Posts
2681Following
677Followers
1504screaminggoat
screaminggoat@infosec.exchangeHappy #PatchTuesday from Splunk:
- SVD-2024-1201 Information Disclosure in Mobile Alert Responses in Splunk Secure Gateway (CVE-2024-53243, 4.3 medium)
- SVD-2024-1202 Risky command safeguards bypass in "/en-US/app/search/report" endpoint through "s" parameter (CVE-2024-53244, 5.7 medium)
- SVD-2024-1203 Information Disclosure due to Username Collision with a Role that has the same Name as the User (CVE-2024-53245, 3.1 low)
- SVD-2024-1204 Sensitive Information Disclosure through SPL commands (CVE-2024-53246, 5.3 medium)
- SVD-2024-1205 Remote Code Execution through Deserialization of Untrusted Data in Splunk Secure Gateway app (CVE-2024-53247, 8.8 high)
- SVD-2024-1206 Third-Party Package Updates in Splunk Enterprise - December 2024 (multiple CVEs)
- SVD-2024-1207 Third-Party Package Updates in Splunk Universal Forwarder - December 2024 (CVE-2024-5535, 9.1 critical)
No verbiage of exploitation.
buherator
buheratorMr. Bitterness
wdormann@infosec.exchangeCLFS seems like the gift that keeps on giving.
CVE-2024-49138 is being exploited ITW, apparently.
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49138
Given that it says that it's publicly disclosed, does anybody know offhand where CVE-2024-49138 is discussed publicly?
screaminggoat
screaminggoat@infosec.exchangeHappy #PatchTuesday from Microsoft: 71 new vulnerabilities, ONE ZERO-DAY:
- CVE-2024-49138 (7.8 high) Windows Common Log File System Driver Elevation of Privilege Vulnerability
Update for CVE-2024-38033 (7.3 high, from 09 July 2024) PowerShell Elevation of Privilege Vulnerability was reissued a patch for all affected versions of Windows Server 2012 and Windows Server 2012 R2.
The Microsoft data arrived almost 10 minutes early.
cc: @goatyell @mttaggart @hrbrmstr @ntkramer @iagox86 @zackwhittaker @dreadpir8robots @TheDustinChilds @neurovagrant @xorhex @campuscodi @briankrebs (remember to remove the mentions to avoid ReplyAll madness)
#microsoft #msrc #vulnerability #cve #infosec #cybersecurity
buherator
buheratorhttps://blog.scrt.ch/2024/12/05/attacking-cortex-xdr-from-an-unprivileged-user-perspective/
Privileged file access by endpoint security strikes again ;)
Caitlin Condon
catc0n@infosec.exchangeI'd imagine this is gonna change about three times an hour at the rate new info (and intel) is being shared, but Rapid7 is also investigating a bunch of incidents related to this. Our MDR folk have confirmed successful exploitation in customer environments and observed enumeration and post-exploitation behavior similar to what @huntress has already shared. https://www.rapid7.com/blog/post/2024/12/10/etr-widespread-exploitation-of-cleo-file-transfer-software-cve-2024-50623/
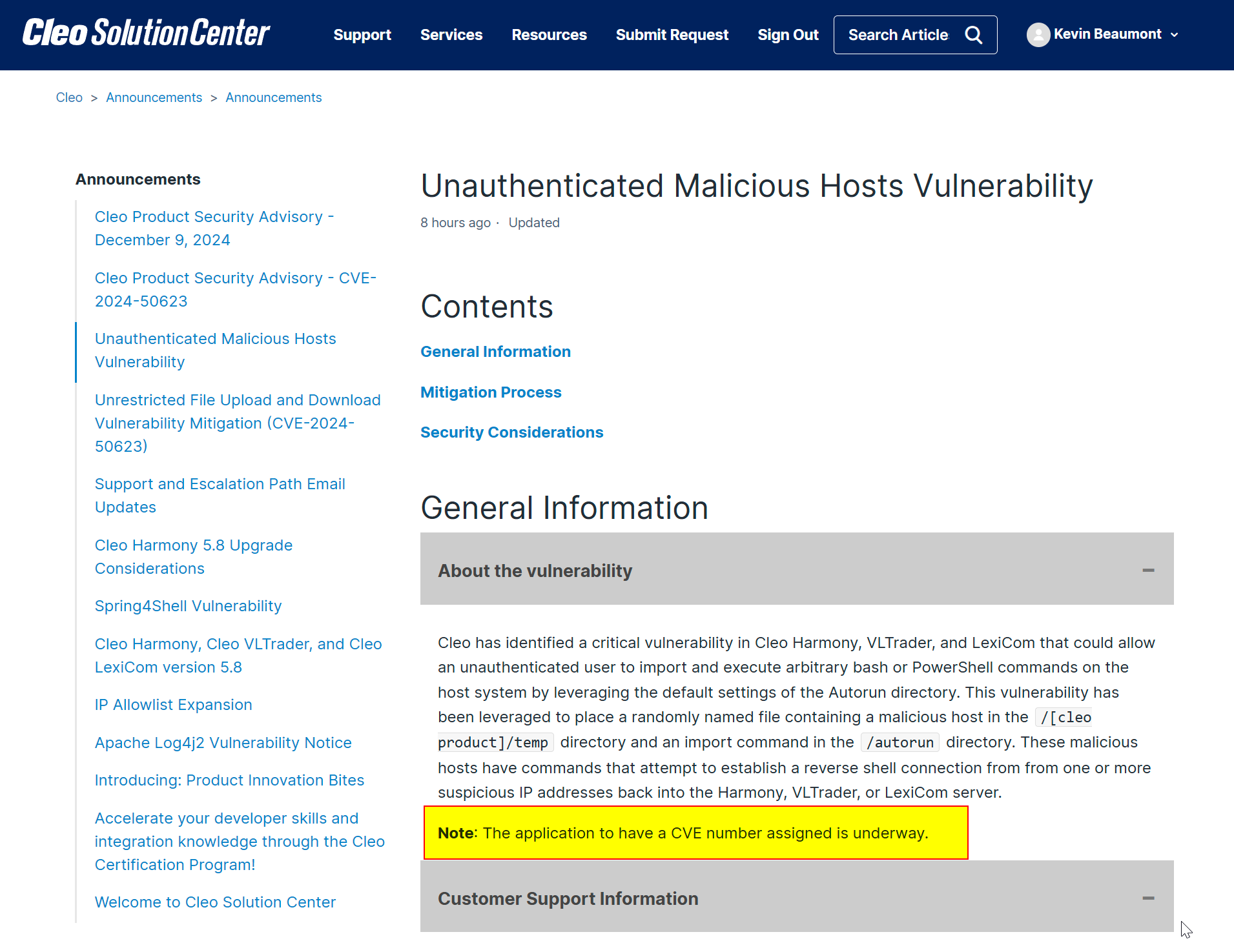
