Posts
2467Following
661Followers
1486Kees Cook (old account)
kees@fosstodon.org~25M lines of code in the Linux kernel drivers/ directory. O_O
~15M LoC for everything else.
Johnathan Norman
spoofyroot@bird.makeupHello everyone, fun fact, UAC bypasses = bounty money when Administrator Protection is enabled. We checked many but we fully expect we missed some. You could simply dig up old research, try it and if it works make some cash. This feature is in an early stage, help us improve it.
buherator
buheratorhttps://googleprojectzero.blogspot.com/2024/10/from-naptime-to-big-sleep.html
"we want to reiterate that these are highly experimental results. The position of the Big Sleep team is that at present, it%27s likely that a target-specific fuzzer would be at least as effective (at finding vulnerabilities). " (still wow!)
buherator
buheratorhttps://blog.trailofbits.com/2024/10/31/fuzzing-between-the-lines-in-popular-barcode-software/
Csepp 🌢
csepp@merveilles.townhttps://netboot.xyz/ is really cool, just used it to install Debian for a relative. 
cc #netbootxyz #theWorkshop
Computer History Museum 🇸🇮
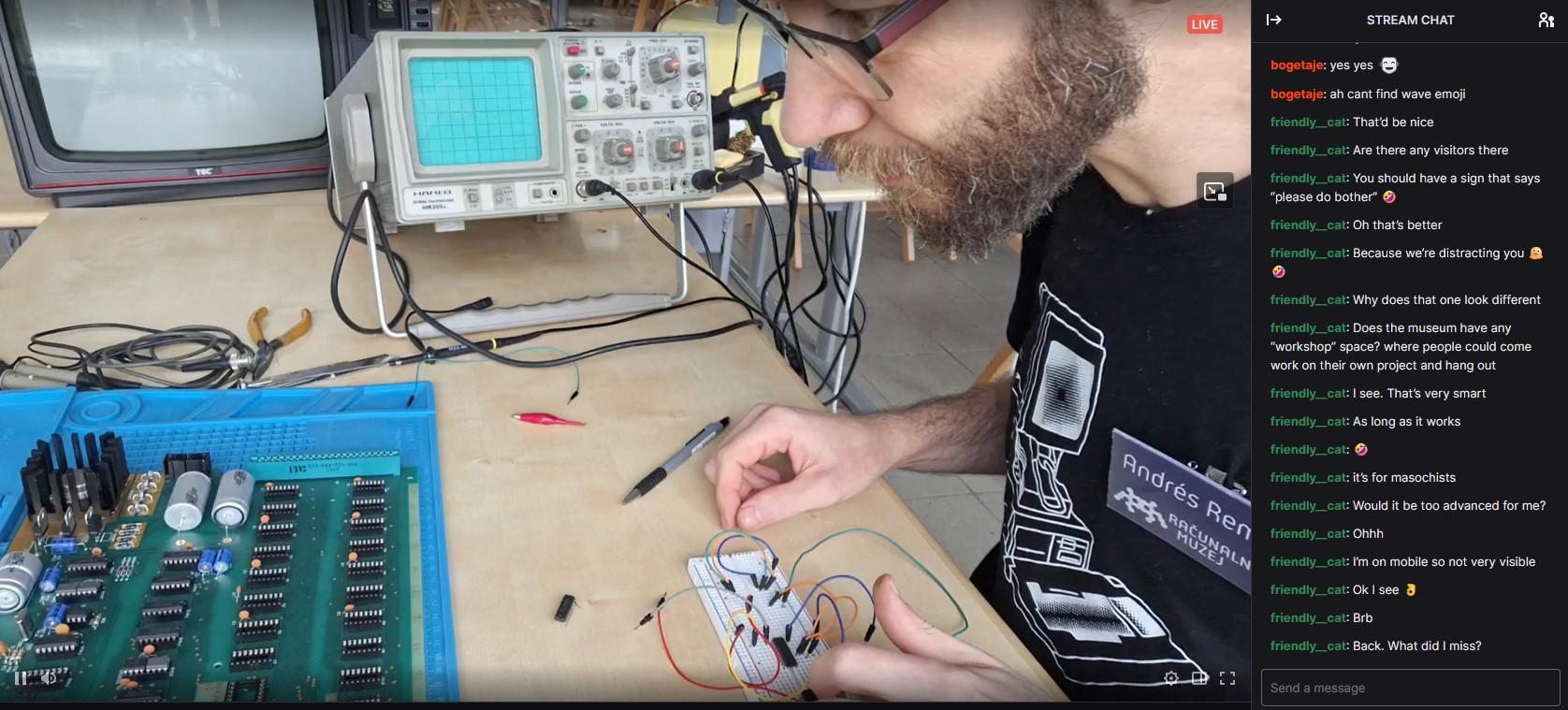
muzej@mastodon.socialWe're live! Join us for a stream as we build an Apple I replica! 🛠️✨ https://www.twitch.tv/racunalniskimuzej
#computermuseum #computerhistory #slovenia #ljubljana #softwareheritage #digitalheritage #nostalgia #applei #museo #retrocomputing #Twitch #livestream #vintagecomputing #stream #SmallStreamers #applenerd #apple #streaming #live #twitchstreamer #apple1 #retrogaming #informatica
Adrian Taylor
adetaylor@mastodon.online2024 Q3 update from #googlechrome security https://www.chromium.org/Home/chromium-security/quarterly-updates/#q3-2024
Kevin Beaumont
GossiTheDog@cyberplace.socialRemember a few weeks ago when Okta dropped a critical auth bypass vuln they’d been aware of for weeks on a Friday at 11pm?
