Posts
2697Following
681Followers
1504buherator
buheratorhttps://www.synacktiv.com/en/publications/defend-against-vampires-with-10-gbps-network-encryption
screaminggoat
screaminggoat@infosec.exchangeSolarWinds: SolarWinds Access Rights Manager (ARM) Deserialization of Untrusted Data Remote Code Execution Vulnerability (CVE-2024-28991)
CVE-2024-28991 (9.0 critical, disclosed 12 September 2024) SolarWinds Access Rights Manager (ARM) was found to be susceptible to a remote code execution vulnerability. If exploited, this vulnerability would allow an authenticated user to abuse the service, resulting in remote code execution.
Reported by Piotr Bazydlo (@chudypb) of Trend Micro Zero Day Initiative. No mention of exploitation.
EDIT: Piotr states that CVE-2024-28991 can be chained with CVE-2024-28990 (6.3 medium) SolarWinds Access Rights Manager (ARM) Hardcoded Credentials Authentication Bypass Vulnerability for pre-authenticated remote code execution.
Prof. Emily M. Bender(she/her)
emilymbender@dair-community.socialI talk to the press largely to *combat* AI hype. It's beyond frustrating to be misquoted in ways that contribute to it instead.
New newsletter post:
https://buttondown.com/maiht3k/archive/correcting-the-record/
buherator
buheratorDavid Weston (DWIZZZLE)
dwizzzlemsft@bird.makeupThis is cool. We ported parts of the Windows MDM stack (used by Intune) to Linux!! Now you can use it to EASILY control the configuration and security posture of Linux VMs in Azure.
https://learn.microsoft.com/en-us/azure/osconfig/quickstart-sec-baseline-mc?tabs=azure-cli
The Verge
verge@bird.makeupMicrosoft is building new Windows security features to prevent another CrowdStrike https://trib.al/otEVx6r
Viss
Viss@mastodon.socialI FOUND IT.
it took nearly four hours, but i found it.
thank you for coming along with me into the mines of my twitter archive to find this gif. dropbox deleted this, and many others when they 'just decided' to delete all locally stored files, making all the stuff you had exist only in the cloud.
i fired them for this, and replaced them with synology drive, that I sync over wireguard.
Lukas Beran
lukasberancz@infosec.exchangeYou asked, and we delivered! Check out the new Microsoft Incident Response Ninja Hub for a compilation of the research and guides that the Microsoft IR team has developed over the years on threat hunting, case studies, and more.
gergelykalman
gergelykalman@infosec.exchangeFor those of you who might like it: Here are the slides from my Alligatorcon talk:
https://gergelykalman.com/the-forgotten-art-of-filesystem-magic-alligatorcon-2024-slides.html
Ryan Baumann
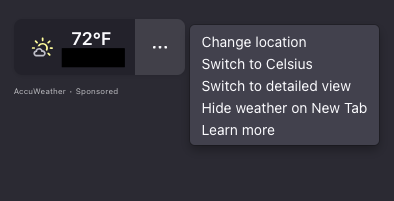
ryanfb@digipres.clubMozilla, reading the room extremely well, seemingly just recently flipped the switch to enable-by-default sponsored weather results from AccuWeather in every new Firefox tab you open. Clicking "Learn more" takes you here, with zero information on if your location is sent to AccuWeather every time you open a new tab: https://support.mozilla.org/en-US/kb/customize-items-on-firefox-new-tab-page
Probably only noticed because I normally have a blank new tab page but this showed up after updating Firefox!
buherator
buheratorhttps://www.crowdfense.com/windows-wi-fi-driver-rce-vulnerability-cve-2024-30078/
buherator
buheratorhttps://blogs.windows.com/windowsexperience/2024/09/12/taking-steps-that-drive-resiliency-and-security-for-windows-customers/?s=09
screaminggoat
screaminggoat@infosec.exchangeCISA: Vulnerability Summary for the Week of September 2, 2024
Sometimes I check the summary for hidden gems. This time, five of the Mozilla Firefox CVEs are CVSSv3.1: 9.8 critical
- CVE-2024-8381 type confusion
- CVE-2024-8384 memory corruption
- CVE-2024-8385 type confusion
- CVE-2024-8387 memory corruption
- CVE-2024-8389 memory corruption
At a glance, they're obviously high severity. It's just that you won't have that sense of urgency at the time of announcement because you didn't see the CVSS score, or understand the impact.
Let's not forget to mention Hall of Shame Progress Software for having LoadMaster vulnerability CVE-2024-7591 with a perfect 10.0 🥳