Posts
3368Following
712Followers
1580buherator
buheratorhttps://therecord.media/recently-patched-firefox-bug-being-used-against-tor-browser-users
Edit: as @zeljkazorz pointed out, Tor disputed this claim!
Ludic 🧛
ludicity@mastodon.sprawl.clubGreat news everyone! I saw code so terrible yesterday that I quit my job on the spot, for realsies. Enjoy what should be the last post about me gazing directly into corporate-hell:
https://ludic.mataroa.blog/blog/get-me-out-of-data-hell/
Future posts will be about the dystopian hellscape that I conjure into being at my own business.
Charlie Stross
cstross@wandering.shopI love this!
"One day, Linus accidentally attempted to use his hard drive to dial the university, resulting in his master boot sector starting with "ATDT" and the university modem-pool phone number. After recovering from this, he implemented file permissions in his kernel."
https://lwn.net/Articles/928581/
Cyclone
cyclone@infosec.exchangeWe just launched a new forum for the hash cracking community, hashpwn. Head over, sign up, and get crackin!
https://forum.hashpwn.net
screaminggoat
screaminggoat@infosec.exchangewatchTowr: Fortinet FortiGate CVE-2024-23113 - A Super Complex Vulnerability In A Super Secure Appliance In 2024
Reference: CVE-2024-23113 (9.8 critical, disclosed 08 February 2024 by Fortinet, added to CISA KEV Catalog 09 October 2024) Fortinet Multiple Products Format String Vulnerability
I personally love the snark that watchTowr brings to the infosec community. If you didn't already grasp it from all the memes, you'll understand once you start reading this blog post. watchTowr covers locating the vulnerability CVE-2024-23113 and finding the root cause. I know the term rabbit hole is used often, but in this case, each vulnerable/patched version of their firmware provides different behavior to exploitation attempts and these are explained. No one's safe from watchTowr: they even include a dis for Check Point:
I mean, it's one up from Checkpoint's 'buy another Checkpoint device to put infront of your vulnerable Checkpoint device'
#CVE_2024_23113 #fortinet #vulnerability #eitw #vulnerabilityanalysis #cybersecurity #infosec #cve #activeexploitation #kev
Kagi HQ
kagihq@mastodon.socialKagi's Snaps allows you to easily limit search results to a specific website by using the @ symbol followed by a short code for the site and then your search query🪄
More on how to use and contribute to Snaps: https://help.kagi.com/kagi/features/snaps.html
TrendAI Zero Day Initiative
thezdi@infosec.exchangeHuh.... Turns out electricity is a little bit spicier in Ireland. Lesson learned. Setup for #Pwn2Own Ireland continues...
buherator
buheratorhttps://kaist-hacking.github.io/publication/park-rgfuzz/
Royce Williams
tychotithonus@infosec.exchangeThere's something specifically and deeply evil about making kids watch ads for extra stuff in games.
Bryan Steele 
brynet@bsd.network
As a planned follow-up to the splitting of sshd-session out of the sshd(8) binary, sshd-session has be further split into a new sshd-auth binary to handle user authentication.
djm@ modified src/usr.bin/ssh/*: Split per-connection sshd-session binary
This splits the user authentication code from the sshd-session binary into a separate sshd-auth binary. This will be executed by sshd-session to complete the user authentication phase of the protocol only.
Splitting this code into a separate binary ensures that the crucial pre-authentication attack surface has an entirely disjoint address space from the code used for the rest of the connection. It also yields a small runtime memory saving as the authentication code will be unloaded after the authentication phase completes.
Joint work with markus@ feedback deraadt@
Tested in snaps since last week
Also only on #OpenBSD, this new sshd-authd binary gets relinked on boot, as with sshd-session and sshd.
deraadt@ modified src/etc/rc: sshd-auth also has a relink kit
Brewster Kahle
brewsterkahle@mastodon.archive.orgThe @internetarchive’s Wayback Machine resumed in a provisional, read-only manner.
Sorry, no Save Page Now yet.