Well, they’re back again with another auth bypass dropped on a Friday at 11pm https://infosec.exchange/@SecureOwl/113409933398662230
Chris Merkel 🐀👨🏼🍳
chrismerkel@infosec.exchangeNot sure I want to open this. If Cobalt Strike had a scent, what would it be and why?
buherator
buherator"This is an overview of CVE-2024-29506, CVE-2024-29507, CVE-2024-29508, and CVE-2024-29509"
https://codeanlabs.com/blog/research/ghostscript-wrap-up-overflowing-buffers/
buherator
buheratorhttps://www.cyberark.com/resources/threat-research-blog/discovering-hidden-vulnerabilities-in-portainer-with-codeql
buherator
buheratorWendy Nather
wendynather@infosec.exchangeAs you know, I've been talking about the #SecurityPovertyLine for over ten years now, and I'm always learning new things that add to my thinking on it. In my work with the National Academy of Sciences committee on cyber hard problems, I got to hear a presentation from @fuzztech that really opened my eyes.
It seems that US law enforcement is also below the security poverty line. Really. They struggle with protecting their own infrastructure (which includes huge amounts of digital data that now has to be stored as evidence for, like, forever -- as innocent people are still being exonerated decades later), and they also struggle with being able to help victims of cyber-enabled crime.
This presentation (which starts at 4:20 in the video) is open to the public, and I believe it needs more attention, as this problem affects not only SMBs, but also the very fabric of society. Have a look:
buherator
buheratorhttps://seclists.org/fulldisclosure/2024/Oct/18
Jann Horn
jann@infosec.exchange@pid_eins but do we have the software/hardware infrastructure needed to actually make this secure on a typical Linux desktop machine?
To me, the core purpose of disk encryption is protect a machine against an attacker who steals the entire, powered-off machine; and it's easy to mess up unattended disk encryption so that this is easy to break. The communication with the TPM needs to be protected against interposer attacks somehow (see https://www.nccgroup.com/us/research-blog/tpm-genie-interposer-attacks-against-the-trusted-platform-module-serial-bus/ ); the disk ideally should not just be encrypted but also integrity-protected (because in some settings, the disk encryption is then relied on for security against adaptive online attacks instead of security against a one-time-snapshot passive attacker); you need rollback protection against someone booting a super vulnerable outdated OS image; bugs in device drivers turn into disk encryption bypasses (and notably Linux basically trusts PCI devices to not be actively evil); and so on.
So I'm worried that providing TPM-based disk unlock as an easy-to-configure mechanism might give people a false sense of security. With password-based disk encryption, to me, the core security promise is easy: If someone steals your (not-too-recently-) powered-off computer, they can't get any of the data out of it unless they break your password. With TPM-based unlock, the story is a lot more complex...
tmpout
tmpout@haunted.computertmp.0ut Volume 4 is happening! Our call for papers is now open, and we're excited to see what you've been working on 👀 read the full announcement here: https://tmpout.sh/blog/vol4-cfp.html
metlstorm
metlstorm@infosec.exchange@buherator Oh my god I had no idea (or maybe i blanked it out?!) that talk had been video'd and made it to youtube.
My main memory of that talk is that i was the closing talk of the con, and at some point mid way thru i realised i was out of time, and instead of doing the usual thing of rushing it thru to the end which no one enjoys or remembers, I decided that anyone who needed to leave to go pick up their kids or whatever could just get up and leave, and i would keep going until I was done. Despite poor conference organiser @sputina sitting in the front row having a conniption fit making "wrap it uppppp" gestures, and then eventually also just giving up and crying to herself. I don't recall seeing anyone leave, but maybe that's just my head-canon version of it.
This was a pretty cathartic (albeit maybe a bit self indulgent) talk to write and do.
I ... was not expecting it to have held up so well, and, having worked with @dave_aitel and also read a lot of his output over the years, I respect dave a heap, so getting a 10 outta 10 from dave is ... I'm actually kinda chuffed about that.

 🌻
🌻 

