Posts
3013Following
699Followers
1547Foone🏳️⚧️
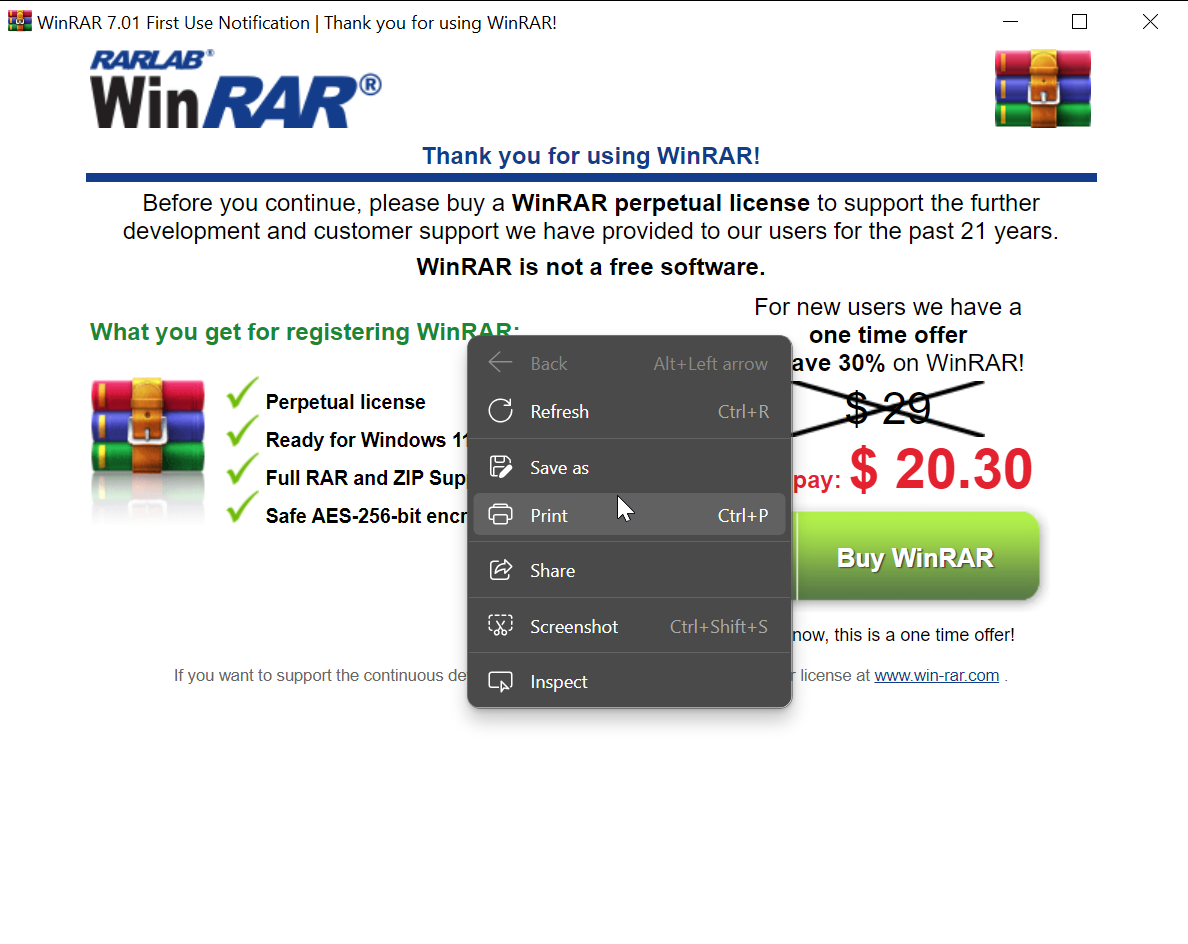
foone@digipres.clubFeel old yet? The winrar registration nag screen is Electron these days.