Kevin Beaumont
GossiTheDog@cyberplace.socialCleo have issued a (paywalled) advisory about the zero day, saying a new CVE number is being allocated.
Cisco Talos
TalosSecurity@mstdn.socialCisco Talos' Vulnerability Research team recently discovered two vulnerabilities in MC Technologies LR Router and three vulnerabilities in the GoCast service. Read the latest in the Vulnerability Roundup: https://blog.talosintelligence.com/mc-lr-router-and-gocast-zero-day-vulnerabilities-2/
Fedi.Tips
FediTips@social.growyourown.servicesThe official PeerTube app just released:
 https://play.google.com/store/apps/details?id=org.framasoft.peertube
https://play.google.com/store/apps/details?id=org.framasoft.peertube
 https://apps.apple.com/app/peertube/id6737834858
https://apps.apple.com/app/peertube/id6737834858
(coming soon to F-Droid)
How to add more servers:
1. Click Explore
2. Click "Show More Platforms" in middle of the screen
3. Click the + icon in top right
4. Enter server's web address & connect
5. Click "Platforms" at the bottom to browse added servers
Don't blame Framasoft for missing features, blame Apple and Google's idiotic rules:
https://framablog.org/2024/12/10/peertube-mobile-app-discover-videos-while-caring-for-your-attention
🧵 1/2
Fight for the Future
fight@mastodon.fightforthefuture.orgOver 350 musicians are speaking out to demand that major labels drop a lawsuit aimed to destroy the Internet Archive.
/r/netsec
_r_netsec@infosec.exchangeThe Ruby on Rails _json Juggling Attack https://nastystereo.com/security/rails-_json-juggling-attack.html
HN Security
hnsec@infosec.exchangeHello Rustaceans! Our technical director @raptor is back at it.
In this second installment of our #Rust series, “An offensive Rust encore”, he will guide you in bringing your skills to the next level by using a new PoC #RedTeaming tool as an excuse:
buherator
buheratorhttps://github.com/google/security-research/security/advisories/GHSA-h65x-r3mq-jr2v
buherator
buheratorhttps://msrc.microsoft.com/blog/2024/12/mitigating-ntlm-relay-attacks-by-default/
✧✦Catherine✦✧
whitequark@mastodon.socialfascinating result about the performance of memory-safe PNG decoders and the usefulness of autovectorization in real projects https://www.reddit.com/r/rust/comments/1ha7uyi/memorysafe_png_decoders_now_vastly_outperform_c/
blacktop
blacktop@mastodon.socialHigh level diff of iOS 18.2 RC vs. iOS 18.2 RC2 🎉
https://github.com/blacktop/ipsw-diffs/blob/main/18_2_22C150__vs_18_2_22C151/README.md
pancake 
pancake@infosec.exchange
Totally missed Huawei's new programming languages: ArkTS (ts subset that compiles to native code) and Cangjie (too much chinese documentation for me to understand it):
https://en.wikipedia.org/wiki/ArkTS
https://www.gizmochina.com/2024/06/21/huawei-cangjie-programming-language/