Safe to resume but might need further maintenance, in which case it will be suspended again.
Please be gentle https://web.archive.org
More as it happens.
buherator
buheratorhttps://therecord.media/casio-ransomware-attack-exposed-emplyee-customer-data
First the IA, now Casio - nothing is sacred for these punks!
buherator
buherator(Bonus points for not using the Esolang wiki)
Street Art Utopia
streetartutopia@mastodon.onlinePainted by a homeless man: https://streetartutopia.com/2024/10/13/painted-by-a-homeless-man/
Steve Bellovin
SteveBellovin@mastodon.lawprofs.orgDoing my weekly update of TeXLive, I spotted this as a new feature. Just what I want—SQL injection in document source…
Jeff Atwood
codinghorror@infosec.exchangeWriting things down isn't just good science; it's the ultimate kink. 😝
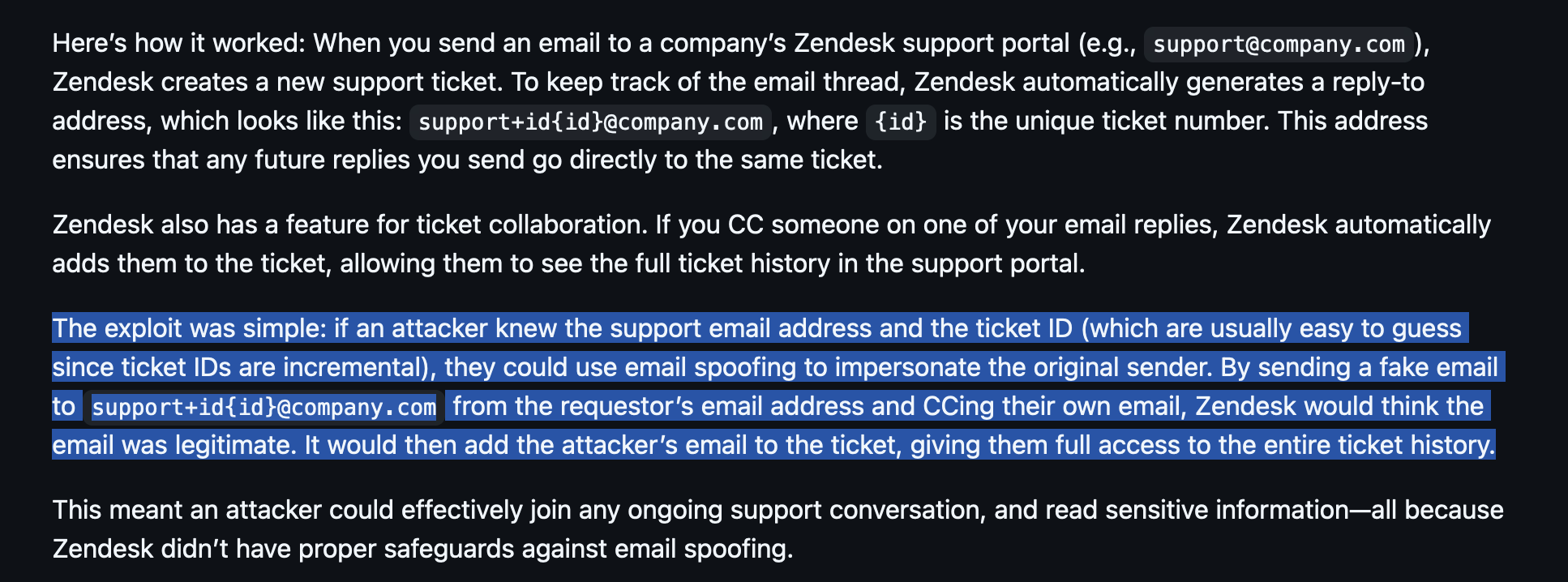
Viss
Viss@mastodon.socialthe zendesk hack, for anyone interested
https://gist.github.com/hackermondev/68ec8ed145fcee49d2f5e2b9d2cf2e52