EDIT: Whoops, it seems I'm wrong: This is just an embedded webview, which on Win10 is apparently chromium-backed (probably because it's Edge)
Virtual Colossus
virtualcolossus@infosec.exchange#Polish researchers have discovered components of a German #Enigma cipher machine, crucial to the Nazi wartime communications system, on Sobieszewska island near the city of Gdańsk. All in all, 8 rotors and various other parts were recovered. https://tvpworld.com/84053156/fragments-of-rare-german-enigma-machine-unearthed-in-poland
buherator
buherator"[Person] will be the wall
that guides us through the night!"
buherator
buheratorAs a company owner, I took one for the team and set up a personal bank account for testing. Surely enough, it resulted in me getting fucked *at another bank* (costing me considerable money).
buherator
buheratorhttps://www.ibm.com/support/pages/node/7179158
Emphasis mine:
"A user with authority to a *view* can alter the based-on *physical file* security attributes without having object management rights to the physical file."
I wonder what other discrepancies there may be between Db2 and other interfaces.
Stephen Rees-Carter 
valorin@phpc.social
One of the fun parts of doing my security audits is coming across unexpected code that looks exploitable, and trying it out myself to see what possibilities exist.
In a recent audit, I found myself asking... What if you hashed null?
https://securinglaravel.com/security-tip-what-if-you-hashed-null/
Prof. Emily M. Bender(she/her)
emilymbender@dair-community.socialCalling all Mystery AI Hype Theater 3000 fans! Have you found a piece of Fresh AI Hell but not known where to send it? Here's the spot:
https://thecon.ai/submit-fresh-ai-hell/
Help @alexhanna.bsky.social and me clean out the Fresh Hell by submitting it there!
💻📡🛰️ IooNag
IooNag@infosec.exchangeDevOps practices are all well and good, but beware of the configuration of the tools that access your production.
I've written a blog post sharing some dangerous ways Argo CD can be configured, detailing the security impact: https://ledger.com/argo-cd-security-misconfiguration-adventures
buherator
buheratorAnd this comes from someone who's been writing #documentation professionally at #Microsoft! I'm at loss for words...
https://github.com/MicrosoftDocs/WSL/pull/2021#issuecomment-2548390973
buherator
buheratorSerious question.
Project Zero Bot
p0botLinux: Panthor: racy panthor_vm_pool_get_vm() leads to UAF
https://project-zero.issues.chromium.org/issues/377500597
CVE-2024-53080
Project Zero Bot
p0botLinux >=5.10: wrong order of operations on close_and_free_vma error path causes temporary dangling PTE
https://project-zero.issues.chromium.org/issues/374117290
CVE-2024-53096
David Gerard
davidgerard@circumstances.runMicrosoft refuses pull request to put documentation in readable table form because LLMs are bad at parsing tables https://github.com/MicrosoftDocs/WSL/pull/2021
tmpout
tmpout@haunted.computerWe are extending our call for papers to January 1, 2025!
We are now targeting an end of January release.
If you have any Linux/ELF related research, projects, or papers, we would love to publish them!
Huge thank you to everyone who has already submitted!
Phrack
phrack@haunted.computerWe updated our CFP for Phrack 72! The deadline is now April 1st 2025. Check the site for specifics on how to contribute, as well as some inspiration! We also posted a link to purchase physical copies of Phrack 71, and a donation link too. Enjoy!
screaminggoat
screaminggoat@infosec.exchangeCCCS (Canada): Alert - CVE-2024-53677 - Vulnerability impacting Apache Struts 2
I see multiple government organizations emphasize the criticality of CVE-2024-53677 (CVSSv4: 9.5 critical) affecting both end-of-life and current versions of Apache Struts 2. A malicious actor can exploit this vulnerability to traverse system paths, upload malicious files, and perform remote code execution.
The Canadian Centre for Cyber Security (CCCS) is aware that a proof of concept (POC) exploit is available for this CVE.
#apache #struts #CVE_2024_53677 #vulnerability #cve #infosec #cybersecurity #proofofconcept #poc