worded in that it uses both the phrases "victim DC" and "any unpatched Windows Server (not just DCs)", in the same sentence nonetheless.
While the vul can be triggered by any lookup to a malicious LDAP server by any version of Windows, this particular PoC:
- Makes a MS-NRPC Netlogon Remote Protocol to talk to Windows Server, specifically DsrGetDcNameEx2, which gets info about the specified domain.
- Windows Server checks via DNS what LDAP server to talk to to get this info.
- Windows Server talks to the (malicious) LDAP server to service the request.
- The malicious LDAP server sends an unexpected LDAP referral value, causing LSASS.EXE, and subsequently Windows, to fall over.
It's perhaps important to note that CVE-2024-49113 is "just" a DoS, and CVE-2024-49112 is the more juicy RCE one. SafeBreach has indicated that they're still investigating what a full RCE chain might look like.
The fact that SafeBreach called their CVE-2024-49113 exploit "LDAPNightmare" is a bit deceptive, IMO, as CVE-2024-49112 is the thing of nightmares (CVSS 9.8). But hey, whatever gets clicks, amirite?
stacksmashing
stacksmashing@infosec.exchangeDoes someone happen to have a copy of the tangara-hw git repo and could push it to Github? The official repo is 502ing right now
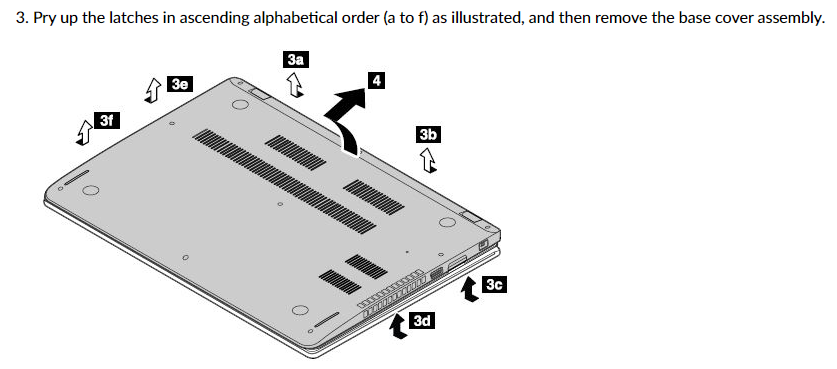
The back of the laptop will not come off :( :( :( no matter what I do :(
There is a diagram on the Lenovo site. They didn't seem to think this was important to include int he video, the video was just like "use caution". It's also baffling. There are "latches" that have to be "pried up". How do you "pry" a "latch". What does that mean. Does it mean apply force. Latch 3D simply will not unlatch and I can see new little-but-distinct creases forming in the aluminum back of the unit
buherator
buheratorProject Zero Bot
p0botWindows Kernel False File Immutability attack on registry hives via the Cloud Filter API
https://project-zero.issues.chromium.org/issues/42451734
CVE-2024-49114
Alexandre Borges
alexandreborges@infosec.exchangeDiving into ADB protocol internals:
part 01: https://www.synacktiv.com/publications/diving-into-adb-protocol-internals-12
part 02: https://www.synacktiv.com/en/publications/diving-into-adb-protocol-internals-22
#adb #mobile #protocol #informationsecurity #cybersecurity #reverseengineering
CFG Bot 🤖
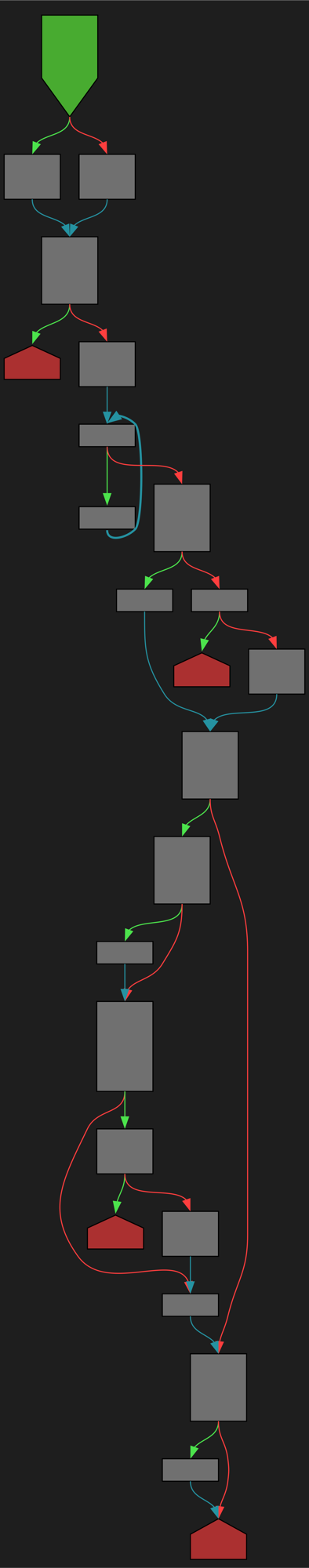
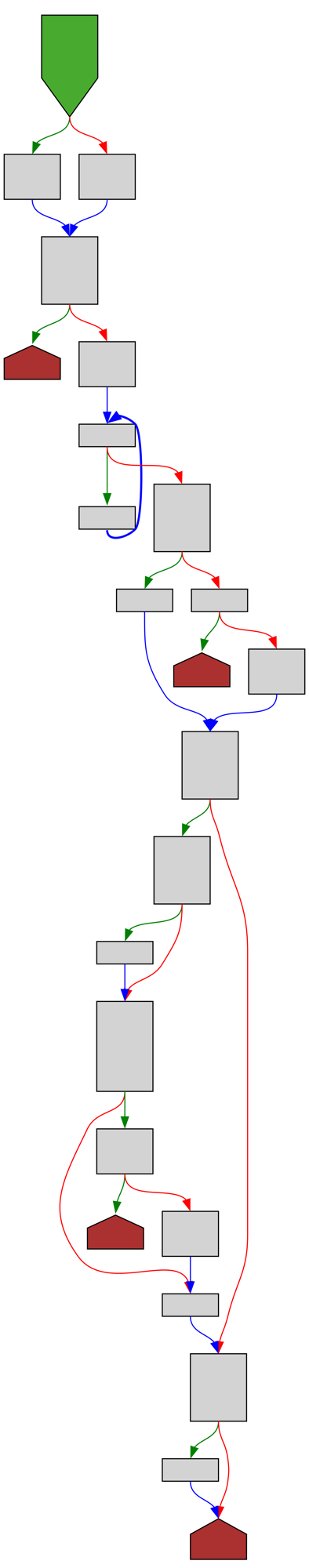
cfgbot@mastodon.socialProject: python/cpython https://github.com/python/cpython
File: Lib/ntpath.py:343 https://github.com/python/cpython/blob/2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd/Lib/ntpath.py#L343
def expanduser(path):
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fpython%2Fcpython%2Fblob%2F2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd%2FLib%2Fntpath.py%23L343&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fpython%2Fcpython%2Fblob%2F2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd%2FLib%2Fntpath.py%23L343&colors=light